-
Disaster Recovery Plan Testing Best Practices 2024
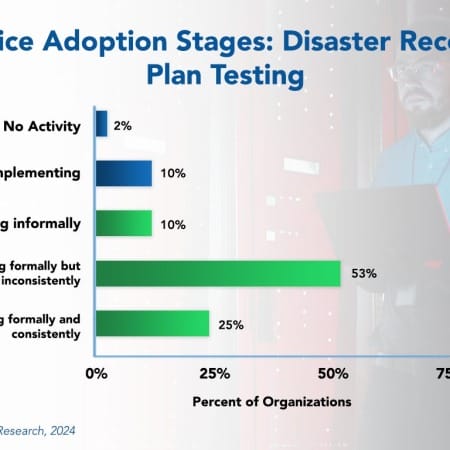
In today’s unpredictable business environment, there is an increasing reliance on data and digital systems to operate efficiently. With this comes the need for robust disaster recovery (DR) plans and testing to reduce the impact of unforeseen events. The effectiveness of a DR plan can only be truly validated through routine testing. However, while this practice is growing, few organizations are testing their DR plans formally and consistently. This Research Byte summarizes our full report on disaster recovery plan testing as a best practice.
January, 2024
-
DevOps Best Practices 2024
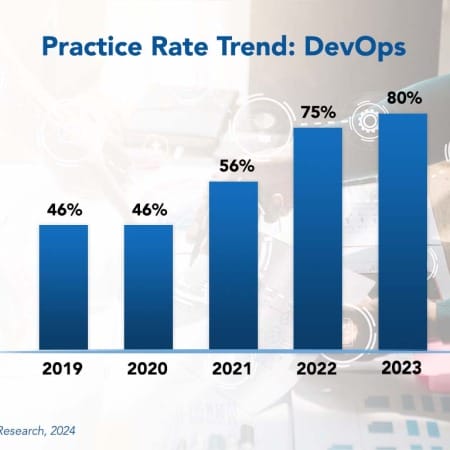
Development operations (DevOps) is an organizational model that promotes collaboration between software developers and IT operations. The model allows for frequent deployment of systemic changes and includes a use for automation. DevOps is a natural extension of agile development into the deployment and operational phases of the systems life cycle. Just as agile development builds software in small, iterative build cycles, DevOps applies enhancements as small incremental changes committed daily, hourly, or even moment-by-moment into the production system.
February, 2024
-
Agile Development Best Practices 2024
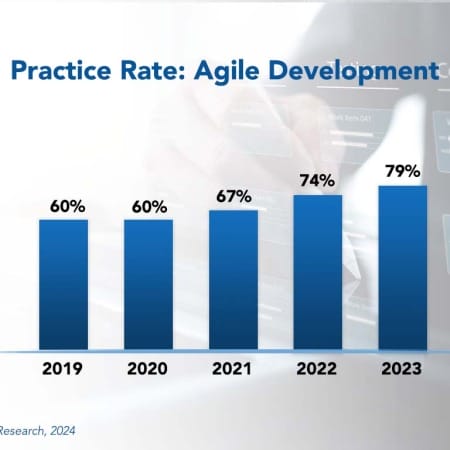
SaaS and packaged solutions are incredibly valuable. They help save time and resources in developing and maintaining applications for common back-office processes such as payroll, accounting, ERP, and CRM.
February, 2024
-
Website Accessibility Best Practices 2024
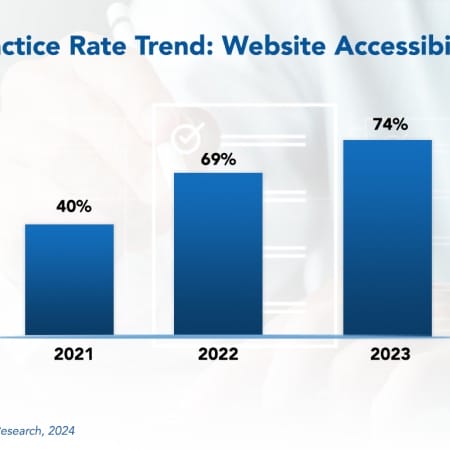
Website accessibility means building and maintaining websites that anyone can use comfortably and effectively.
February, 2024
-
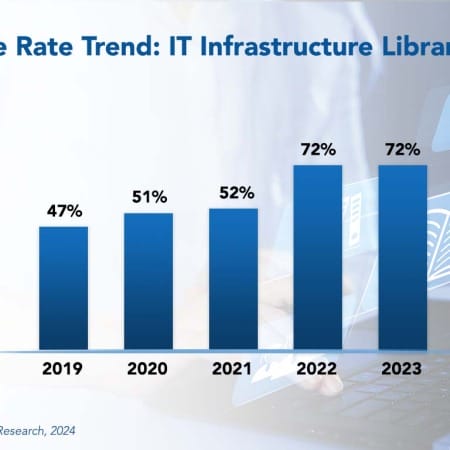
ITIL Best Practices 2024
The Information Technology Infrastructure Library (ITIL) is a framework of best practices and processes designed to assist businesses in supporting, delivering, and improving their IT services. The primary goal of ITIL is to ensure that IT services align with business objectives and customer needs. Frequently adopted ITIL processes include incident management, change management, and problem management.
March, 2024
-
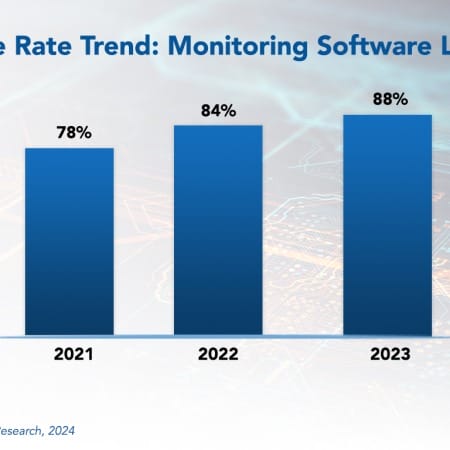
Monitoring Software Licenses Best Practices 2024
The art of monitoring software licenses is crucial in today’s software-driven world. Enterprises that depend on software must engage in effective license management for cost optimization, compliance assurance, and gaining a competitive edge. It is no longer just a box that needs to be checked.
March, 2024
-
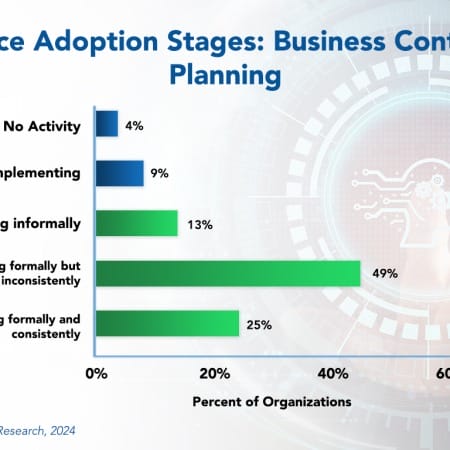
Business Continuity Planning Best Practices 2024
In today’s business landscape, virtually every organization relies heavily on information technology. Therefore, restoring information systems in the event of a disaster is an essential element of risk management, not just IT. At the same time, having IT systems recovered without restoring business operations is of little value. As such, a thorough business continuity plan goes beyond IT recovery, ensuring the overall survival of the business amid disruptions and re-establishing key business functions. Effective continuity planning should also address the potential loss of key individuals, disruption of customer or supplier operations, and failure of logistics providers.
March, 2024
-
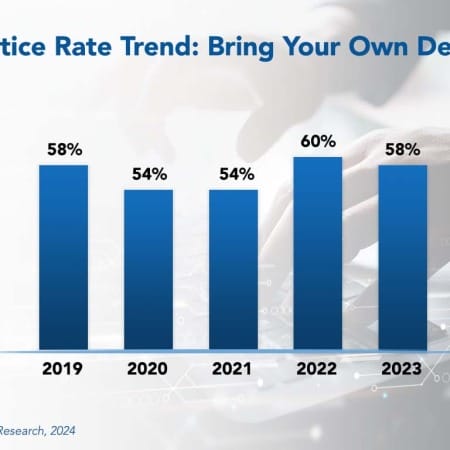
Bring Your Own Device Best Practices 2024
When iOS and Android smartphones were widely available in the late 2000s, bringing your own device for work-related tasks became popular. Employees generally favored their devices over those issued by the company, because it was simpler not to carry two devices. This trend drove companies to develop rules and regulations to control the practice.
March, 2024
-
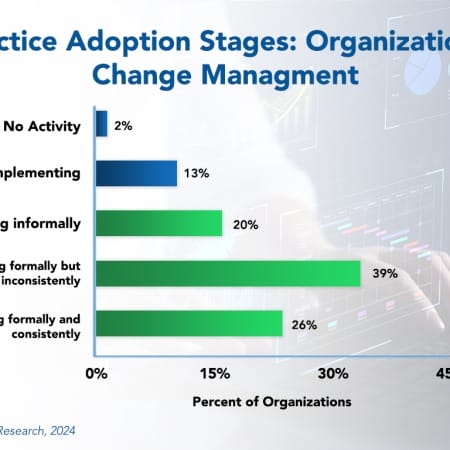
Organizational Change Management Best Practices 2024
The pace of change in many companies is increasing as new technologies allow businesses to serve customers faster, better, and cost-effectively. In most industries, therefore, new systems are essential to compete in today’s global economy. Still, some companies fall behind in formal and consistent practice of change management best practices. These best practices can help them leverage these new systems more effectively. IT leaders are not as resistant to change as they once were, but inadequate training and support, unrealistic expectations, or a lack of governance and strategic leadership might hinder them.
March, 2024
-
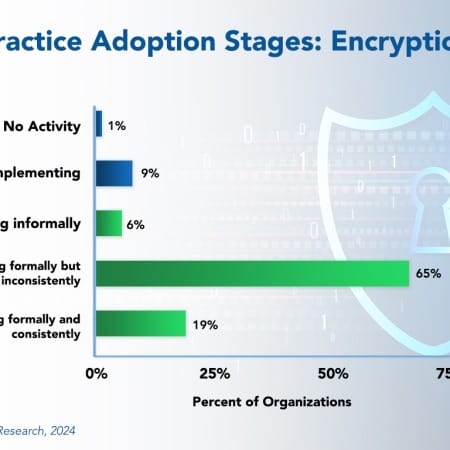
Encryption Best Practices 2024
Encryption best practices protect sensitive or confidential information, both in storage and in transit. Data encryption software and algorithms translate data into another form or code so that only those with access to a secret key—a decryption key—can read it. Banking details, health records, financial information, or other sensitive personal information must be encrypted so it cannot be intercepted, accessed, or read.
March, 2024
-
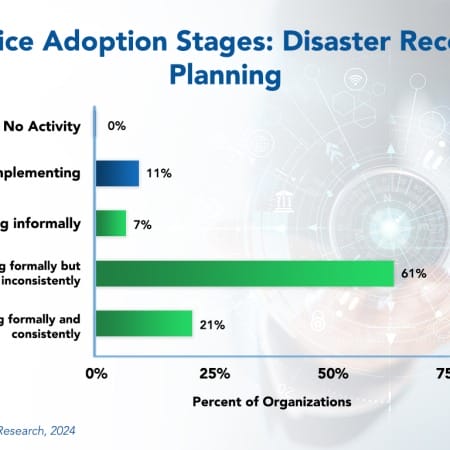
Disaster Recovery Planning Best Practices 2024
In 2021, a ransomware attack on Colonial Pipeline, a major fuel supplier in the US, forced the company to shut down operations for several days. This resulted in gasoline shortages and price hikes on the East Coast. Several airline companies in Britain experienced major IT failures in 2023, which resulted in thousands of canceled flights and an estimated $128 million in lost revenue. As these and numerous other examples show, the business impact of a disaster affecting the IT function can be enormous. The ability to recover information systems and data quickly and effectively after a disaster, cyberattack, or system failure should be an organizational priority. However, not many companies are consistently planning for disaster recovery.
April, 2024
-

Clinical Services Business Process Transformation 2023 Market Insights™
The Clinical Services Business Process Transformation 2023 Market Insights™ assists organizations in identifying important demand-side trends that are expected to have a long-term impact on any clinical services project. The report also highlights key challenges that enterprises face today.
May, 2023
-
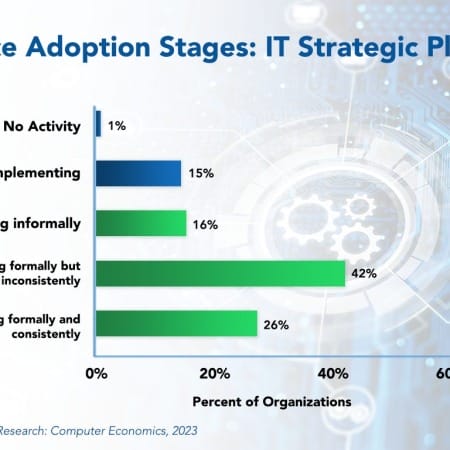
IT Strategic Planning Best Practices 2023
With digital transformation well underway, organizations of all sizes and across multiple industry sectors are increasingly viewing information technology as essential in supporting business strategy. Organizations in these sectors face digital disruption, and it is difficult to see how they can respond without an IT strategic plan.
September, 2023
-
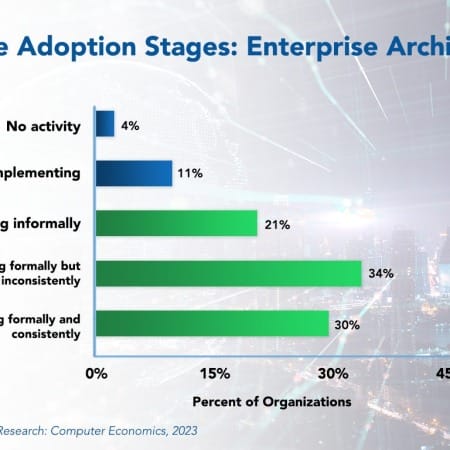
Enterprise Architecture Adoption and Best Practices 2023
While large IT project failures generate headlines, an even larger risk may be the incoherence that comes from developing new systems and capabilities without an overall plan. Enterprise architecture is an IT best practice that provides a description of the organization in its desired state. This allows developers to build an infrastructure, data model, systems, and process that are aligned with that organizational architecture.
October, 2023
-
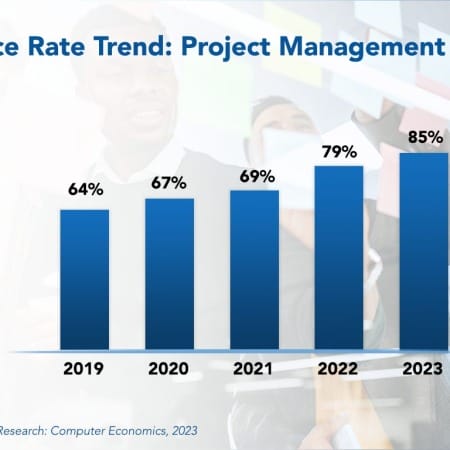
Project Management Office Best Practices 2023
To improve project success, companies often establish a formal project management office (PMO) as a center of excellence for project management disciplines. In some organizations, the PMO operates as an advisory group to project managers, who report directly to business units. In other organizations, project managers report directly to the PMO and are assigned to projects as needed. However, in recent years, the use of PMOs has grown significantly, especially for organizations that use them for all projects.
December, 2023

 Grid View
Grid View List View
List View