-
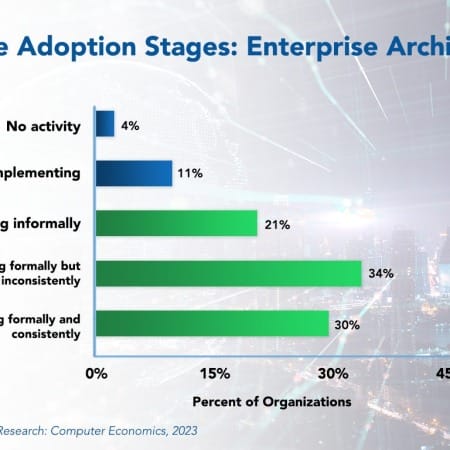
Enterprise Architecture Adoption and Best Practices 2023
While large IT project failures generate headlines, an even larger risk may be the incoherence that comes from developing new systems and capabilities without an overall plan. Enterprise architecture is an IT best practice that provides a description of the organization in its desired state. This allows developers to build an infrastructure, data model, systems, and process that are aligned with that organizational architecture.
October, 2023
-
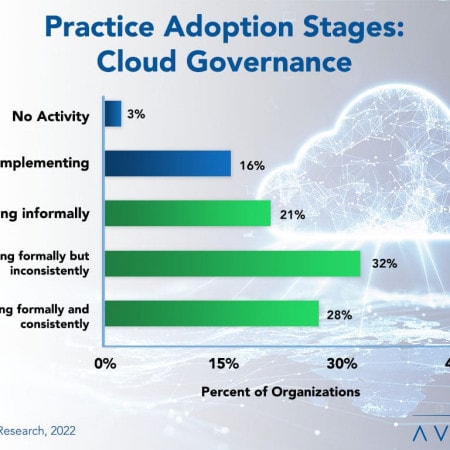
Cloud Governance Best Practices 2022
Cloud governance is a set of policies and practices governing an organization’s use of cloud computing to enable new capabilities and optimize cloud cost, scalability, security, compliance, and interoperability. Cloud governance should be top of mind for several organizations because it provides a complete overview of an organization’s cloud resources and how they should be managed. It is not surprising that many organizations see the vital role cloud governance plays in their daily operations, and practice rates are high compared with most best practices in our annual study.
November, 2022
-
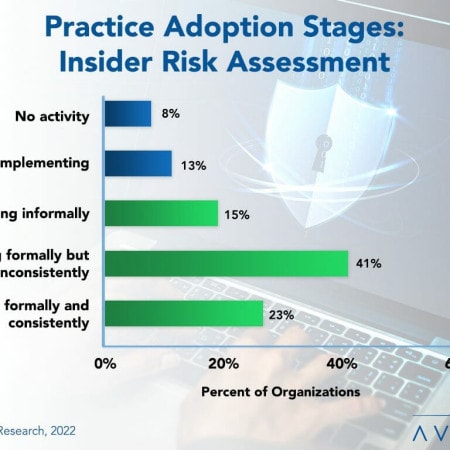
Insider Security Risk Assessment Best Practices 2022
Most organizations are aware of the IT security threats posed by outsiders. Countermeasures such as firewalls, antivirus software, and intrusion detection systems are all aimed at these threats. Yet these measures do little to counter insider threats within the organization.
September, 2022
-

IT Vendor Governance Best Practices
IT vendor management is a function and set of practices that guide the selection, management, and assessment of IT suppliers to ensure that all parties comply with the terms of their contracts. IT supplier management has been a best practice for many years, but the disciplines have evolved. Traditional IT vendor governance practices are now inadequate to navigate the changing business ecosystem. The upshot is that most organizations need to transform their vendor governance programs. This Research Byte summarizes our full report on IT Vendor Governance Best Practices.
August, 2022
-
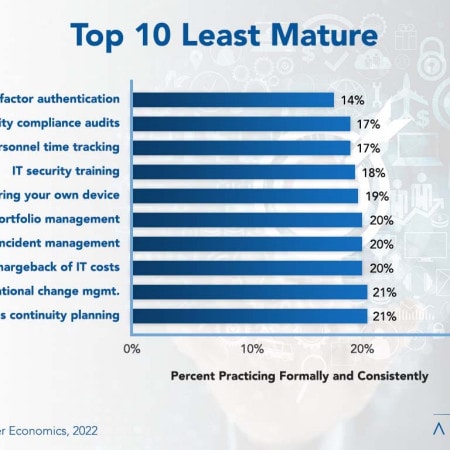
IT Management Best Practices 2022
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 33 IT management practices, which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices. (196 pp., 178 figs.)
March, 2022
-
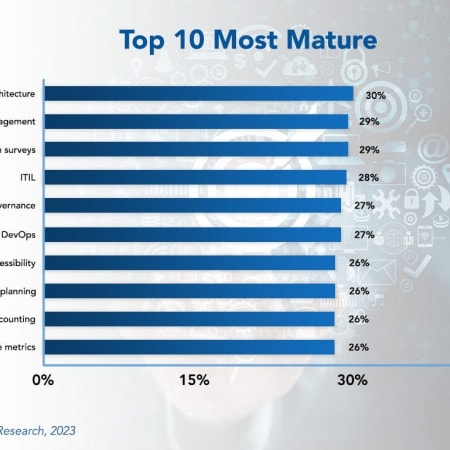
IT Management Best Practices 2023
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 35 IT management practices, which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices.
March, 2023
-
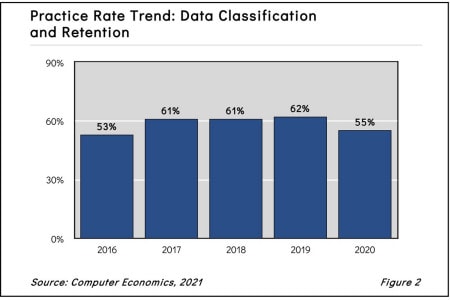
Data Classification and Retention Adoption and Best Practices 2021
Creating a formal classification scheme is an important element in managing data for security, disaster recovery, and retention purposes. Yet, many organizations—even those that profess a commitment to protecting corporate and customer information—fail to implement data classification. This report begins by defining data classification and retention. We next study the adoption and practice levels and examine those by organization size and sector. We conclude with best-practice recommendations.
July, 2021
-

Website Accessibility Adoption and Best Practices 2021
Website accessibility is a best practice requiring the use of inclusive website design to facilitate use by people with disabilities, including visual, hearing, motor skills, or cognitive impairment. When this practice is followed formally and consistently, the experience is improved for people with disabilities who can better understand, navigate, and interact with an organization’s websites. In this report, we study the adoption and practice levels for website accessibility and examine those by organization size and sector. We conclude with practical recommendations for getting started with website accessibility.
August, 2021
-
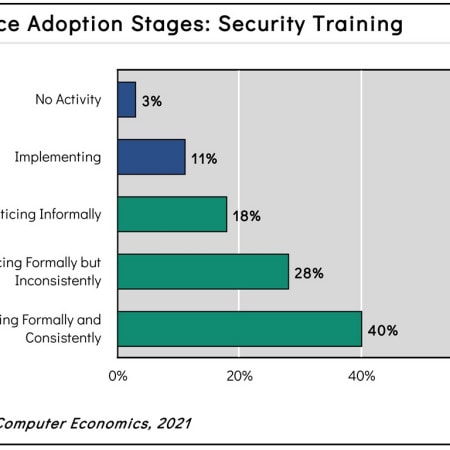
Security Training Adoption and Best Practices 2021
Security training is a business best practice that involves the training of all IT and user personnel in a company’s security policies, procedures, and best practices to increase awareness and ensure compliance. It is a highly advisable practice for every organization. Many companies report the existence of security training, yet there is ample room for improvement. This report begins by defining security training and summarizing the main types of training available. We next study the adoption and practice levels and examine those by organization size and sector. We conclude with best-practice recommendations.
April, 2021
-
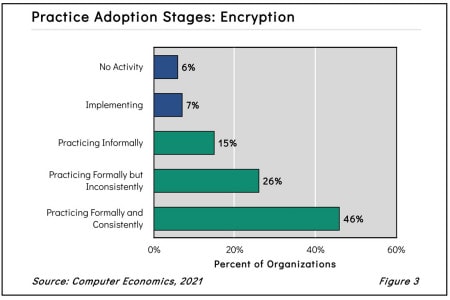
Encryption Adoption and Best Practices 2021
Encryption is a best practice for protecting sensitive or confidential information, both in storage and in transit. Data encryption software and algorithms translate data into another form, or code, so that only someone with access to a secret key—a decryption key—can read it. It has a high maturity rating, but there is ample room for improvement. This report begins with a definition of encryption. We next study the adoption and practice levels and examine those by organization size and sector. We conclude with best-practice recommendations.
February, 2021
-
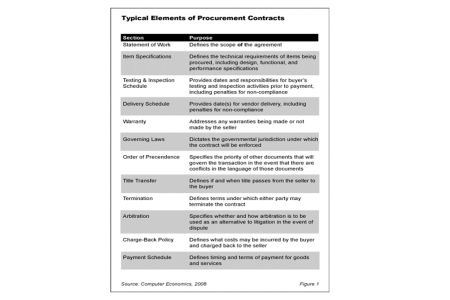
How to Evaluate IT Procurement Contracts
This report serves as a primer on IT procurement contracts. Our focus is primarily on contracts for IT services, though the principles apply to any type of IT procurement. We explain the typical elements of an IT procurement contract and the major types of contracts, including various types of fixed-price and cost-reimbursable agreements.
November, 2008
-
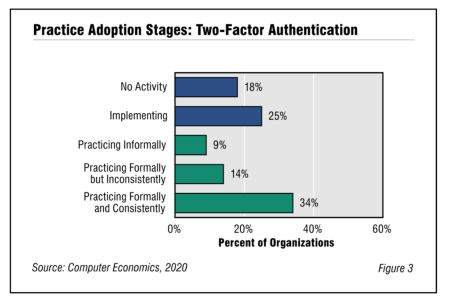
Two-Factor Authentication Adoption and Best Practices 2020
Two-factor authentication is an IT security best practice that provides an extra layer of protection for system access. It is a highly advisable security measure, but our annual survey of IT management best practices shows that not enough companies use it formally and consistently. This report begins with a brief explanation of two-factor authentication.
February, 2020
-
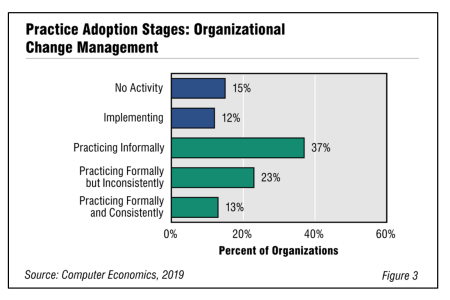
Organizational Change Management Adoption and Best Practices 2019
New system projects often fail, not because of problems with the technology but because the new systems are not fully embraced by the workforce. Fortunately, there are formal methodologies that business and IT leaders can apply to establish and carry out an organizational change management program. In this report, we look at adoption trends and maturity of organizational change management by organization size and sector.
March, 2019
-
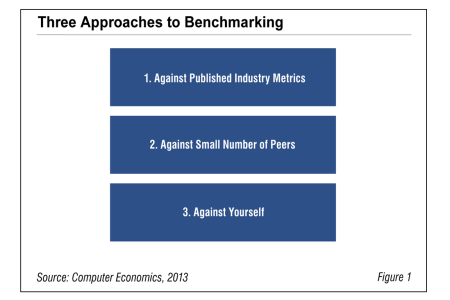
Best Practices for Benchmarking IT Budget Ratios
Benchmarking is a popular way for IT organizations to justify their IT budgets and better focus their efforts toward continuous improvement. But without following certain principles, business leaders will likely question the validity of the outcome. This report, based on many years of benchmarking exercises at Computer Economics, outlines three complementary approaches to benchmarking.
February, 2013
-
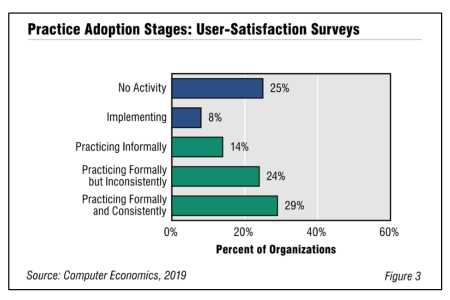
User-Satisfaction Surveys and IT Performance Metrics Adoption and Best Practices 2019
Periodic surveys of user satisfaction are one way to measure how well an IT organization is delivering services, resolving issues, and managing perceptions. If user satisfaction is falling, it may mean that the service desk is understaffed or change requests are not being accommodated. At the same time, collecting data on service levels can be useful for tracking and monitoring performance in a service organization. But taking the next step and publishing the performance metrics for the community can be even more useful. In this report, we look at the maturity of surveying user satisfaction and publishing IT performance metrics.
July, 2019

 Grid View
Grid View List View
List View