-
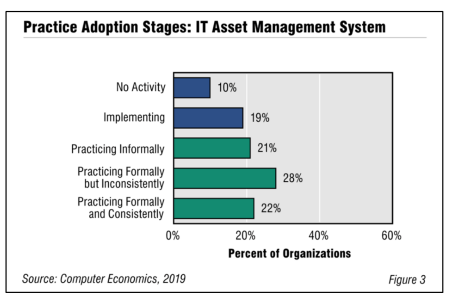
IT Asset Management Adoption and Best Practices 2019
IT organizations often find it difficult to track all of the information about IT assets, such as hardware and software licenses, along with critical data such as location, configuration, and renewal dates. In response, companies have worked to set up IT asset management and configuration management systems, and processes to bring IT assets into a common management framework. In this report, we describe why IT asset management is an important process and the challenges it faces.
August, 2019
-
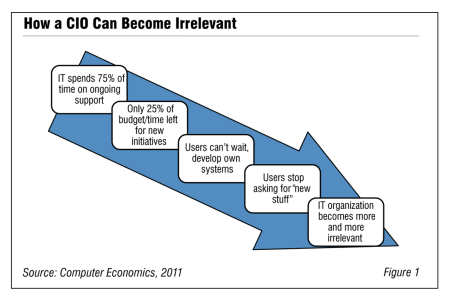
Elevating the Role of the CIO
CIOs are being asked to expand their role to support business change and innovation while they are struggling with maintaining aging infrastructure and declining resources. This report provides guidance for CIOs on how to elevate their role within the organization to one that has a meaningful influence on meeting strategic business objectives.
December, 2011
-
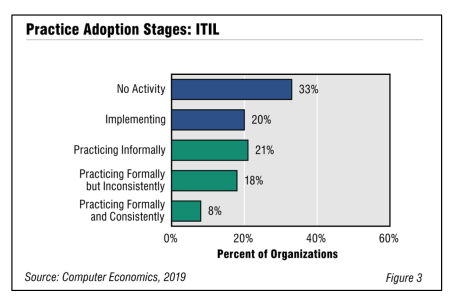
Information Technology Infrastructure Library Adoption and Best Practices 2019
Although large IT organizations are continuing to embrace the Information Technology Infrastructure Library (ITIL), the number of organizations committed to full ITIL implementation remains relatively small. This report begins with a brief explanation of ITIL’s history and current framework for IT service management, including its relationship with new approaches to change management, such as DevOps.
April, 2019
-
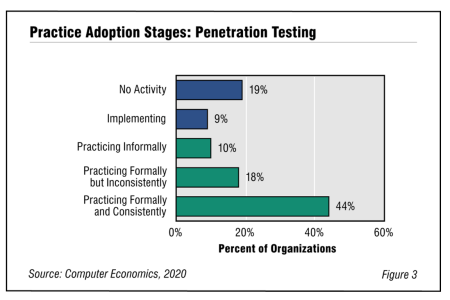
Penetration Testing Adoption and Best Practices 2020
Penetration testing is an important element of IT security best practices. However, by itself, penetration testing is insufficient. It needs to be part of a robust and iterative process, in combination with the other security best practices to make it a formidable defensive weapon. In this report, we look at the maturity of penetration testing as an IT discipline. We assess current adoption trends by organization size and sector.
February, 2020
-
Agile Development Adoption and Best Practices 2020
After more than two decades of maturation, agile development methodologies promise to deliver new systems more quickly, improve software quality, and increase user satisfaction. While adoption remains only moderate in corporate IT groups, agile development continues to gain adherents as organizations seek to respond to a continuously changing environment. In this study, we report how widely and deeply agile development is being embraced by IT groups today, by organization size and sector.
March, 2020
-

IT Management Best Practices 2020-2021
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 34 IT management practices.
October, 2020
-
Avoiding Technical Bankruptcy in Legacy Systems
Technical debt is a term that describes the consequences of a system that has become out of date because of accrued unapplied updates. But if an organization continues to take on technical debt, the system becomes a true legacy system, falling into a state we describe as “technical bankruptcy.” In this report, we identify the symptoms of technical bankruptcy and the devastating effects that it has on the organization.
March, 2017
-

IT Management Best Practices 2019/2020
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 34 IT management practices which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices. (197 pp., 178 figs.) [Full Report Description and Sample Pages] [Research Byte]
September, 2019
-

IT Strategic Planning Adoption and Best Practices
IT strategic planning is essential when the economy is good, as well when facing headwinds. The strategic road map can help an IT organization look beyond the pressures of quarter-to-quarter performance and stay focused on long-term goals, such as corporate growth and expansion, and guide it through periods of technology change. A strategic plan is also needed when major programs, such as an overhaul of legacy systems, require a long-term commitment beyond the current budget year. In this study, we describe the fundamental components of IT strategic planning, and assess current adoption trends by organization size and sector. We conclude with areas that should be addressed in the strategic IT road map. (17 pp., 6 pg.) [Research Byte]
December, 2018
-

IT Security Policies Adoption and Best Practices
Nearly every IT organization has security policies to some extent, but there is often much room for improvement. The fact that so many companies have IT security policies that are not formally established, comprehensive in their scope, or followed consistently is part of the reason that we continue to see little progress against high-profile cyberattacks. In this report, we look at adoption trends and maturity of IT security policies by organization size and sector. We conclude with practical recommendations for IT organizations interested improving their IT security policies. (17 pp., 6 figs.) [Research Byte]
October, 2018
-

IT Management Best Practices 2018/2019
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 35 IT management practices which we have grouped into six major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, application development practices, and innovation best practices. (207 pp., 184 figs.) [Full Report Description and Sample Pages] [Research Byte]
September, 2018
-

DevOps Adoption and Best Practices
DevOps, a combination of the words “development” and “operations,” is an organizational model with a set of processes and tools that promote collaboration between software developers and IT operations, allowing frequent deployment of system changes. As an extension of agile development, DevOps is gaining traction, although it still has limited adoption in corporate IT environments. In this report, we look at adoption trends and maturity of DevOps by organization size and sector. We conclude with practical recommendations for IT organizations interested in getting started with DevOps. (15 pp., 6 figs.) [Research Byte]
August, 2018
-

IT Personnel Time Tracking Adoption and Best Practices
Personnel accounts for more than 40% of the typical IT operational budget. Therefore, properly allocating personnel time and expenses to projects, tasks, or service delivery is vital for managing IT costs and pricing IT services. Nevertheless, a surprising number of organizations do not keep track of where IT personnel are spending their time. In this report, we look at adoption trends for IT personnel time tracking by organization size and sector. We also discuss the benefits of tracking IT personnel time along with recommendations for making time tracking effective. (15 pp., 6 fig.) [Research Byte]
April, 2018
-

Business Continuity Planning Adoption and Best Practices
A comprehensive business continuity plan is one that ensures that the business itself will survive in the event of a disruption, with key business functions re-established. Nevertheless, far too few business leaders understand the importance of this exercise. In this report, we define what a business continuity plan should contain and look at adoption trends by organization size and sector. We also discuss the steps that IT leaders should take to create and maintain a business continuity plan. (16 pp., 6 fig.) [Research Byte]
April, 2018
-

Post-Implementation Audits Adoption and Best Practices
Implementing a new software system can be a risky endeavor. The project team might rightly celebrate after the implementation is complete, but it should be just the start of another phase of the system development life cycle: the post-implementation stage. A post-implementation audit should be conducted to determine what benefits have been achieved, what lessons can be learned, and what corrective actions should be taken to ensure maximum success with the new system. In this report, we look at adoption trends for post-implementation audits by organization size and sector. We also discuss best practices in conducting post-implementation audits. (15 pp., 6 fig.) [Research Byte]
March, 2018

 Grid View
Grid View List View
List View