Paralleling the popularity of portable computers, Wi-Fi has been gaining enthusiastic supporters among business users. The recently completed Computer Economics 2005/2006 Information Systems Spending and Technology Trends study, shows how widespread the use of Wi-Fi technology has become. This annual study, now in its 16th year, is based on surveys with approximately 200 IT managers and executives across every major industry sector, as well as state and local government agencies.
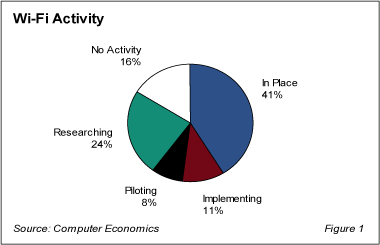
As Figure 1 indicates, Wi-Fi networks are in use at 41% of the data centers surveyed for our annual study. Another 11% are implementing Wi-Fi, and the 32% of sites that are either piloting or researching wireless technology points toward increased usage in the future.
Furthermore, the economics behind wireless networks are excellent, with favorable ROI reported by the vast majority of data centers, and most reporting TCO to be the same as or less than expected.
Although the financial aspects of Wi-Fi investments are favorable, full realization of these benefits must include consideration of the system and information security risks that exist if the technology is not implemented correctly. Technical security problems inherent in the original WEP security standard have been eliminated by WPA security, and the emerging 802.11i standard, otherwise known as WPA2, further strengthens protection of wireless networks with the use of the Advanced Encryption Standard (AES). However, these security advances will mean nothing if end-users do not practice safe-computing when using wireless networking.
For example, users that are issued portable computers with Wi-Fi capabilities must understand that if they connect to an unsecured wireless network—for example, in an airport, coffee shop, or hotel—it is possible for hackers or other malicious parties to intercept their network traffic. Some hackers have gone so far as to set up counterfeit access points in public places as a way of gaining access to the computers of unsuspecting wireless users. Although there have not yet been a great number of reports of security incidents related to such ploys, known as “evil twins,†it is likely that such incidents will increase in the future. Security measures to thwart such tactics are possible, but they must be planned for and implemented by IS organizations as part of an overall Wi-Fi security strategy. At a minimum, users should be given training to understand the risks and mitigation measures they should use when operating in wireless mode.
Computer Economics believes that Wi-Fi is a low risk investment as long as a security assessment and appropriate risk mitigation measures are included as part of the overall strategy for implementation. Such measures should include appropriate technical security as well as policies and procedures to ensure that users understand and consistently practice safe computing using wireless.
July 2005
Information for this Research Byte was taken from our recent report on this subject entitled, Wi-Fi Move Into Enterprise Computing. This report provides more detailed information regarding the current ROI and TCO of Wi-Fi deployments and also examines the current state of the technology from a security perspective. Clients can view this report for free, and non-clients can purchase it online via credit card, at following link: https://avasant.com/report/wi-fi-moves-into-enterprise-computing-2005/
Additionally, our newly released 2005/2006 Information Systems Spending and Technology Trends study provides detailed information on spending, staffing, and technology trends by specific industry sector.



