Latest Reports
-
![HR Process Transformation to Build an Employee-Centric Culture MoneyShot Global Hire to Retire BPT 2022–2023 - HR Process Transformation to Build an Employee-Centric Culture]()
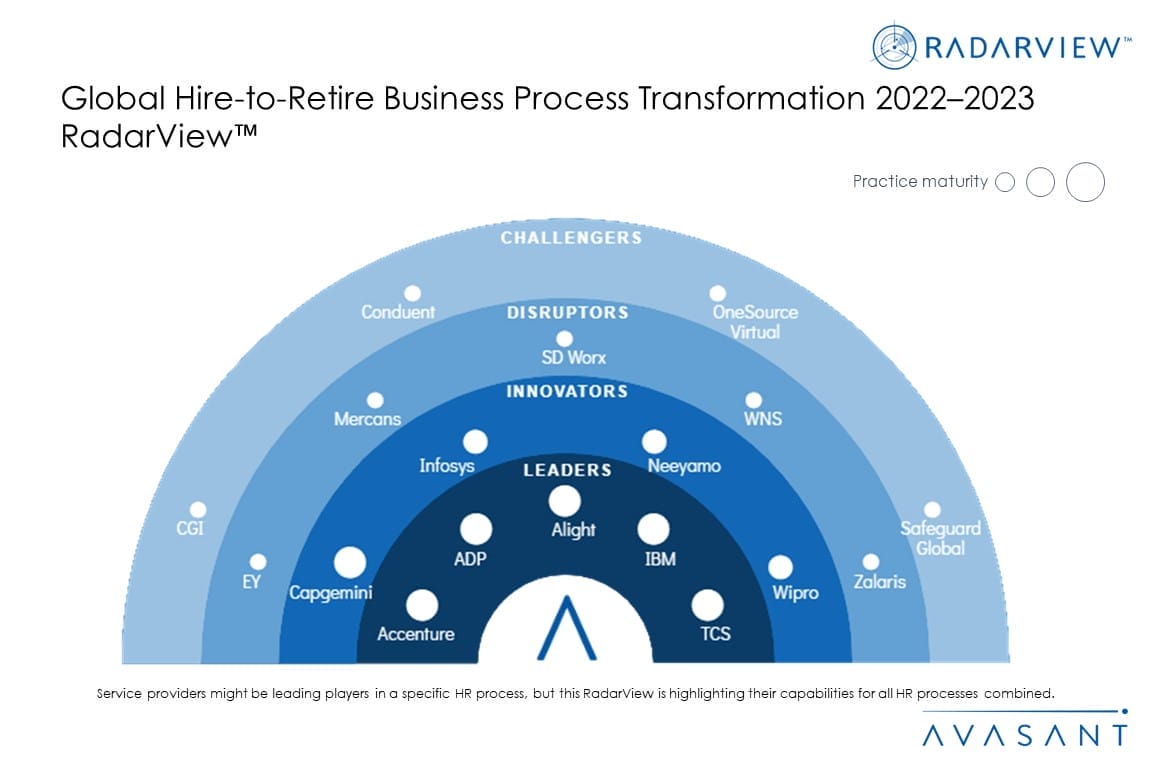
HR Process Transformation to Build an Employee-Centric Culture
The enterprise HR function has been traditionally concerned with reducing employee costs, managing employee transactions, and complying with local labor laws. However, with competition for talent and elevated employee expectations, the enterprise HR function is becoming more strategic with a focus on engaging employees. Enterprises are transforming their people, processes, and technology to meet these demands. As a result, service provider HR transformation clients grew by over 30% between September 2021 and September 2022. These trends, and others, are covered in our new Global Hire-to-Retire Business Process Transformation 2022–2023 RadarView™.
January, 2023
-
![Factors Affecting DBA Staffing Ratios Database Administration Staffing Ratios - Factors Affecting DBA Staffing Ratios]()
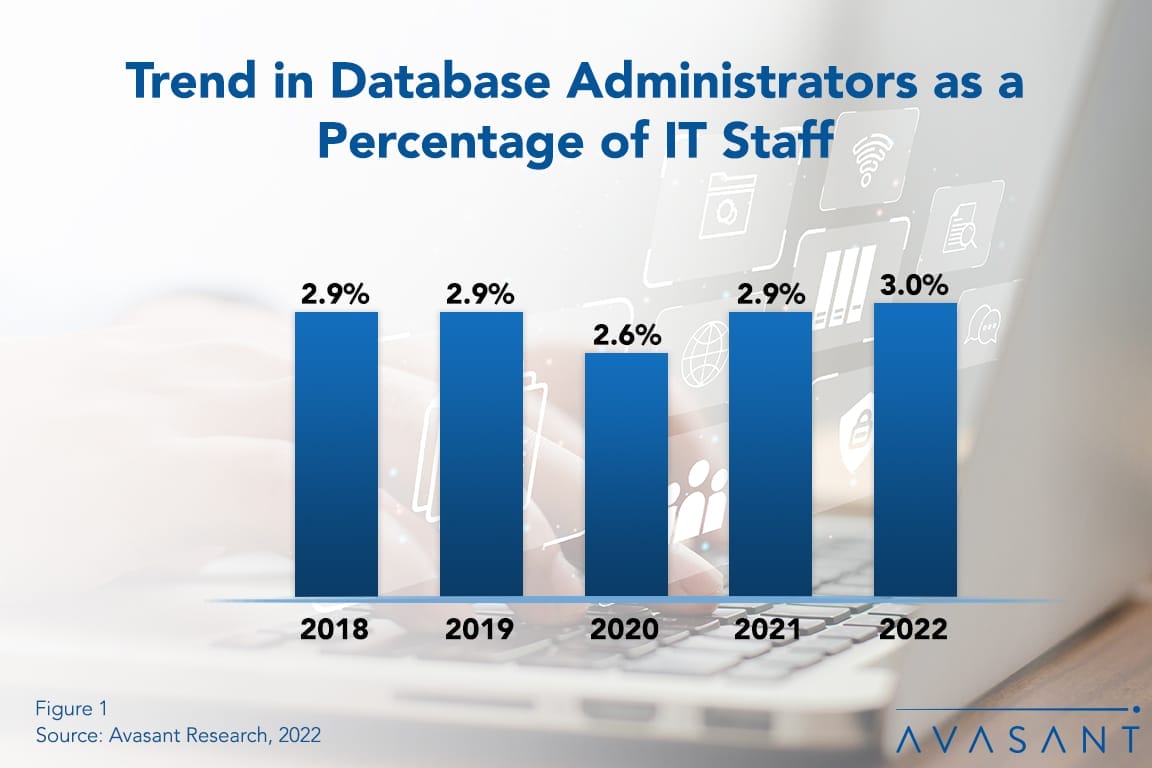
Factors Affecting DBA Staffing Ratios
Database administration (DBA) staffing remained steady in 2022, even though organizations are capturing and analyzing greater amounts of data. One reason DBA staffing levels are not rising is technology, specifically AI/ML, which is assisting DBAs in collecting, sorting, managing, and controlling ever-larger volumes of data. This Research Byte summarizes our full report on database administration staffing ratios.
January, 2023
-
![Finance and Accounting Outsourcing Driving Long-Term Business Value Money Shot FA Business Process Transformation 2022–2023 - Finance and Accounting Outsourcing Driving Long-Term Business Value]()
Finance and Accounting Outsourcing Driving Long-Term Business Value
Finance and accounting (F&A) outsourcing grew between 13% and 17% from June 2021 to June 2022. F&A outsourcing is expanding as enterprises entrust service providers with more strategic processes, such as tax and treasury. Additionally, companies want to deal with fewer service providers, leading to an increase in the number of multitower deals. For F&A outsourcing service providers combined, 50%–75% of their F&A revenue comes from providing end-to-end services, compared to function-specific projects. These trends are covered in Avasant’s F&A Business Process Transformation 2022–2023 RadarView™.
January, 2023
-
![Leveraging the Hybrid Cloud for Faster Time-to-Market MoneyShot Hybrid Enterprise Cloud Services 2022 2023 RadarView - Leveraging the Hybrid Cloud for Faster Time-to-Market]()
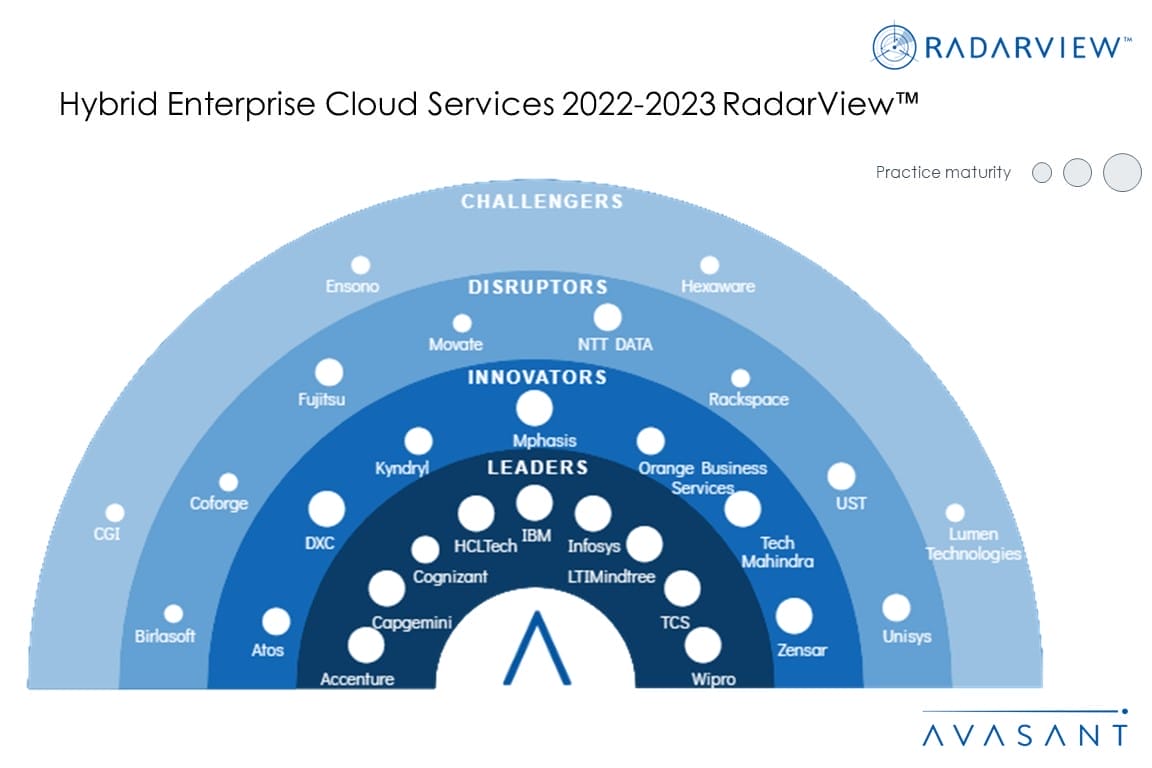
Leveraging the Hybrid Cloud for Faster Time-to-Market
Enterprises want to improve customer experience of their cloud-based solutions and applications, and they are looking for faster rollout of features and upgrades to deliver personalized products and services. They are leveraging hybrid cloud environments to quickly modify their applications according to client requirements while ensuring the stability and reliability of the underlying cloud infrastructure.
January, 2023
-
![Study: IT in PJs on the Rise Study IT in PJs on the Rise - Study: IT in PJs on the Rise]()
Study: IT in PJs on the Rise
In the aftermath of the pandemic, one thing appears to be here to stay: working from home. Today, a much higher percentage of IT personnel are working from home, compared to pre-pandemic numbers. Our annual IT salary study finds that almost half of IT workers now ply their trade from home.
December, 2022
-
![IT Wages to Rise 4.0% at the Median in 2023, Salary Study Finds RB IT Salary - IT Wages to Rise 4.0% at the Median in 2023, Salary Study Finds]()
IT Wages to Rise 4.0% at the Median in 2023, Salary Study Finds
With current high levels of inflation and relatively low levels of unemployment, we would expect IT salaries to be rising strongly. But in the IT job market right now, that is not the case. The job market is being influenced by a series of competing tensions, which will continue in ’23. This Research Byte summarizes the executive summary of our IT Salary Report 2023.
December, 2022
-
![Transforming the Utilities Industry Through Digital Technologies MoneyShot Utilities Digital Services 2022 2023 - Transforming the Utilities Industry Through Digital Technologies]()
Transforming the Utilities Industry Through Digital Technologies
Electric, gas, and water utilities are facing regulatory pressures. For example, governments expect gas and electric utilities to support global sustainability and energy transition goals. They also require water utilities to ensure water quality and availability. While an increasing number of electrical customers also become energy producers, their expectations have changed. Furthermore, utilities are facing growing challenges in terms of skilled worker shortages, high investment and maintenance costs, and heavy asset losses due to the rising number of natural disasters. To address these issues, utilities globally are investing in digital technologies to transform their day-to-day operations, enable predictive maintenance, reduce human dependency, automate repetitive and tedious tasks, and reduce costs. These emerging trends are covered in Avasant’s Utilities Digital Services 2022–2023 RadarView™.
December, 2022
-
![Hitachi Vantara Addresses the Data Elephant in the Room Hitachi RB 1 - Hitachi Vantara Addresses the Data Elephant in the Room]()
Hitachi Vantara Addresses the Data Elephant in the Room
Hitachi Vantara CEO Gajen Kandiah will be the first to admit it. Hitachi Vantara has struggled to get its identity across to the market. He compared the problem to the old proverb about blind men coming across an elephant. As one man grasps the trunk, he decides it is a snake. Another feels the elephant’s sides and decides he is touching a wall. Each of the men touch a different part of the elephant, and none see the big picture. If you want to know what the whole Hitachi Vantara elephant looks like, data is what holds together all of its parts.
December, 2022
-
![Global Disruptions Show Value of Cloud Infrastructure IaaS Adoption and Investment RB - Global Disruptions Show Value of Cloud Infrastructure]()
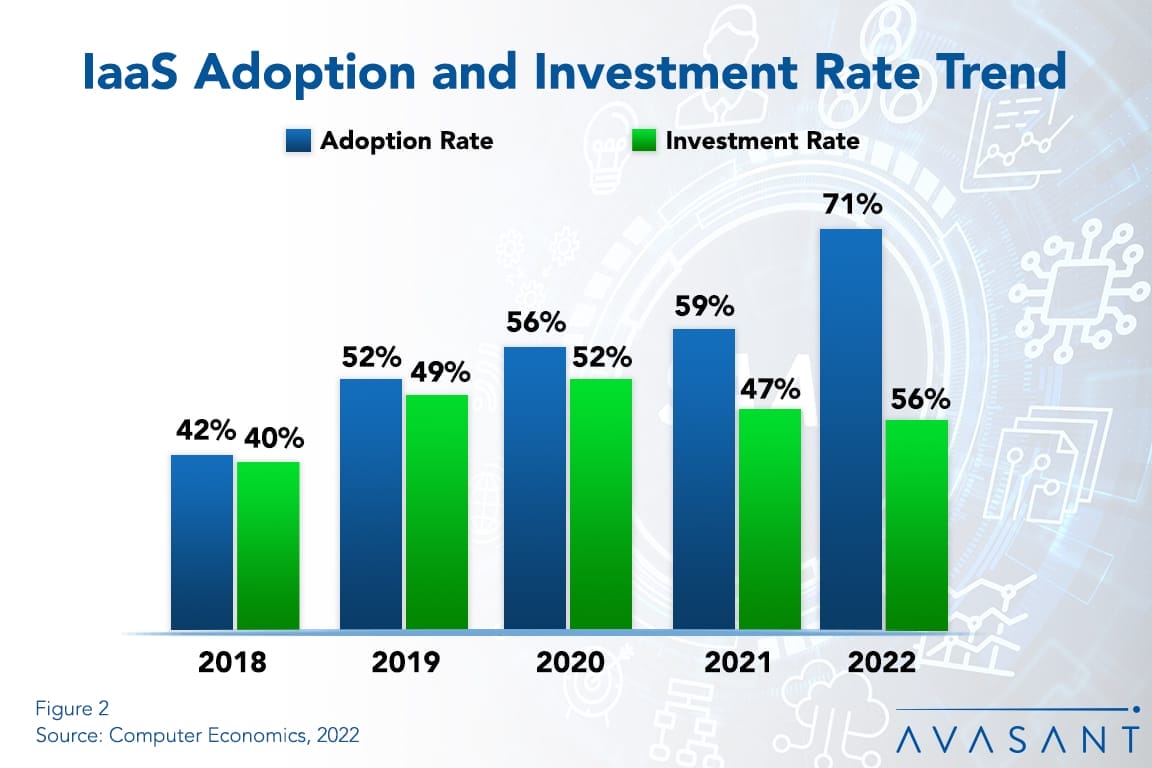
Global Disruptions Show Value of Cloud Infrastructure
The need for agility continues to drive investment in Infrastructure as a Service (IaaS). And the global pandemic and subsequent supply chain disruptions have only increased this trend. Cloud infrastructure makes it easier for companies to respond to fluctuations in demand, changes in business requirements, and the need to optimize costs over time. This Research Byte provides a summary of our full report on IaaS adoption trends and customer experience.
December, 2022
-
![Remote Work Presents New Challenges for Project Management Staffing IT Staffing RB Project Manager - Remote Work Presents New Challenges for Project Management Staffing]()
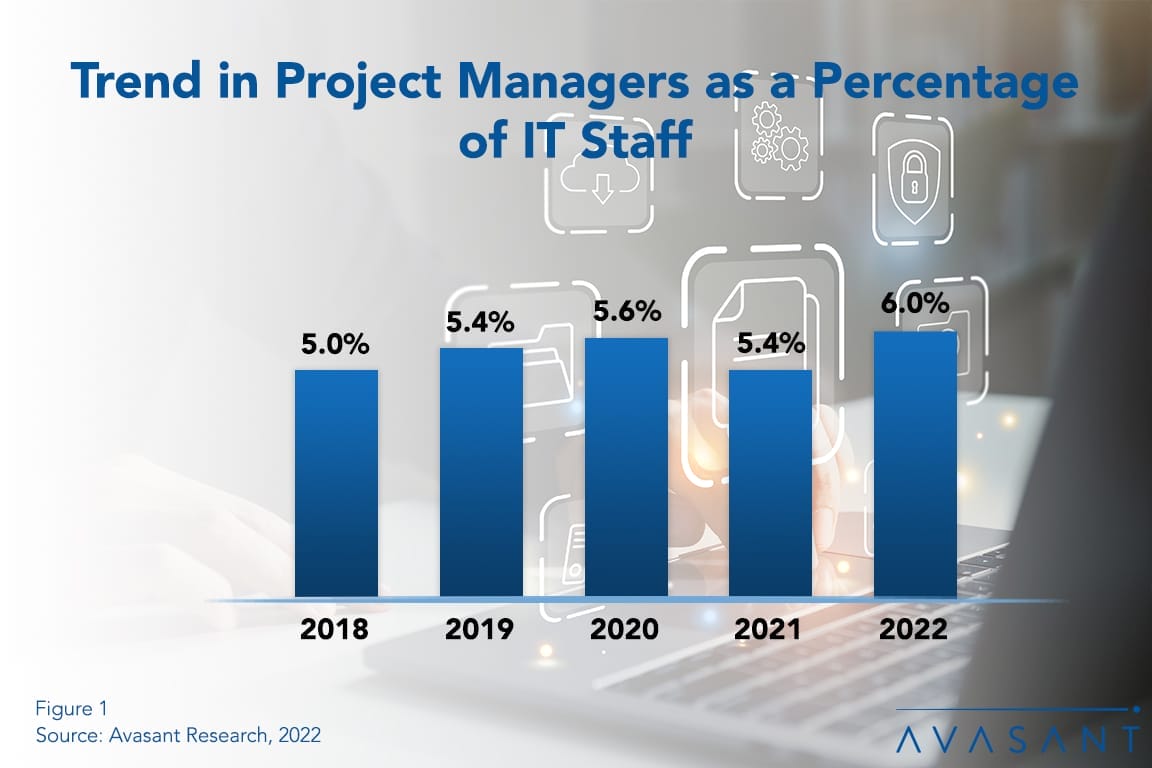
Remote Work Presents New Challenges for Project Management Staffing
The role of the IT project manager is critical in this dynamic, changing IT environment. The rise in the remote/hybrid work model puts project managers in the middle of recreating business and project management processes to reflect a more dispersed workforce. This Research Byte provides a summary of our full report on IT project management staffing ratios.
December, 2022
-
![Cloud Growth Requires Cloud Governance Practice Adopotion Stages Cloud Governanced - Cloud Growth Requires Cloud Governance]()
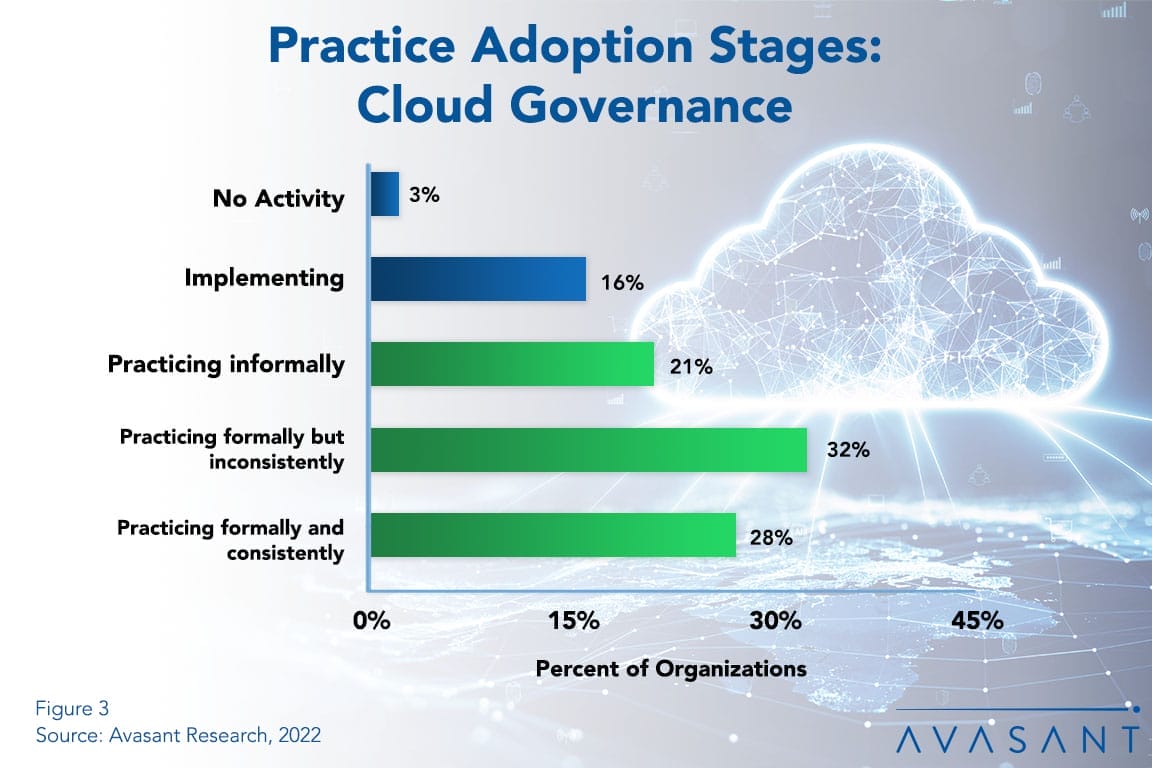
Cloud Growth Requires Cloud Governance
With the continued migration to the cloud, governance becomes even more critical. Cloud governance provides a complete overview of an organization’s cloud resources and how they should be managed. Therefore, it is not surprising that many organizations see the vital role cloud governance plays in their daily operations, and practice rates are high compared to most best practices in our annual best practices study. This Research Byte summarizes our full report on Cloud Governance Best Practices.
November, 2022
-
![Intelligent Process Mining: Delivering Complex Business Intelligence and Process Transparency MoneyShot Intelligent Process Mining Platforms 2022 2023 RadarView - Intelligent Process Mining: Delivering Complex Business Intelligence and Process Transparency]()
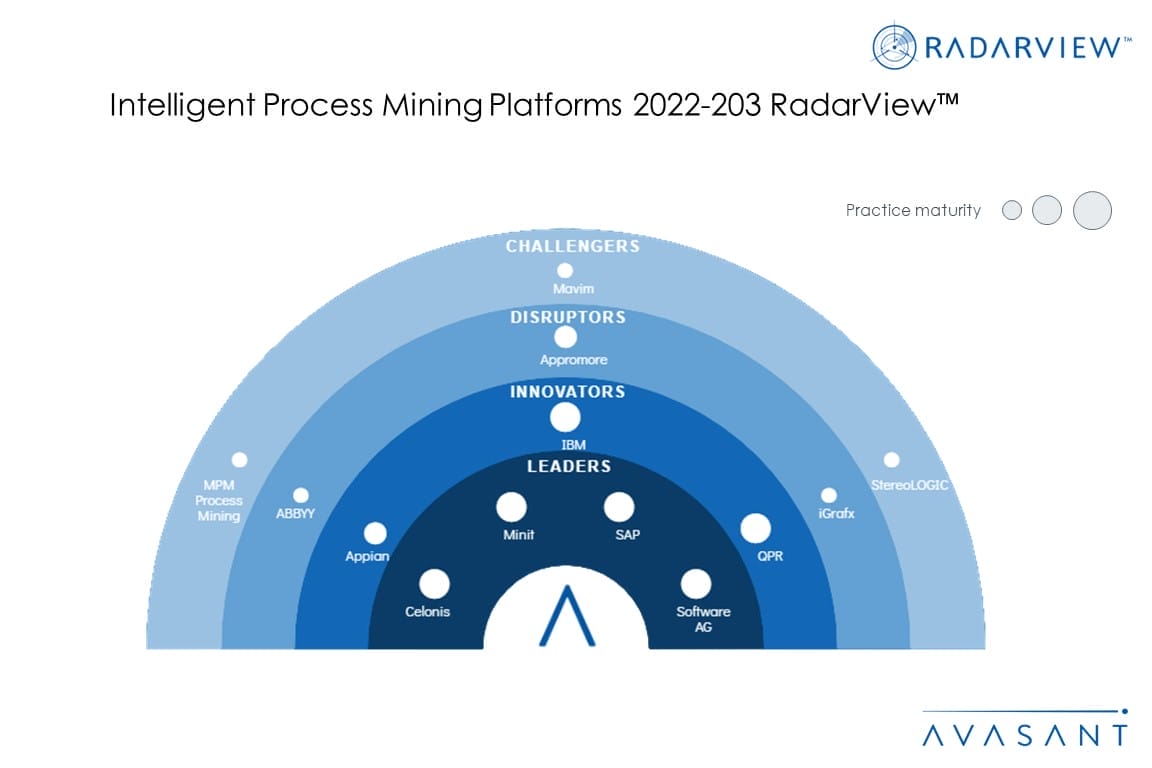
Intelligent Process Mining: Delivering Complex Business Intelligence and Process Transparency
An increase in enterprise demand for hyperautomation has boosted the demand for process mining tools. With advancements in technology such as RPA, low-code/no-code, and artificial intelligence, the role of process mining has elevated from process standardization or automation to digital transformation. Platform features such as data integration with IoT devices and digital twin development enhance process understanding and data visualization. To tap market opportunities, software-as-service (SaaS) providers are embedding process mining in business applications by developing in-house capabilities and acquiring or partnering with vendors in the space. These emerging trends are covered in Avasant’s Intelligent Process Mining Platforms 2022–2023 RadarView™.
November, 2022