Over the last decade, cybersecurity has increased from approximately 2% of the total IT budget to around 7%. And there is no sign that spending on cybersecurity will slow anytime soon. Just as enterprises get a handle on one attack vector, another one appears. Now, AI and quantum computing both promise new methods of defense and attack. Enterprises will continue to need to accelerate their cybersecurity spend to meet these new threats. Still, there is such a thing as throwing too much money at a problem. It is crucial to right-size the IT budget to protect the organization, while also avoiding throwing good money at the wrong problems. The right benchmarks are crucial for this exercise.
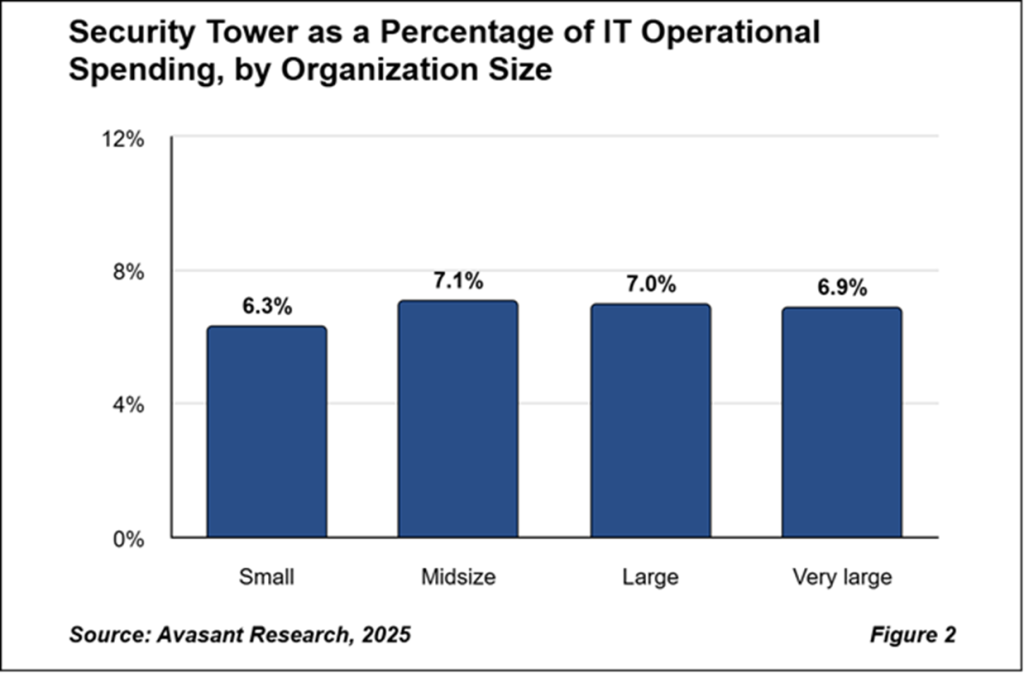
As shown in Figure 2 of our IT Security, Cybersecurity, and Compliance Spending and Staffing Benchmarks 2025 report, organization size has little influence on IT security spending as a percentage of overall IT operational spending. Small organizations allocate 6.3%, while midsize and large organizations allocate 7.1% and 7.0%, respectively. Very large companies spend 6.9% on the IT security tower.
What is the security tower? It includes all IT security, cybersecurity, and security-related compliance spending. It also includes the costs of security personnel (both internal and external), security hardware, security software, and external security services. Both security spending and depreciation of security capital investments in the past are included in the security tower. It does not include current-year security capital spending.
“Cybersecurity can feel like a money pit,” said David Wagner, senior research director at Avasant Research, based in Los Angeles. “However, solid data can give you confidence that you are protecting yourself without wasting money.”
Our full report addresses this need, providing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance spending and staffing. Benchmarks are calculated across several key metrics, including user count, organizational revenue, IT operational spending, number of network devices, number of network locations, and number of endpoints. Security staffing metrics are calculated as a percentage of the IT staff and per user. Industry benchmarks are provided for business services, IT services and solutions, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. By ranking these industries across multiple security spending and staffing metrics, we are able to provide a relative ranking by major industry sector, from most security-intensive to least.
We also include a breakdown of the composite security spending by major category, including identity and access management, security policy and awareness, cybersecurity and incident response, threat and vulnerability management, data privacy and security, and governance, risk, and compliance (GRC). We conclude with guidelines for benchmarking your IT security, cybersecurity, and compliance spending.
This Research Byte is a brief overview of our report, IT Security, Cybersecurity, and Compliance Spending and Staffing Benchmarks 2025. The full report is available at no charge for subscribers. You can contact us for subscription information here.


