There is no doubt that penetration testing feels like the sexy part of security. It conjures Hollywood images of hackers matching wits over high-stakes data. In actuality, penetration testing is mostly about automated scripts, and, even when the hackers are involved, the hardest part of IT security should have already been done. Penetration testing is just one part of a comprehensive security program that needs to be taken seriously long before the white hats are called in. This consistent, formal process is what is missing from many penetration testing efforts.
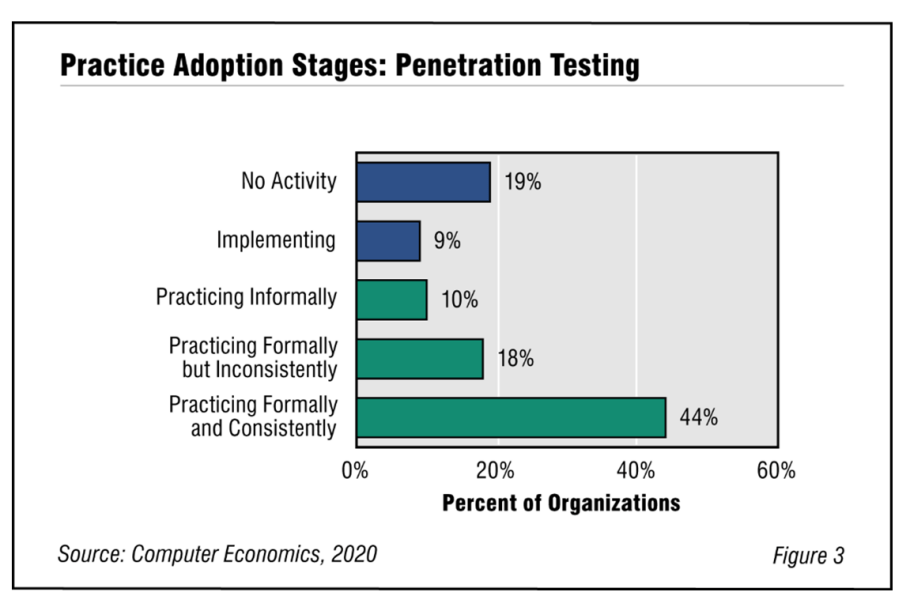
As shown in Figure 3 from our full report, Penetration Testing Adoption and Best Practices, 44% practice penetration testing formally and consistently (what we call the maturity level). Another 18% are practicing penetration testing formally but inconsistently. Another 9% are implementing this best practice for the first time, while 19% report no activity with this practice. The take away is that a fair number of organizations are practicing penetration testing, but too few are doing it formally and consistently.
A penetration test is a best practice that identifies security weaknesses. It is an authorized, simulated attack on an organization’s network and systems to identify vulnerabilities so that they can be patched. Such tests are typically automated by means of scripts but can be augmented with manual attempts to breach security defenses.
The purpose and value of penetration testing, of course, is to harden systems against attack and reduce vulnerabilities to an increasing variety of attack vectors. However, penetration testing is useless without having other security best practices in place. If security is not taken seriously at the development, implementation, and management stages, penetration testing will only find the most cursory issues.
“Penetration testing really shows its value only after you’ve put in your security work,” said David Wagner, vice president of research for Computer Economics, an IT research firm based in Irvine, Calif. “If you don’t have an overall security program, penetration testing will only find the low-hanging fruit. Penetration testing can be expensive, so you want to make sure you get the most out of it.”
The actual act of penetration testing with tools or a team is just a step in a larger, more formal, iterative process. It might follow this pattern:
-
- Establish baseline security measures. The system or infrastructure should be hardened to the best of the ability of the traditional IT team, paying particular notice to security best practices, patching, and common- sense security.
- Conduct initial penetration testing. Then typically, the security team can put systems under a simulated attack using existing tools and scripts looking for known vulnerabilities.
- Address the vulnerabilities. Penetration testing can be expensive and time-consuming. By taking care of the vulnerabilities that can be discovered through the use of due diligence and off-the-shelf tools, IT leaders can save time and money before conducting more expensive tests.
- Call the hackers. If resources are available, an outside vendor or an internal “red team”—a group of security professionals purposely kept in the dark about the IT organization’s architecture and systems so that it can attack from the point of view of an outsider—also can be used to probe for additional vulnerabilities.
- Rinse and repeat. Any weaknesses discovered should be addressed and the process repeated on a periodic basis. Remember that plugging one vulnerability does not mean the system is safe. Regardless of the color hat they wear, hackers, like humans, typically open the first door they find. It does not mean another door is not available.
The full report begins with a definition of penetration testing and provides a look at the iterative process that makes it most effective. We next study the adoption and practice levels, and examining those by organization size and sector. We conclude with best-practice recommendations.
This Research Byte is a brief overview of our report on this subject, Penetration Testing Adoption and Best Practices. The full report is available at no charge for Avasant Research subscribers, or it may be purchased by non-subscribers directly from our website (click for pricing).

