IT security policy audits are among the most popular of the best practices in our study, IT Management Best Practices, which measures the practice rates and levels of 33 IT disciplines. But surprisingly, there is room to grow. While adoption of this best practice increased this year, the practice rate is below historic highs. Considering that many security breaches are caused by failure to comply with IT security policies, it should be a mandate for IT organizations to pay more attention to security compliance.
As shown in Figure 1 from our full report, Security Compliance Audit Adoption and Best Practices, the adoption of this IT management best practice earns a rating on the low side of high. The rating is based on a comparison of the adoption of this practice with 33 other IT management best practices.
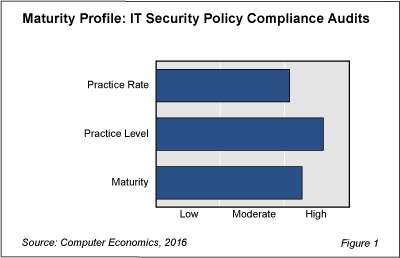
While most security practices tend to be highly adopted, IT security audits still have room to grow. The practice level, however, shows that organizations who do practice security audits are taking them seriously. The practice level is defined as the percentage of the practitioners who are fully engaged, as opposed to only partially adopting the practice. IT organizations that have a formal process in place for responding to security incidents tend to follow through with those procedures.
Overall, this practice earns a high maturity rating. In light of the apparent escalation in threat levels over the past year, there is plenty of room for broader adoption. This is a practice that every IT organization should consider embracing with some level of rigor. In the full report, we introduce this best practice and examine adoption trends by organization size and sector.
It is nearly cliché to bring up the growing number and wider array of threats facing the enterprise today. In recent years, major breaches have hit parts of the U.S. government, Fortune 500 companies such as Target and Sony, and large insurance companies such as Anthem. The number of threats creates a sense that it is impossible for organizations to defend themselves, at least not without significant technology upgrades and unrealistic budgets. However, many of the high-profile breaches in recent years were caused, at least in part, by failures to adhere to internal security policies. For instance, the Anthem breach was due to failure to take necessary steps against a known threat called Heartbleed. The Target threat was due to improper verification of vendor credentials. Lawsuits currently being heard allege that the Sony breach was caused by failure to maintain long-held security best practices and to meet the standards of several industry groups.
Establishing security policies and implementing the best security technology is not enough. Follow-up to be certain that these standards are being maintained is equally, if not more, important.
This Research Byte is a brief overview of our report on this subject, Security Compliance Audit Adoption and Best Practices. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

