Despite a seeming rise in high-profile security breaches, IT organizations have been somewhat slow to embrace formal methodologies for responding to security breaches, assessing the vulnerabilities, and coming up with solutions to prevent future incidents.
As shown in Figure 1 from our study, IT Security Incident Management Adoption Trends, the adoption of this IT management best practice earns only a moderate rating. The rating is based on a comparison of the adoption of this practice with 24 other IT management best practices.
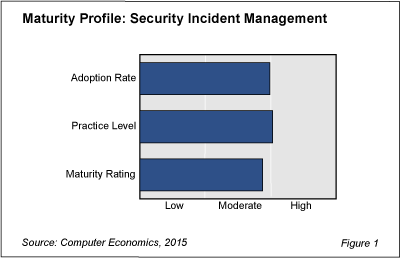
While most security practices tend to be highly adopted, IT security incident management remains just shy of earning that designation. The practice level, however, does make it over the line into the high column, if just barely. The practice level is defined as the percentage of adopters that are fully engaged with the practice, as opposed to only partially adopting the practice. IT organizations that have a formal process in place for responding to security incidents tend to follow through with those procedures.
Overall, this practice earns only a moderate maturity rating based on its combined adoption-level and practice-level ratings. In light of the apparent escalation in threat levels over the past year, there is plenty of room for broader and deeper adoption. This is a practice that every IT organization should consider embracing with some level of rigor. In the full study, we introduce this best practice, examine adoption trends by organization size and sector, and define some of the vendors in the space.
Cyberattacks have become a fact of life, and IT organizations are committing resources to incident response. What is often not well understood is the difference between security incident response and incident management. While security incident response is a technical discipline, security incident management is a more formal process for monitoring, detecting, tracking, and responding to security incidents.
When a security incident occurs, an organization with a security incident management practice will have a response team in place and clearly defined procedures for managing it. This best practice includes deployment of people, processes, and technology to encompass the entire span of security incident management, from responding to the initial problem to initiating improvements.
This Research Byte is a brief overview of our report on this subject, Security Incident Management Adoption Trends. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

