Organizations rely heavily on IT to conduct business, and thus IT security policies should form a major backbone of the organization’s overall security program. Nearly every IT organization has such policies to some extent, but too often they are not formally established, comprehensive in their scope, or followed consistently.
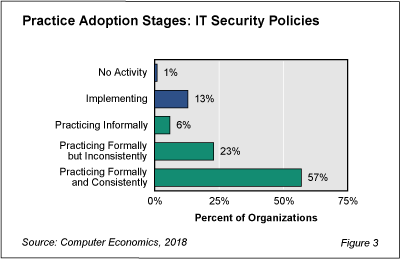
In fact, according to our survey, only 57% of companies adhere to their IT security policies in a formal and consistent manner. If you aren’t in that 57%, your organization is most likely exposed, because an organization’s security program must start with policies.
As shown in Figure 3 from our full report, IT Security Policies Adoption and Best Practices, 57% of survey respondents have formal security policies that they follow consistently (the maturity level). Twenty-three percent of respondents have formal security policies but follow them inconsistently.
IT security policies are management statements that define the organization’s rules and principles related to its security program. Although IT security policies should be comprehensive, covering all elements of the security program, our survey specifically identifies five areas as a test of whether the organization can say that it has established IT security policies. We chose these because they are critical policy areas and because some of these tend to be overlooked. The full report discusses the five: Acceptable use policy, network access policy, remote access policy, supplier security policy, and security audit policy.
“In this area, failure is not an option—or it shouldn’t be,” said Tom Dunlap, director of research for Computer Economics, an IT analyst firm based in Irvine, Calif. “Unfortunately, it’s clear that far too many companies do not understand the consequences of having non-existent or informal IT security policies. Formal IT security policies are required before any other security measures can be taken.”
Without IT security policies, the organization does not have a solid foundation to mitigate risk or take corrective action. To name two examples, if an organization does not have an acceptable use policy, how can a manager discipline an employee who uses his or her work computer to manage the books for a side business? Does it matter if he or she does so on his or her own time? Likewise, how can an organization take action to stop employees from sharing passwords if there is no network access policy?
In our annual IT Management Best Practices study, IT security policies are one of seven disciplines in the IT security and risk management category. The other six are data classification and retention, IT security compliance audits, security incident management, disaster recovery planning, disaster recovery testing, and business continuity planning. These practices are about reducing risk, either from security incidents or from losses due to business disruptions and disasters.
In light of the new security realities, it behooves company executives to be sure they are following security best practices. In our full report, we look at the practice rate, practice level, and maturity level of IT security policies by organization size and sector. We conclude with many practical recommendations for organizations to improve their IT security policies.
This Research Byte is a brief overview of our report on this subject, IT Security Policies Adoption and Best Practices. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

