Most organizations are aware of the IT security threats posed by outsiders. Countermeasures such as firewalls, antivirus software, and intrusion detection systems are all aimed at these threats. Yet these measures do little to counter an even greater threat–that of malicious insiders within the organization.
As our study on Malicious Insider Threats shows, many organizations do not treat these threats seriously. Such threats include fraud, sabotage, and theft or loss of confidential information caused by trusted insiders. These threats go beyond negligence. They represent purposeful action on the part of insiders to act in opposition to the interests of the organization, whether for financial gain, retribution, or some other motivation. Our analysis of these threats is based on a special survey conducted by Computer Economics.
Threats are Underappreciated
Figure 1 shows four categories of malicious insider threats along with the percentage of respondents that view each threat as “major.” Respondents could rank each threat as major, moderate, minor, or no threat. Thirty-eight percent of midsize and large organization view the the risk of unauthorized disclosure of confidential data as a major risk. In all other cases, however, fewer than than one-third of the small or midsize/large organization rate any of the four types of risks as major threats.
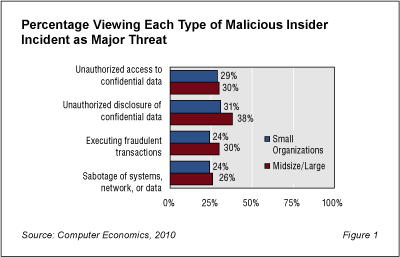
There is not a great deal of difference in the way small organizations, defined as those with less than $50 million in annual sales, and large and midsize organizations view the risks. The larger organizations are slightly more likely to rate the risks as major, but with the exception of guarding confidential information, the differences are not great. Most organizations are only moderately concerned about malicious insiders.
Perceptions of Risk Often Do Not Match Reality
Security professionals have long understood that malicious insiders pose a greater security threat than outsiders. In announcing results of the 2010 CyberSecurity Watch Survey, conducted by CSO magazine, U.S. Secret Service, Software Engineering Institute CERT Program at Carnegie Mellon University, and Deloitte, the authors wrote: “While outsiders are the main culprits of cybercrime in general, the most costly or damaging attacks are more often caused by insiders.”
Yet many IT executives do not appreciate the threat. The moderate level of concern about malicious insiders indicated in Figure 1 is in conflict with the number of incidents actually reported by these same organizations. A good number of organizations are experiencing malicious insider incidents but still not considering them as major threats.
As shown in Figure 2, more than half of organizations, regardless of size, experienced at least one incident of unauthorized access to confidential information in the prior 24 months, according to the Computer Economics survey. Furthermore, more than half (56%) of midsize and large organizations experienced unauthorized disclosure of confidential information. If this pattern continues, it means organizations have a better than 50% chance of experiencing an incident of malicious insiders accessing or disclosing confidential information over the next two years.

Moving to the second two categories of threats, we see that less than one-third of organizations report incidents of fraudulent electronic transactions or sabotage by malicious insiders. Nevertheless, it is important to note that these are still significant percentages. If the reports of these respondents are indicative of general trends, it means that about 20% to 30% of organizations will experience incidents of e-fraud or sabotage by insiders over the next two years.
These results contrast with the level of concern indicated by organizations, as shown in Figure 1. Organizations develop contingency plans for scenarios with much lower probabilities such as earthquakes, hurricanes, or other natural disasters; they should develop proactive plans on how to deal with malicious insider threats as well.
Although the intrinsic threat from insiders has long been recognized, the threat today is greater than ever. Economic recession has led to widespread layoffs and loss of job security. Such conditions lead to a small percentage of insiders developing malicious intent. For example, employees who fear unemployment may plan to steal confidential information such as customer lists that may be useful in future employment or in setting up a competing business. Insiders who feel mistreated may plot to sabotage the organization’s systems. Although the great majority of insiders may harbor no malicious intent, it only takes one or two to wreak havoc on the unsuspecting organization.
This report is abstracted from our major study entitled Malicious Insider Threats: Countering Loss of Confidential Information, Fraud, Sabotage, & Other IT Security Threats Posed by Trusted Insiders. The full report covers four categories of malicious insider threats: accessing confidential information without authorization, disclosing confidential information, executing fraudulent transactions, and sabotage of the organization’s systems, network, or data. For each category we report how seriously organizations perceive these threats and how frequently these threats actually result in violations of security. We then examine the extent to which organizations implement four best practices for controlling user access and 12 best practices for mitigating threats from IT personnel. Finally, we analyze the extent to which organizations take action to counter malicious insider activity by monitoring of insider email, keystrokes, computer files, and Internet traffic.
A sister study, Insider Misuse of Computing Resources, addresses separately threats posed by employees and other insiders who violate their organizations’ acceptable use policies. Both reports are based on a special survey conducted by Computer Economics in 2009.

