The proliferation of smartphones, mobile applications, and desktop virtualization has spawned a surge in the use of bring-your-own-device, or BYOD, policies. However, results from our annual survey of IT management best practices show that BYOD is too often an informal or inconsistent practice, leaving the IT organization vulnerable.
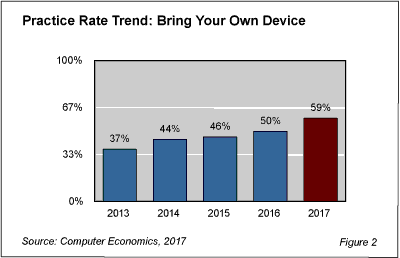
As shown in Figure 2 from the full report, BYOD Adoption and Best Practices, 59% of organizations currently allow employees to bring their own devices, which is up from 50% in 2016 and 46% in 2015.
“Nearly 60% of organizations have BYOD policies in place,” said Tom Dunlap, director of research for Computer Economics, based in Irvine, Calif. “But it is surprising that only 38% have formal policies governing what devices are allowed and what employees can use them for. Companies that let employees bring their own devices into the workplace, but do not have formal policies governing the practice, are putting themselves at risk.”
Why do companies need a BYOD policy? Because smartphones, tablets, and other devices, like any other piece of IT equipment, need to be managed and secured. An organization cannot leave that task up to individual employees. Users today want to conduct business from any location using any device they have at hand, complicating IT’s responsibility to ensure security and reliability. Now there are a handful of technologies and best practices that IT can deploy to allow users to securely access data while working with personal devices.
Many IT organizations have responded with BYOD policies and procedures that enable employees to use their personal devices for work, define what they are allowed to do with them, and specify how security and support for them will be managed.
In the full report, we first take a look at adoption trends for BYOD by organization size and sector. We also discuss the elements that every BYOD policy should contain, steps IT organizations should take before enabling users to access corporate networks with their personal devices, and solutions available to help manage the security of mobile devices and applications.
This Research Byte is a brief overview of our report on this subject, BYOD Adoption and Best Practices. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

