Over the past five years, the percentage of users with IT-supported smartphones has doubled in the enterprise and continues to accelerate, prompting more and more IT organizations to develop policies concerning the use of personal devices to access corporate data and applications.
Figure 1 from our study, Bring-Your-Own-Device Best Practices, shows that a the median, 20.5% of users now have IT-supported smartphones compared with 11.5% in 2009. Moreover, the trend appears to be accelerating. In 2013, the percentage of users with smartphones rose 26% over the previous year.
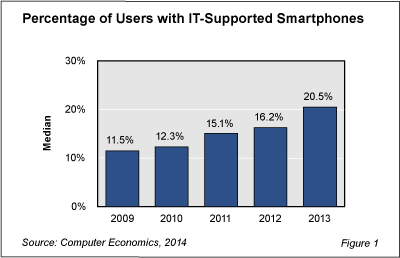
In most cases, these smartphone users have devices that are supplied by the IT organization and it is not clear how many of these smartphones are running enterprise mobile applications. Our Technology Trends research, however, indicates that by 2012 about 27% of organizations had mobile enterprise applications in place and another 17% had plans to implement a mobile application within an 18-month period. Like smartphones, the use of mobile applications in the enterprise is on a steep upward curve.
With mobile computing’s inevitable push into the enterprise, IT organizations can no longer keep these consumer devices outside the firewall. Users today want to conduct business from any location using any piece of hardware, and one response has been to allow employees to access the network with their own smartphones and tablets. More recently, desktop virtualization is spawning much discussion about bring-your-own-device, or BYOD, policies for PCs.
Like it or not, many IT organizations are having to confront BYOD as an emerging practice and adopt policies and procedures to deal with the security, legal, and support issues surrounding it. In the full study, we examine adoption trends for BYOD by organization size and sector. We also discuss the elements that every BYOD policy should contain and the steps IT organizations should take before enabling users to access corporate networks with their personal devices.
This Research Byte is a brief overview of our management advisory on this subject, Bring-Your-Own-Device Best Practices. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

