This report helps enterprises chart out their action plan for developing a robust security posture by identifying potential service providers. It begins with a summary of key trends and challenges that are shaping the cybersecurity space. We continue with a detailed assessment of 28 leading service providers for the cybersecurity. Each profile provides an overview of the service provider, their security-specific solutions, and a list of representative clients and partnerships, along with brief client case studies. Each profile concludes with analyst insights on the provider’s practice maturity, partnership ecosystem, and investments and innovations.
Why Read this RadarView?
As enterprises rapidly shift to cloud, agile, and edge computing, their cybersecurity strategy must adapt. This requires moving from prevention-focused activities to more cyber resilience activities. Thus, applying an increased emphasis on the ability to detect, respond, and recover using well-structured and organized frameworks and methodologies.
This report is designed to inform enterprises about best practices in this space and provide a relatively granular understanding of key service providers.
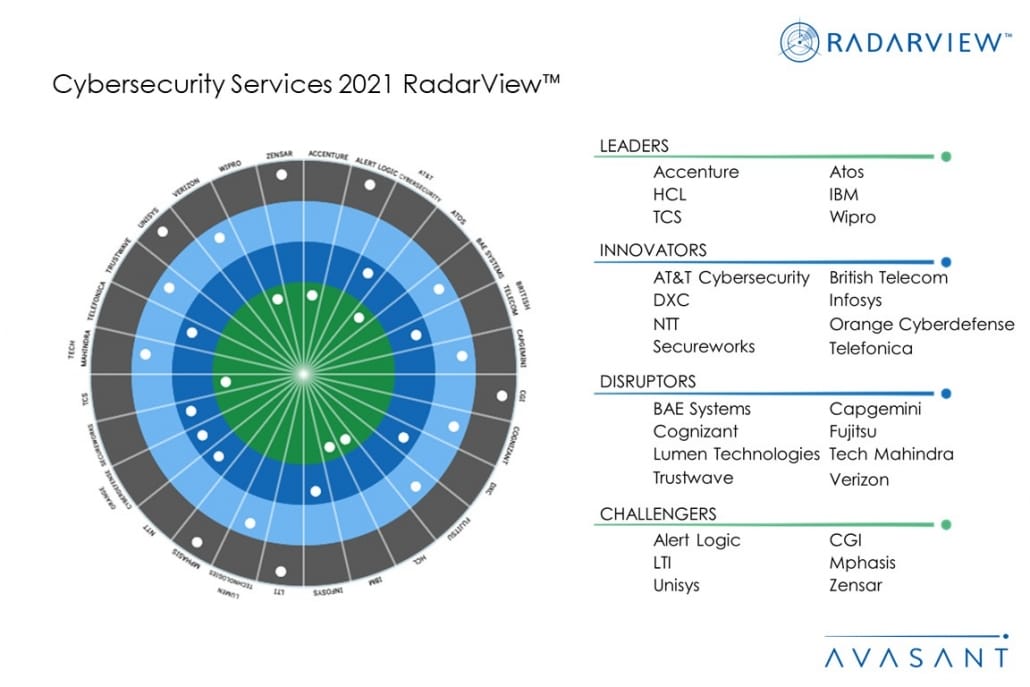
Featured Providers
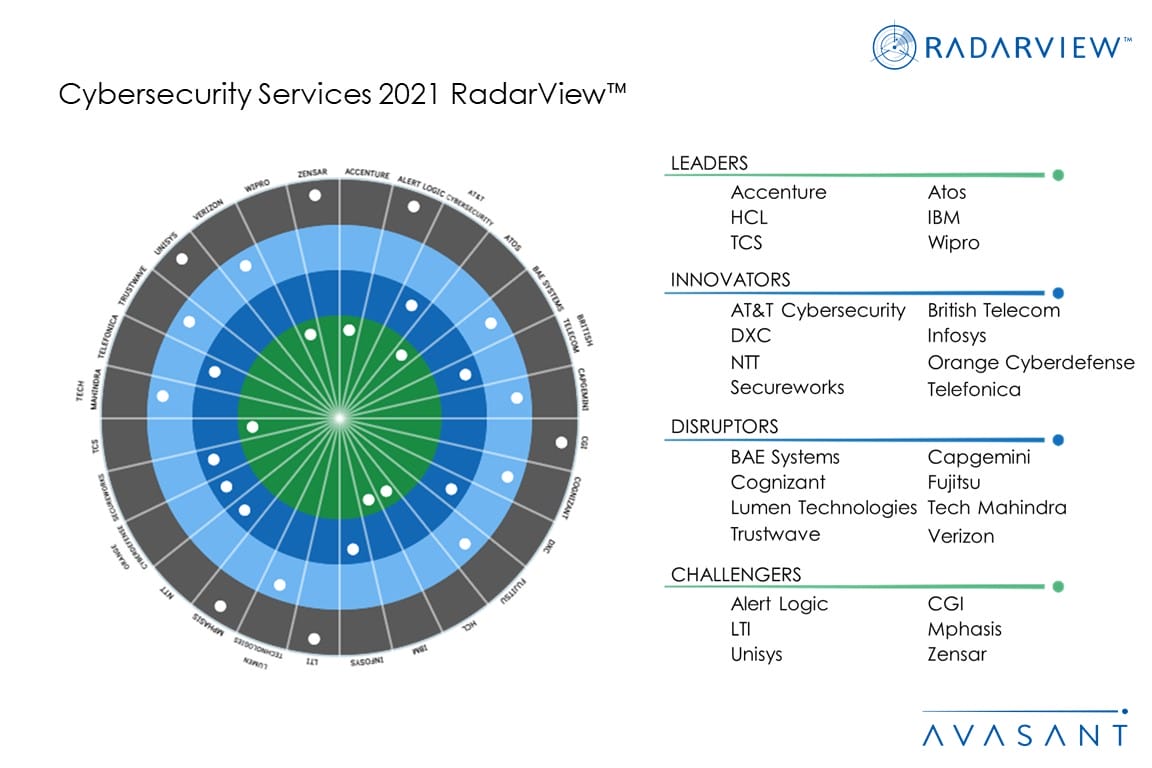
This RadarView includes an analysis of the following digital service providers in the cybersecurity space: Accenture, Alert Logic, AT&T Cybersecurity, Atos, BAE Systems, British Telecom, Capgemini, CGI, Cognizant, DXC, Fujitsu, HCL, IBM, Infosys, LTI, Lumen Technologies, Mphasis, NTT, Orange Cyberdefense, Secureworks, TCS, Tech Mahindra, Telefonica, Trustwave, Unisys, Verizon, Wipro, and Zensar.
Methodology
The industry insights and recommendations presented are based on our ongoing interactions with senior executives, vendors, subject matter experts, and Avasant Fellows, along with lessons learned from consulting engagements.
Our evaluation of service providers is based on primary input from the providers, focused briefings, public disclosures, and Avasant’s ongoing market interactions. The assessment is across the three dimensions of practice maturity, partnership ecosystem, and investments and innovation leading to our recognition of those service providers that have brought the most value to the market over the last 12 months.
Table of Contents
About the report (Page 3)
Executive summary (Pages 4-8):
-
- Defining cybersecurity
- Key enterprise cybersecurity trends shaping the market
- Enterprise cybersecurity adoption: The road ahead
- Avasant recognized 28 top-tier providers supporting enterprise cybersecurity
Lay of the land (Pages 9-19)
-
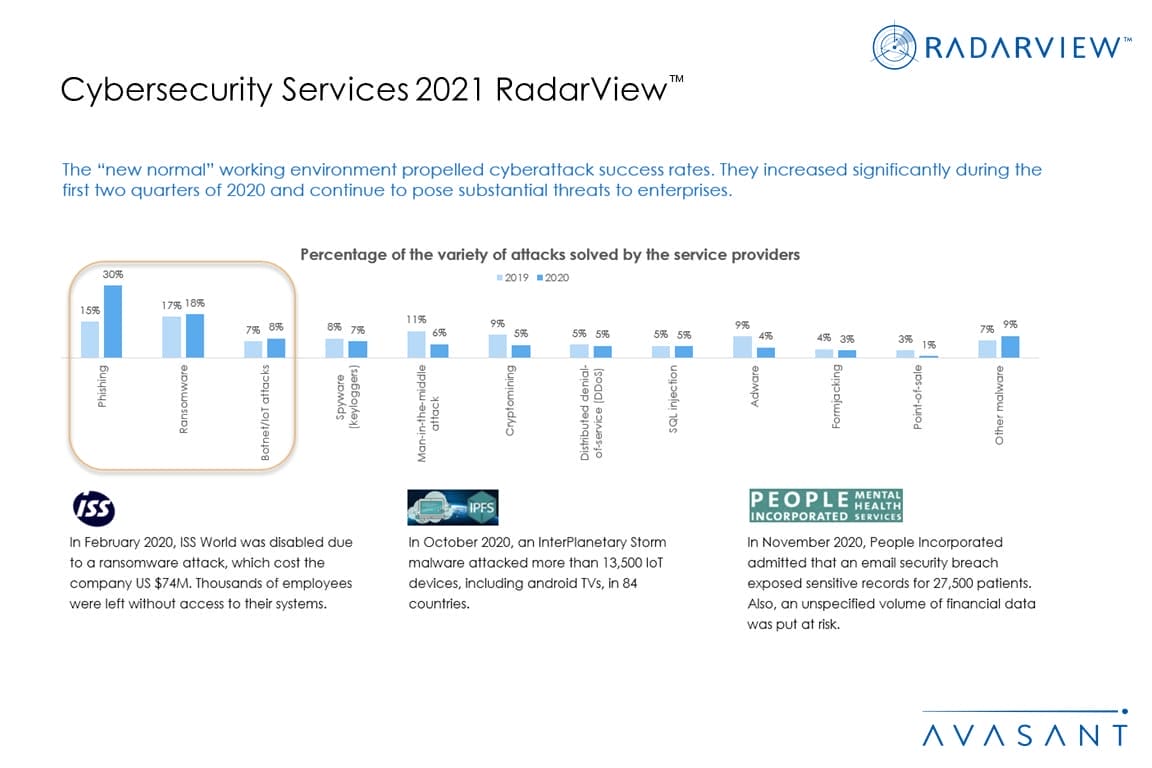
- Phishing continues to be the common medium
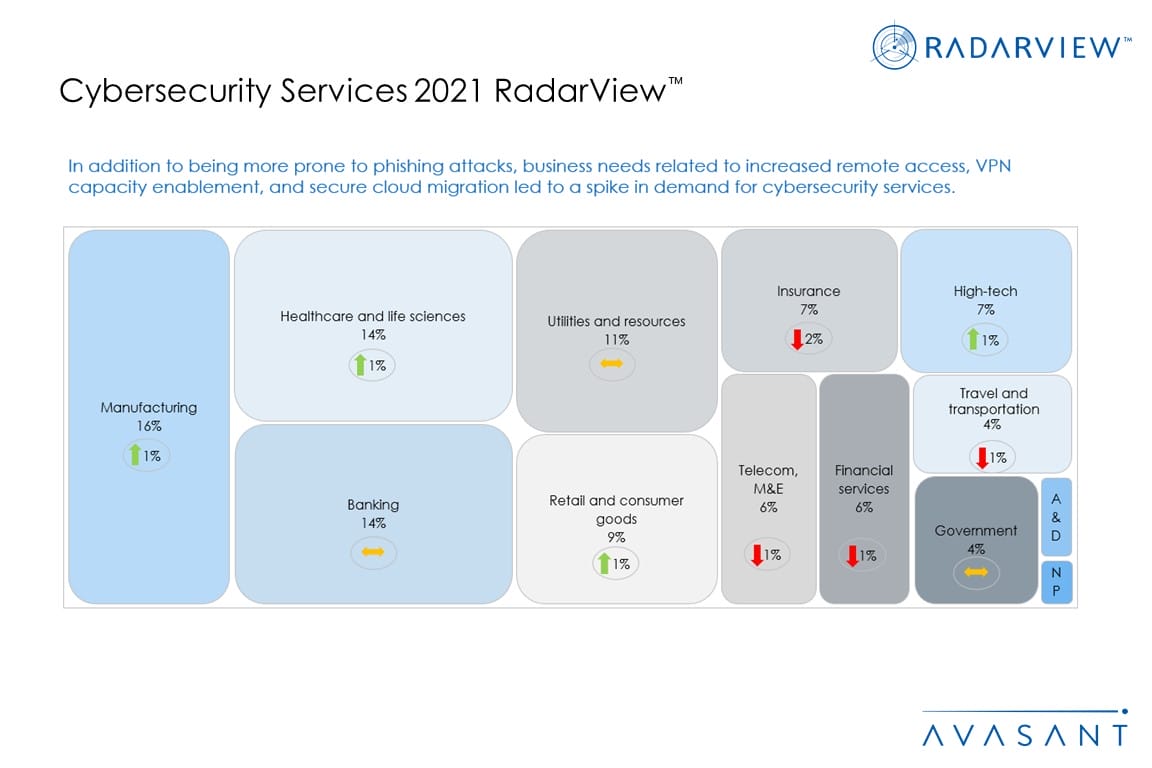
- Manufacturing continues to take a lead in the cybersecurity spend
- Use cases rising for identity governance, access management, regulatory compliance
- Legal directives across the cybersecurity landscape are changing around the globe
- Service providers are collaborating with ecosystem partners and acquiring capabilities
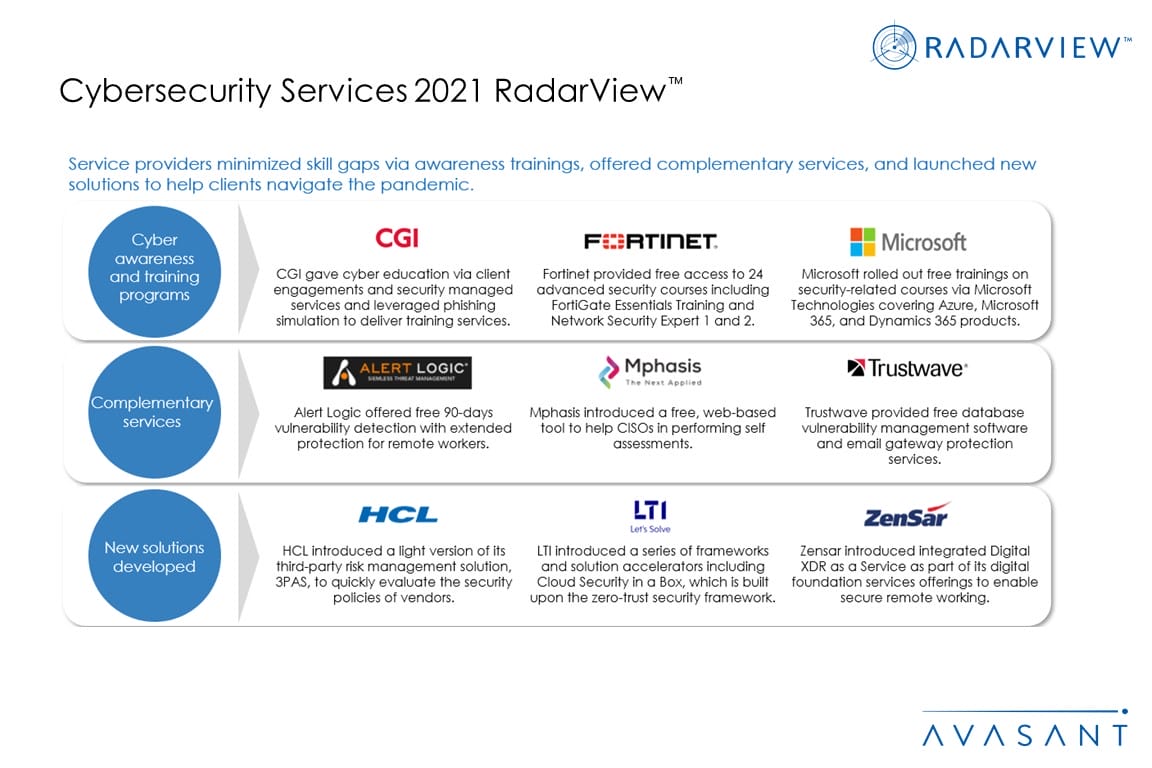
- Amid COVID-19, service providers proactively engaged with customers
The Road Ahead (Pages 20-24)
-
- The increased migration to cloud, has brought focus on identity
- In the “New Normal” working environment, zero trust takes the fore
- Secure by design ops gaining momentum to address security concerns
- Need for advanced solutions leveraging automation & orchestration capabilities
RadarView Assessment (Pages 25-30)
-
- Methodology and coverage
- Interpretation of classification
- RadarView assessment
Service Provider Profiles (Pages 31-87)
-
- Detailed profiles for Accenture, Alert Logic, AT&T Cybersecurity, Atos, BAE Systems, British Telecom, Capgemini, CGI, Cognizant, DXC, Fujitsu, HCL, IBM, Infosys, LTI, Lumen Technologies, Mphasis, NTT, Orange Cyberdefense, Secureworks, TCS, Tech Mahindra, Telefonica, Trustwave, Unisys, Verizon, Wipro, and Zensar
Key Contacts in Avasant (page 88)
Read the Research Byte based on this report.