The pandemic is accelerating distributed service architectures, which is driving changes to the security landscape. Changes in working practices are exposing different attacks, altering the types and severity of threats an organization is exposed to. Though phishing remains the most common attack mode, the SolarWinds exploit has brought attention back onto supply chain-based attacks.
These emerging trends are covered in Avasant’s Cybersecurity Services 2021 RadarView™ report. The report is a comprehensive study of the industry-wide adoption of cybersecurity services. It includes the current landscape, impact of COVID-19, enterprise recommendations, and a close look at the leaders, innovators, disruptors, and challengers in this market.
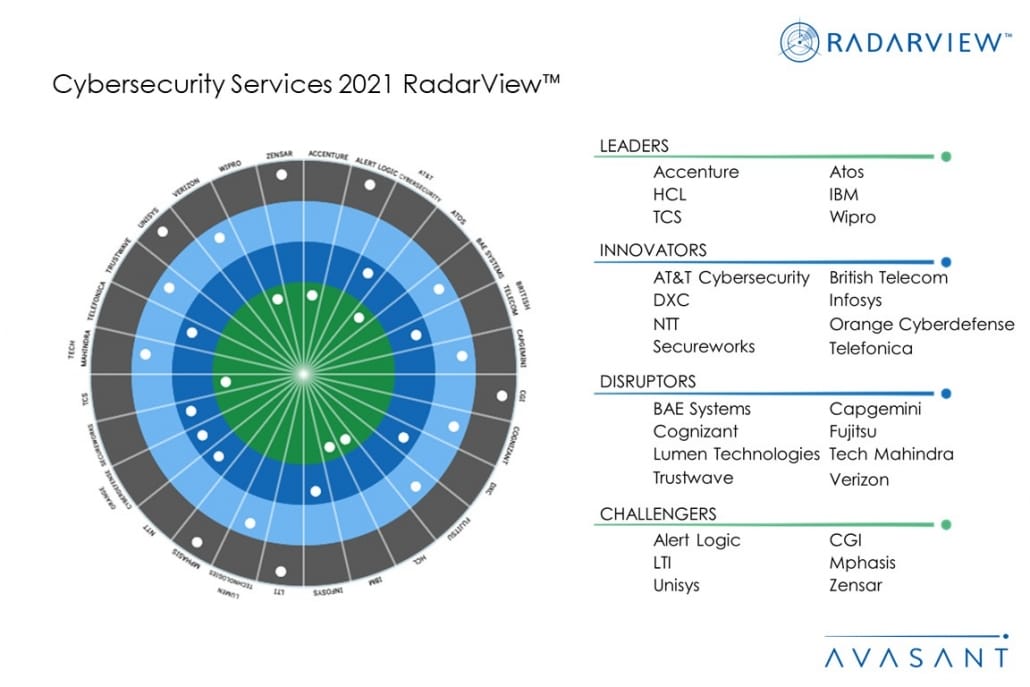
Avasant evaluated 42 providers using three dimensions: practice maturity, partnership ecosystem, and investments and innovation. Of those 42 providers, we recognized 28 as having brought the most value to the market during the past 12 months.
The report recognizes service providers in four categories:
-
- Leaders: Accenture, Atos, IBM, HCL, TCS, and Wipro
- Innovators: AT&T Cybersecurity, British Telecom, DXC, Infosys, NTT, Orange Cyberdefense, Secureworks, and Telefonica
- Disruptors: BAE Systems, Capgemini, Cognizant, Fujitsu, Lumen Technologies, Tech Mahindra, Trustwave, and Verizon
- Challengers: Alert Logic, CGI, LTI, Mphasis, Unisys, and Zensar
Figure 1 from the full report illustrates these categories:
Mark Gaffney, a Director with Avasant, congratulated the winners noting, “As enterprises are enabling remote access of critical IT infrastructure, it becomes imperative to follow zero-trust security principles while driving user experience and employee wellness. Moreover, there is an increased need for introducing security in the early stage of the business life cycle, pushing service providers for a Secure by Design approach.”
Some of the findings from the full report include the following. Enterprises should:
- Integrate IAM solutions with analytical and reporting capabilities.
-
- Managing over-provisioned permissions in the cloud environment will increasingly become a constant challenge, as enterprises move to a hybrid/multicloud environment.
- Augmenting identity access management (IAM) solutions with user and entity behavior analytics (UEBA), Identity as a Service (IDaaS), privileged access management (PAM), and real-time centralized access management will empower organizations to detect and respond to threats swiftly.
- Gain momentum with zero trust principles-based offerings.
- A zero trust security solution can be implemented through various approaches including software-defined perimeter (SDP), identity governance, microsegmentation, and software-defined network access to support various use cases such as biometrics and multifactor authentication (MFA).
- Various service providers have developed a series of frameworks and platforms based on zero-trust security principles, focusing on user experience, automation, and enhanced visualization.
- Bring a Secure by Design mindset at every stage of the business life cycle.
- To ensure threat concerns are addressed throughout solution development, deployment, and maintenance, security needs to be top of mind even before coding starts.
- DevSecOps, popularly known as Secure by Design, revolves around four fundamental pillars: people, process, technology, and governance. Thus, bringing together Dev, Sec, and Ops teams to work toward shared goals in an open, transparent, and accountable environment.
- Outsmart hackers by embedding automation in security solutions.
- As hackers are making smart inroads in security, solution providers need to augment their overall security framework by leveraging automation and orchestration capabilities.
- Service providers are enhancing security services with security orchestration, automation, and response (SOAR) tools, advanced managed detection and response (MDR) tools, and automated response playbooks to identify patterns and achieve efficient time to detect and respond to attacks.
“As the focus increasingly shifts to identity, it is important to consider tools that enable centralized access management powered by artificial intelligence and machine learning to have real-time visibility into user access such as user and entity behavior analytics. As more and more enterprises transition to a hybrid/multicloud environment, enabling access provisioning and deprovisioning is optimized when performed through a central team and common set of tools.” said Avasant’s Associate Research Director, Gaurav Dewan.
The full report also features detailed RadarView profiles of the 28 service providers, along with their solutions, offerings, and experience in assisting enterprises in digital transformation.
This Research Byte is a brief overview of the Cybersecurity Services 2021 RadarView™ report (click for pricing).

