Each year, hundreds of millions of sensitive personal records are exposed by hackers and cybercriminals. Encryption is an essential security control and part of a company’s security policies and procedures. Yet, despite high practice rates, few IT leaders encrypt their data consistently.
Companies that do not enforce data encryption face ugly consequences. Unauthorized individuals might steal data from compromised accounts or gain access to unencrypted data. Ransomware and other attacks are significantly more effective without encryption. Moreover, a company’s reputation can be affected by breaches. That is why encryption is often mandated in security regulations.
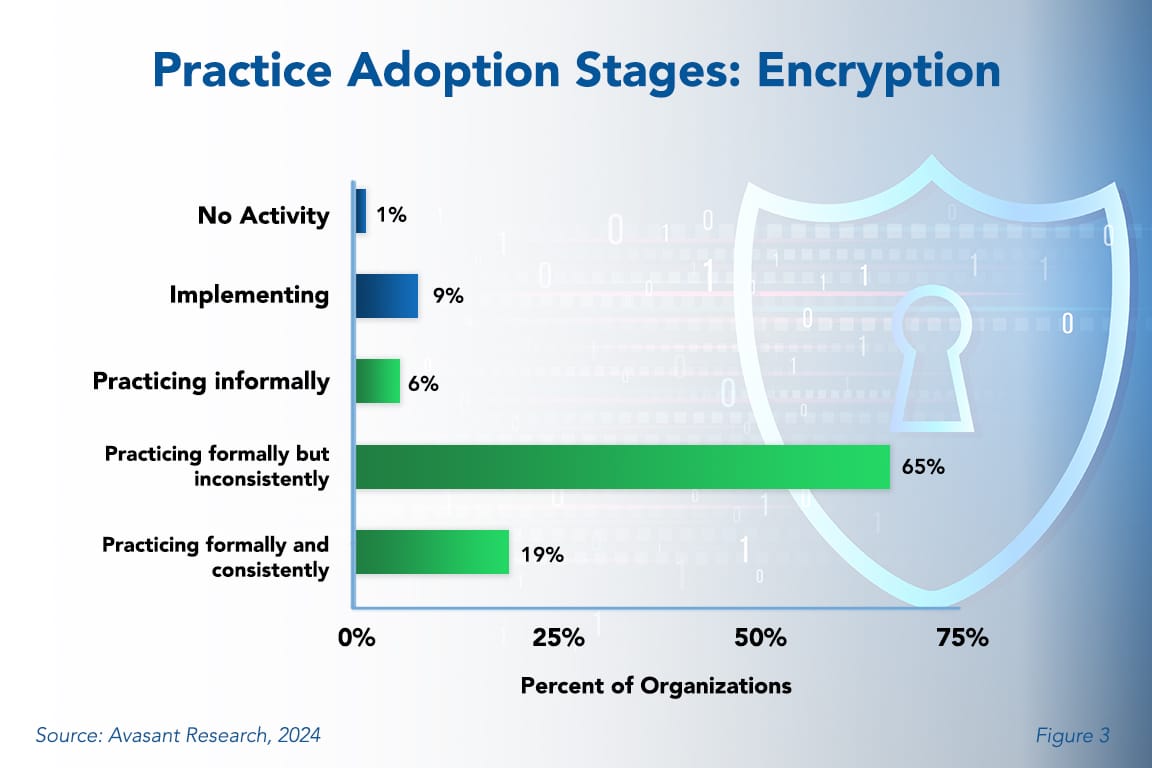
As shown in Figure 3 from our full report, Encryption Best Practices, 6% of our survey respondents encrypt data informally, while 65% do so formally but inconsistently. This may mean that they only encrypt certain data for certain personnel or in specific locations but not others. Whatever the reason for the inconsistency, this remains a pressing concern for executives committed to thwarting cybercriminals. It is surprising that only 19% practice encryption formally and consistently.
“All PII and company data should be encrypted, and it is not challenging to do so,” said Waynelle John, research analyst for Avasant Research, based in Los Angeles. “There are numerous free solutions available, but encryption initiatives must be driven from the top down to ensure consistency.”
Data theft is on the rise, but encryption best practices can protect sensitive or confidential information, both in storage and in transit. It is an advisable practice for every organization, especially those processing personal information or other highly confidential data.
Take the case of the MOVEit data breach of 2023. This significant global cyberattack exploited a vulnerability in Ipswitch’s managed file transfer software, MOVEit. The attackers utilized SQL injection on public-facing servers to steal files from over 2,500 organizations worldwide. More than 60 million individuals were impacted, with 80% of affected organizations based in the United States. The extent of this breach was possible because the data handled by the MOVEit software is often unencrypted. Therefore, once attackers found a weak spot, they were able to access significant amounts of data.
Significant challenges lie in a lack of employee awareness, education, and training regarding encryption practices. Another area of inconsistency relates to where encryption is performed. Data is at risk when it is at rest in a database or storage repository and when it is in transit over a network. Consistent encryption requires the protection of data in both states. Yet, some companies only encrypt data in only one of these states, potentially exposing their data to attack.
The full report seeks to define encryption and provide suggestions for getting started. We also study adoption, practice levels, and maturity and examine these parameters by organization size and sector. We conclude with best practice recommendations.
This Research Byte is a brief overview of our report Encryption Best Practices. The full report is available at no charge for subscribers, or it may be purchased by non-clients directly from our website (click for pricing).


