As organizations increase their use of information technology to do business, employees and other insiders are using computers and the Internet more and more in their day-to-day work. Although these computing resources can greatly increase worker productivity, they can also be misused.
This Research Byte is adapted from the executive summary of our full report, Insider Misuse of Computing Resources, which analyzes 14 forms of insider misuse in detail. Based on our survey of 100 IT security professionals and executives worldwide, the full report analyzes the threat of insider misuse of computing resources–that is, any violation of an organization’s policies regarding acceptable use. For each of 14 types of insider misuse, we analyze the perceived seriousness of the threat, typical organizational policies or lack thereof, frequency of violations against company policy, analysis of preventive and detective actions taken by organizations to deter the misuse, and typical levels of enforcement.
The threat of insider misuse goes beyond loss of productivity. Some forms of misuse also expose the organizations to more sinister threats. For example, surfing the web can bring users to websites that contain malicious code, opening the user’s desktop and network to infection. Participating in peer-to-peer file sharing networks can do the same. Storage of pirated music, video, or unlicensed software exposes the organization to copyright violation liabilities. There are many other examples of the threats to security that can directly result from failure to reign in insider misuse of computing resources. While many organizations are sensitive to the need to defend against information security threats originating from outside the organization, the threat posed by insiders misusing computing resources can be just as great or greater.
Understanding the Threat of Insider Misuse
Insider misuse, as defined in this report, is not necessarily malicious behavior. Individuals misusing the organization’s computing resources are for the most part not doing so with the intent to harm the organization. They may just be attempting to “get the job done.” For example, an employee may use his personal laptop to bring work home over the weekend in spite of the organization’s ban on use of personal computing devices for business purposes.
Insider misuse does not need to be malicious to pose a threat to the organization. The study shows a number of ways that violation of an organization’s acceptable use policy may result in harm. Making insiders aware of these threats is an important part of mitigating the risk of insider misuse as we discuss later in the full study.
A sister report, Malicious Insider Threats, addresses threats where the insider intends to harm the organization or acts in a purposeful way that threatens the organization’s interests. Admittedly, there is sometimes a fine line between malicious intent and mere misuse. For example, an employee downloading music or video files to a desktop computer would not usually be doing so with intent to harm the organization. But if the files being downloading are pirated, the employee is putting the organization at risk. Furthermore, if the employee is using a peer-to-peer file-sharing program to download music, his behavior could inadvertently give outsiders access to confidential files on the computer. The employee may not intend to harm the organization, but his actions put the organization at risk.
Nevertheless, we find it useful to separate threats from insider misuse from threats by insiders with malicious intent. Furthermore, many of the countermeasures against insider misuse are also useful to counter malicious insiders.
How Serious Is the Threat of Insider Misuse?
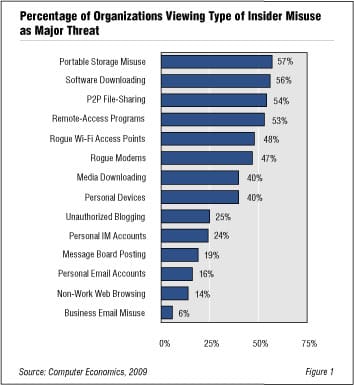
Before delving into our analysis of each threat, it is useful to examine them in total. For this analysis, we look at all types of insider misuse and rank them according to the perceived seriousness of each threat. Figure 1 shows the 14 categories of insider misuse ranked by the percentage of organizations viewing each as a “major threat.”
In our survey, we asked respondents to rate the “seriousness” of each category of insider misuse as no threat, a minor threat, moderate threat, or major threat. We recognize that the word seriousness has no formal definition in risk management. Typically, risk management professionals quantify risks by their “severity” (potential harm) and the “likelihood” of experiencing an incident within a given timeframe.
However, because many forms of insider misuse are not readily quantifiable, we use the word “seriousness” to gauge how concerned IT security professionals are with each threat. We believe the seriousness level provides a useful measure of the perceived importance of each threat, while being mindful that perception and reality are not always consistent.
In assessing the seriousness of each category, we asked respondents to consider all forms of potential damage to the organization, such as effect on system availability or integrity, network performance, legal liability, disclosure of confidential information, loss of worker productivity, and damage to the organization’s reputation. In addition, we asked respondents to evaluate these threats without consideration of any countermeasures their organizations were taking to deter misuse.
Loss of Information, Security Breaches, and Legal Liability vs. Productivity Loss
Interestingly, the 14 categories of insider misuse fall into two distinct groups. The first eight categories form one group, where at least 40% of our respondents view each as a major threat. The first group includes unauthorized copying of files to portable storage devices; downloading unauthorized software; use of unauthorized P2P file-sharing programs; remote access programs; rogue wireless access points; unauthorized modems; downloading of unauthorized media; and use of personal computing devices for business purposes.
What do these forms of misuse have in common? They all pose a threat primarily in terms of loss of information, security breaches, and legal liability. For example, unauthorized copying of files is a threat as it may lead to loss of confidential information. An employee using his own laptop for business purposes may inadvertently take confidential information home at night or retain this information when he leaves the organization. Downloading unauthorized software or using P2P programs may introduce malware into the organization, leading to theft of information or loss of system availability. It is not difficult to envision the seriousness of the threats that these forms of misuse pose to the organization.
There is a significant gap between this first group and the bottom six categories. Only 25% or fewer of our respondents considered these as major threats. This group includes unauthorized blogging or participating in message boards concerning the organization’s business, instant messaging using personal accounts, non-work-related web browsing, and using the organization’s email system for personal matters.
The forms of misuse in this second group are perceived as less serious threats than those in the first group. The perceived threat in the second group is primarily loss of worker productivity. One may argue that some of these forms of misuse also lead to loss of confidential information—for example, an insider blogging about the organization’s business without authorization could disclose trade secrets. Or an insider using a personal instant messaging account through the corporate network could introduce malware into the organization. Nevertheless, our respondents do not view these forms of misuse as being as serious as those in the first group. Whether these forms of misuse should be treated more seriously is a subject for analysis in the full report.
Sample of Key Findings
The bulleted points below summarize some of the findings of the full study:
-
Unauthorized copying of files to portable storage devices is the most serious threat and a major source of information leakage from organizations. The majority of organizations categorize it as a major threat, yet approximately one-third make no attempt to deter such activity.
-
Downloading unauthorized software is a close second in perceived threat level, and nearly 90% of organizations have policies forbidding this activity.
-
Unauthorized P2P file-sharing programs are considered a major threat by more than half of organizations, but one-quarter make no mention of P2P programs in their acceptable use policies.
-
Use of unauthorized remote access programs and services round out the top four perceived threats, with 17% reporting widespread violations of policy.
-
Downloading of unauthorized media content such as video and music is not judged as serious as the preceding four threats. The majority of organizations nevertheless give verbal warnings to insiders that violate organizational policy against unauthorized downloading.
-
Unauthorized authorship of blogs concerning the organization’s business is not addressed in the policies of most organizations. Similarly, most organizations make no attempt to deter insiders from making unauthorized postings to message boards concerning the organization’s business.
-
More than one-third of organizations have no policy concerning instant messaging using personal accounts.
-
The large majority of organizations view use of personal email accounts from within the corporate network to be a moderate or major threat, but 29% either have no policy or take no action when policy violations are detected.
-
More than half of organizations consider non-work-related web browsing to be a moderate or major threat, but one-third explicitly allow insiders to browse the Web from within the corporate network. This may be because the majority of companies have specific controls in place to monitor or block inappropriate web browsing, though there are significant variations in the types of sites restricted.
-
More than half of our respondents view use of business email for personal matters as a moderate or major threat, but one-third do not address this behavior in their acceptable use policies or make any attempt to deter it. Nearly half of all organizations report widespread violations of corporate policy.
- To deter or detect insider misuse, most organizations have email monitoring policies in place, and the majority of organizations examine insider computer files or monitor insider Internet traffic when misuse is expected. Few log insider keystrokes, however.
The full report analyzes these trends and statistics on the 14 categories of insider misuse in more detail. We also analyze the prevalence of certain practices in enforcing policies. These practices include methods to increase awareness of policies, email monitoring, keystroke logging, examination of insider computer files, and monitoring of Internet traffic. We also analyze the types of websites that organizations typically forbid, restrict, or monitor.
This Research Byte is adapted from the executive summary of our special report, Insider Misuse of Computing Resources. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website.
Please refer to the extended report description for the full table of contents and list of figures for this report.

