Policies for personal use of IT resources are policies that explicitly restrict or permit use of the organization’s IT resources for personal reasons. The good news is that 90% of survey respondents have adopted personal-use policies, at various levels of commitment. However, despite high adoption, not nearly enough companies consistently and formally practice these policies.
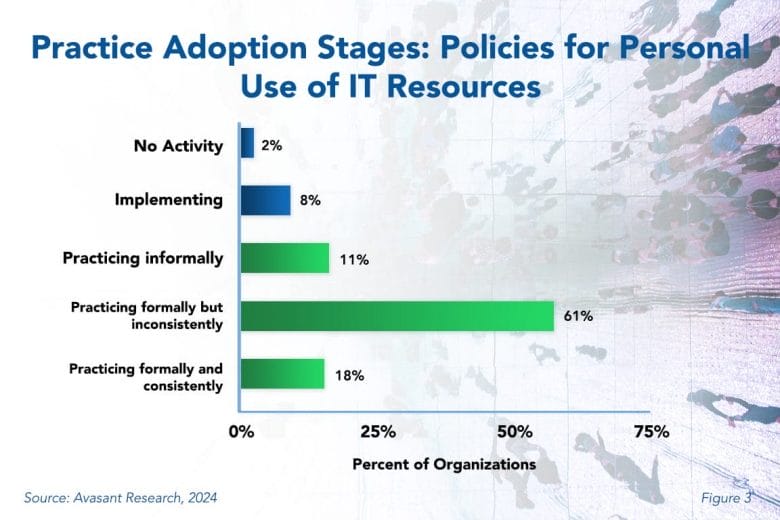
Figure 3 from our full report, Policies for Personal Use of IT Resources Best Practices, shows the percentage of IT organizations at each stage of adoption. About 11% apply personal-use policies informally. Most organizations (61%) practice it formally but inconsistently, while only 18% are fully engaged, practicing it formally and consistently. It is concerning that 61% do not enforce these policies consistently. This indicates that IT leaders may have a formal policy in place so they can check a box on their security audit. They may even have implemented tools to monitor compliance. But they do not consistently monitor and follow up on cases of non-compliance.
Examples of personal use of the employer’s IT resources include non-work-related web surfing, personal e-mail or instant messaging, posting to personal social media accounts, downloading music or unlicensed software, online shopping, and unauthorized copying of files to portable storage devices. This is not an exclusive list, of course.
Personal use of the employer’s IT resources, however, goes beyond wasted computing resources. It also goes beyond the loss of productivity. Surfing the web can bring users to websites that contain malicious code, opening their desktops to infection. Storage of pirated music, video, or unlicensed software exposes the organization to copyright violation liabilities. Posting to personal social media accounts can imply that the views expressed represent the employer. There are other examples of threats that can directly result from failure to rein in personal use of the organization’s computing resources.
“Personal-use policies aren’t just about checking email or updating your Facebook status,” said Tom Dunlap, director of research for Avasant Research, based in Los Angeles. “They’re about protecting company data, boosting productivity, and creating a clear line between work and personal life.”
Please note that this best practice does not specify what the personal-use policies should be, only that policies should be established. An organization may forbid or permit personal use of the employer’s systems or restrict or permit use in specific ways. The nature of the policy should be aligned with the characteristics of the organization. Those with high needs for information privacy and security or in regulated industries, for example, should have policies that are stricter than those of other organizations.
The full report examines the extent to which IT organizations have adopted personal-use policies and measures the level of engagement in the practice. We also look at how the adoption of this IT management best practice differs by organization size and sector. Finally, we provide guidelines for tailoring a personal use policy for a specific organization and recommendations for monitoring the success of this best practice.
This Research Byte is a brief overview of our study, Policies for Personal Use of IT Resources Best Practices. The full report is available at no charge for subscribers, or it may be purchased by non-clients directly from our website (click for pricing).

