Although IT professionals usually adhere to strict security guidelines with the complex development, implementation, and management aspects of their jobs, they sometimes drop their guard in relation to security with some of the more mundane job duties such as data center procedures. The challenge is that these procedures are generally unsophisticated to implement, yet can be very complex to secure. This article highlights the security weaknesses that can be created by such administrative procedures and outlines common sense management practices that can close such back door vulnerabilities.
Eliminating back door vulnerabilities is becoming an important goal for the security program. Cyber-criminals have begun to target specific organizations for financial gain, and they are actively searching for ways to gain access to financial and personal information contained in corporate systems. Furthermore, governmental regulations such as Sarbanes-Oxley and HIPAA require that organizations establish strong internal controls to mitigate the risk of information theft.
Maintenance Procedures That Can Create Back Door Vulnerabilities
There are many data center procedures regularly developed by the technical staff that can inadvertently introduce security vulnerabilities. For example:
- Server backups
- Centralized logging and monitoring
- User account administration
- Administrative remote access
These vulnerabilities are introduced because of the following common practices:
- Technical staff members generally design data center procedures on an ad hoc basis, without appropriate security controls, because they give higher priority to building such controls into procedures that involve the user community. Simply put, the technical staff trusts itself. The lack of a formal process to build internal procedures can mean that these processes may contain serious security deficiencies. This is the primary reason that security vulnerabilities exist in data center procedures.
- Data center maintenance processes are often assigned access rights that are much higher than necessary. This problem is compounded by the fact that many IT personnel who perform administrative duties already have highly escalated access rights. The level of security risk introduced by such data center processes varies depending on the level of authority assigned to the process and the number of individuals or other systems that are authorized to execute it.
- In some data centers, there has been a proliferation of duplicate, overlapping, or obsolete procedures in the production environment. Depending on the types of data they interact with or the administrative access they provide, it is common for these procedures to possess varying levels of risk exposure to the environment. Each procedure by itself may be manageable, but as various processes with varying risk tolerances form inter-relationships, it becomes difficult to maintain a defined risk profile for the data center as a whole. Even worse, as procedures become obsolete they are often just abandoned, leaving back door vulnerabilities that are unattended and, eventually, unknown.
The technical staff often considers these vulnerabilities as a necessary risk in managing the infrastructure. Because of their strong technical skills, personnel may feel confident that they have any risks associated with these procedures well under control. However, the technical staff can be lulled into a false sense of security regarding its ability to track and manage all of the back door vulnerabilities that they have introduced over time.
Example: Tape Backup
A tape backup provides a good example of how a data center procedure can be implemented in a manner that creates a significant back door vulnerability. IT staff often place tape backup procedures into production with little formal control. They install and configure the software to execute the backup and enter a task into the schedule to perform the backup at required intervals.
What can make this scenario potentially disastrous is that the execution of the tape backup will almost always require escalated system privileges. Thus, the backup will execute in privileged mode often at the OS, network, data repository, and application system levels. In most environments, if a malicious individual can penetrate the tape backup infrastructure, he will gain access to the organizationâs most sensitive data.
Insider Risk
In addition to the risk of outsiders taking advantage of back door vulnerabilities, the possibility cannot be overlooked that many security incidents are the work of insiders. Some of the system management personnel who enjoy high system access rights and work on internal procedures may consider themselves above the security rules and regulations that the general IT populace must follow. While most system administrators would never intentionally compromise the infrastructure, there are always a few bad apples and sometimes they are malicious.
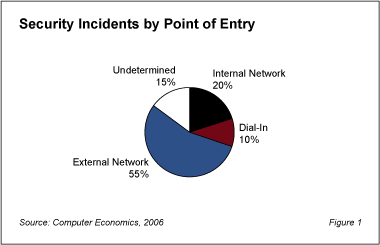
Computer Economics research reveals that security risks from insiders continue to pose a threat. According to our recently released 2006 IT Security Study, a high percentage of security breaches are directly attributable to employees, contractors, and other insiders that have access within the firewall. Figure 1 illustrates that, at a minimum, 20% of all security breaches happen inside the firewall, and the total may be as high as 35%. While it is not being suggested that technical personnel are responsible for a significant number of those breaches, their special access rights do make it important to pay attention to the procedures that they follow on a daily basis. It is also important to recognize that these same individuals usually have access to the systems that are designed to detect malicious activity, which would allow them to delete log files, for example.
Another key problem is that most IT organizations are understaffed and overworked, yet they are still expected to deliver up-time as high as 99.999%. This statistic has a powerful message: virtual perfection is expected. The pace that these technicians must maintain creates the need to work faster and to focus on items that provide measurable benefits to the business. Internal data center procedures such as backups, logging, and monitoring do not fit into this category. Personnel are required to implement numerous detective controls, such as logging and monitoring, but they might not secure the systems that aggregate the collected logs, for example. This does not suggest a lack of concern or a malicious intent â they just do not have the time to develop adequate processes and procedures.
The larger and more complex the environment, the greater the incentive is for system administrators to create technical shortcuts. These shortcuts often take their toll on support procedures in the form of redundant passwords across multiple systems, excessive access rights that violate the âleast privilegeâ rule of thumb, and the proliferation of ad hoc processes and procedures, including duplicate and outdated versions. When all of these elements are combined, the overall security of the system can become seriously compromised.
How to Minimize Back Door Vulnerabilities
What must you do to ensure that there are not significant back door vulnerabilities in your data center? Computer Economics recommends the following actions as principles for minimizing security risks in data center procedures.
- Address data center procedures in the security policy. Individuals that create and maintain data center procedures need guidance concerning the principles outlined in this article. It is far better to build such procedures correctly at the outset rather than identifying vulnerabilities through security audits.
- Invest in administrative tools. Technology cannot solve every problem, but selecting appropriate tools to support administrative procedures will lessen the need for technical staff to maintain high system access rights for routine data center management activities. There are also, of course, productivity benefits in automating data center maintenance procedures.
- Separate duties. The internal control principle of âseparation of dutiesâ should be applied to all data center maintenance procedures. Protect against the potential for abuse by assigning individuals with overlapping duties and enforcing mandatory vacations for individuals with escalated privileges.
- Rotate strong passwords. Create a schedule for rotating passwords for administrative infrastructure access. While the schedule should be aggressive, it would be impractical to change them as often as user passwords. Any password rotation schedule is preferable to the practice seen in many data centers, where administrative passwords are virtually never changed.
- Assign unique passwords. Do not recycle old passwords and do not use the same password for the entire administrative infrastructure. The use of a single password is the most prevalent security. shortcut that is seen today.
- Use centralized authentication management. Directory services or other types of centralized authentication mechanisms can make password and access control management far more feasible for large environments.
Organizations with significant back door security vulnerabilities, as discussed in this article, have numerous avenues for unauthorized access and abuse. While the management practices outlined above are relatively inexpensive and easy to implement, they do require regular enforcement and a strong commitment on the part of management to provide oversight and, if required, disciplinary action.
This article was written by Contributing Research Analysts Ron Collette, CISSP and Mike Gentile, CISSP. They are authors of The CISO Handbook: A Practical Guide to Securing Your Company, published by Auerbach. For more information, please visit http://www.cisohandbook.com.
For more complete analysis of current trends IT security spending, staffing, technology, and management best practices, please refer to the Computer Economics IT Security Study.


