Too many companies fail when it comes to taking basic steps to prevent security incidents, even in the face of catastrophic cyberattacks. Nowhere is that more evident than with IT security compliance audits.
As shown in Figure 3 from our full report, IT Security Compliance Audit Adoption and Best Practices, it is alarming that only 42% of respondents conduct security audits formally and consistently.
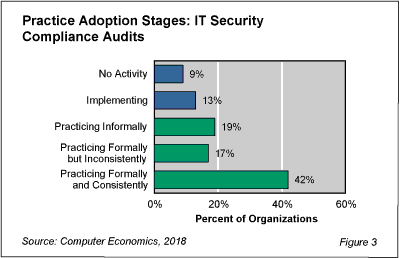
Security compliance audits involve periodically auditing users and IT staff to ensure that security policies and procedures are followed. This best practice is a mandate for every organization, particularly those managing personal information such as patient healthcare records and those processing credit card and other financial transactions. Having robust security policies and practices in place is of little value if they are not enforced. Among other benefits, audits help ensure that employees do not create security risks by violating policies and procedures. Periodic training, including refresher exercises, is a best practice in enforcement of security policies.
Many organizations have learned the hard way that establishing security policies and implementing the best security technology is not enough. Follow-up to be certain that these standards are being maintained is equally, if not more, important. This is where the IT security compliance audit comes into play.
“Many companies think their IT security is up to snuff, but unfortunately too many of them are not consistently using the most important security best practices, such as compliance audits,” said Tom Dunlap, director of research for Computer Economics, based in Irvine, Calif. “With this track record, is it any wonder we keep getting hit with security debacles like Equifax and Uber? Companies need to wake up and smell the compliance.”
As security gets more complex, and enterprises face a wider array of threats, reinforcing existing policies and procedures can go a long way to protecting an enterprise. In the full study, we first look at adoption trends for IT security compliance audits by organization size and sector. We also discuss the steps an IT organization should take to implement such audits. Finally, we provide recommendations for monitoring the success of security audits.
This Research Byte is a brief overview of our report on this subject, IT Security Compliance Audit Adoption and Best Practices. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

