IT security training is a business best practice that involves training all IT and user personnel in a company’s security policies and procedures. This increases awareness and ensures compliance, making it a highly advisable practice for every company. However, too many adopters are only conducting security training in an inconsistent manner, which can have dire consequences.
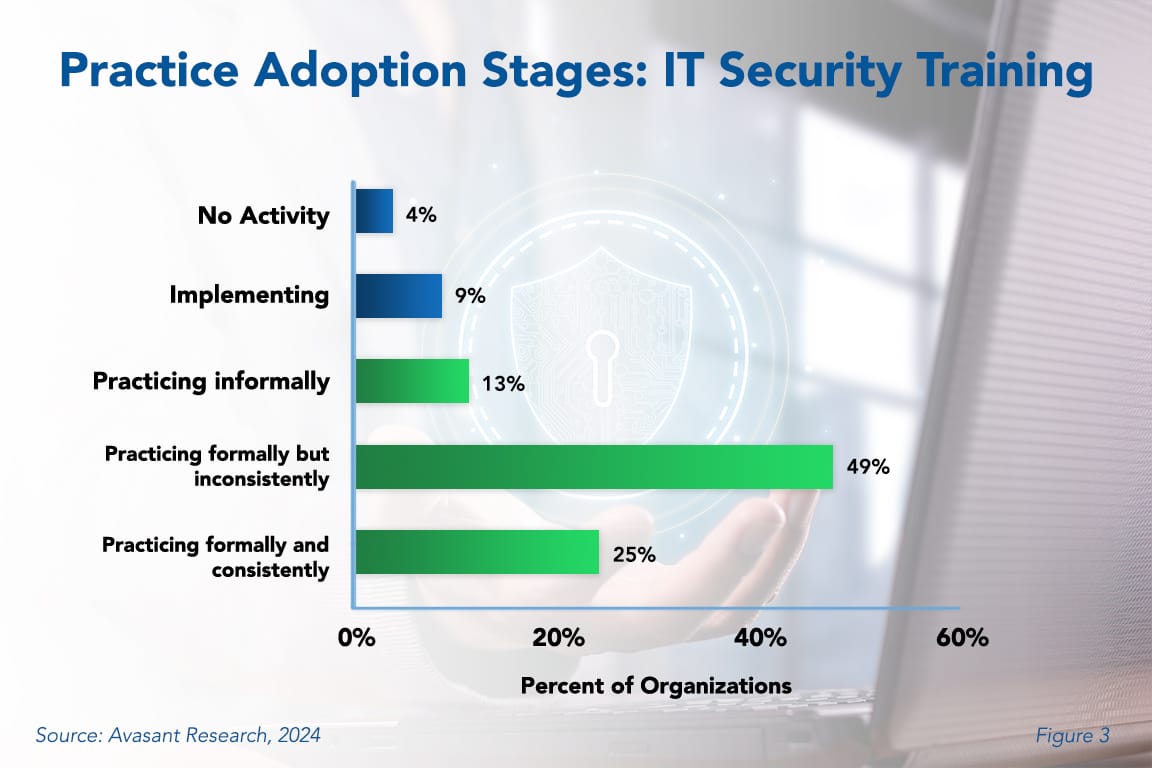
As shown in Figure 3 from our full report, IT Security Training Best Practices, only 25% of our survey respondents indicate that they conduct IT security training formally and consistently, while 49% practice it formally but inconsistently, and 13% practice it informally. Another 9% of survey respondents are still implementing security training for the first time. The remaining 4% admit that they do not conduct IT security training at all.
Security policies must be supported by formal and consistent training of staff on the various threats they may face, how they should respond, and what the company expects of them in terms of compliance. Training helps ensure that employees do not create vulnerabilities by neglecting policies and procedures or by taking shortcuts.
To ensure formal and consistent training of all IT personnel and employees in a company’s security policies, procedures, and best practices, a set of questions must be answered. Our full report provides a suggested list of self-assessment questions to help you and your organization determine if your security training program needs improvement.
“Security policies and procedures are ineffective unless constantly updated and renewed,” said Reneece Sterling, senior research analyst for Avasant Research, based in Los Angeles. “Training should be continuous to match the ever-changing threat landscape.”
Security training has a moderate maturity rating this year relative to the other practices in the IT Management Best Practices study. However, the number of survey respondents consistently and formally conducting security training falls far short of the number practicing it to some degree. Thus, existing training programs should be evaluated to determine how they can be improved.
In our full report, we study the adoption and practice levels for security training and examine those by organization size and sector. As noted previously, we also include a set of self-assessment questions and conclude with recommendations to effectively carry out security training.
This Research Byte is a brief overview of our report on this subject, IT Security Training Best Practices. The full report is available at no charge for subscribers, or it may be purchased by non-clients directly from our website (click for pricing).


