IT security is a major focus for IT leaders, and that is unlikely to change in the near future. The threat landscape continues to evolve with greater diversity in the IT service portfolio, more employees working from home, and a more burdensome regulatory environment. To combat these threats, organizations are turning to IT security outsourcing firms to handle higher-value security tasks.
As shown in Figure 1 of our full report, IT Security Outsourcing Trends and Customer Experience, the net growth rate for IT security outsourcing is moderate. This indicates that more businesses are making use of external IT security providers at a rapid rate and explains why volatility is high. Most organizations want to increase their outsourcing to respond to a wider variety and complexity of threats. However, cost and service success metrics due to this outsourcing are low.
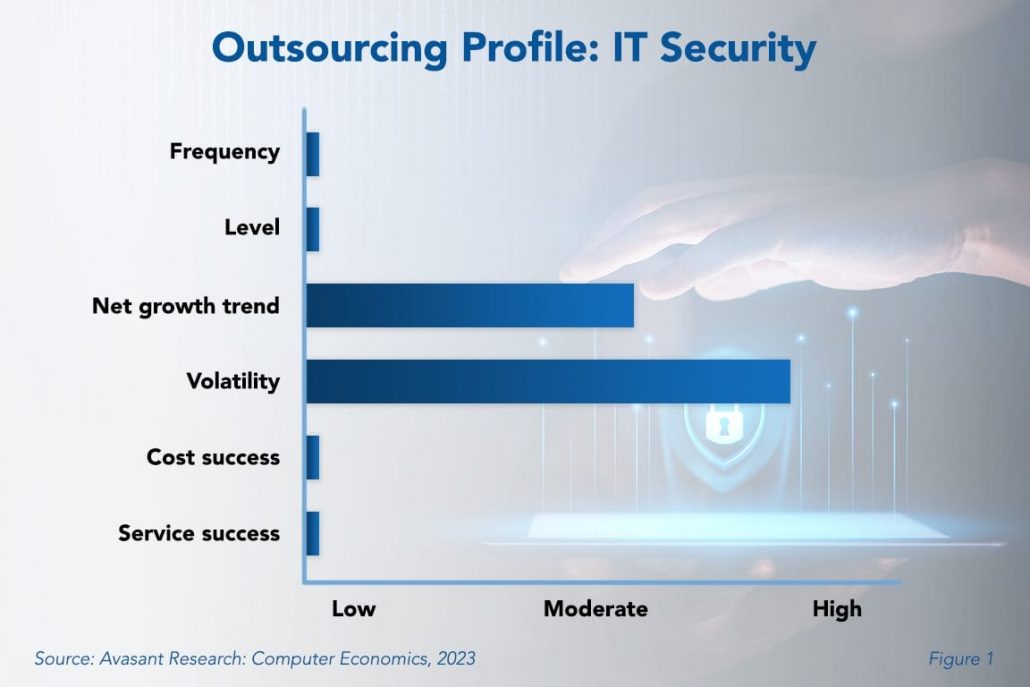
When it comes to IT security outsourcing, companies typically focus on providing good service at the expense of cost savings. However, we see a reduction in service success as well. In the past, service success was higher, leading us to conclude that outsourcing allowed enterprises to tap into specialized skills. But, automation, monitoring technology, and possibly an increase in the number of cybersecurity professionals may be changing the experience.
Nevertheless, recent trends tell us that enterprises have the right idea, are aware of the challenges with service, and are attempting to address them accordingly. For example, many service providers now offer levels of third-party support akin to a CISO in the form of CISO as a service. They can now support end-to-end security requirements, from devising a strategy to managing operations and implementation services. As such, more businesses are utilizing these additional services.
Furthermore, organizations originally opted for pricing models that included a fixed rate. This implied availing a single service with specific features at a single price. However, to account for service uncertainties, more organizations are beginning to use the hybrid service-oriented model. With this approach, businesses can take advantage of varying prices from service providers. Between the constantly changing landscape and the efforts by service providers, we can still expect IT security outsourcing to maintain strategic value in the coming years.
“Many organizations are unable to do an adequate job securing the enterprise without external assistance and specialized talent,” said Waynelle John, research analyst for Computer Economics, a service of Avasant Research based in Los Angeles. “Although we may see new trends and fluctuations in service success, companies will always seek help when needed.”
Despite the general growth, some factors keep this outsourcing percentage from rising much further. One is that security is not a discrete function. It is intertwined with other functions, such as application development, and is embedded in the network and even end-user support operations. Organizations cannot outsource all their IT security to a service provider because security is a mandate of nearly every IT function. A company can hire someone to conduct penetration testing or employee training as an aspect of security. However, if an organization outsources network security to a service provider, the in-house network staff must still be highly skilled in security for the network to be safe.
In the full study, we present data about the five-year trend in IT security outsourcing. In light of the current trends, this study is designed to help IT executives compare their outsourcing activity and experience with other IT organizations. We use six main metrics to measure IT security outsourcing activity: how many organizations outsource their IT security (frequency), how much of the workload is typically outsourced (level), the change in the amount of work being outsourced (trend and volatility), and the cost and service experiences. We also determine how outsourcing activity and experience vary by organization size and sector. We conclude the study with ways to capitalize on the evolving trends in IT security outsourcing.
This Research Byte is a brief overview of our study, IT Security Outsourcing Trends and Customer Experience. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).


