Encryption is a best practice for protecting sensitive information, yet far too many companies are lackadaisical when it comes to encrypting data. Their neglect is a prescription for disaster, as many have learned—most notably Equifax in 2017.
Companies that do not routinely encrypt sensitive data face ugly consequences: Unauthorized individuals might steal data in compromised accounts and gain access to unencrypted data. That is why encryption is often mandated by security regulations.
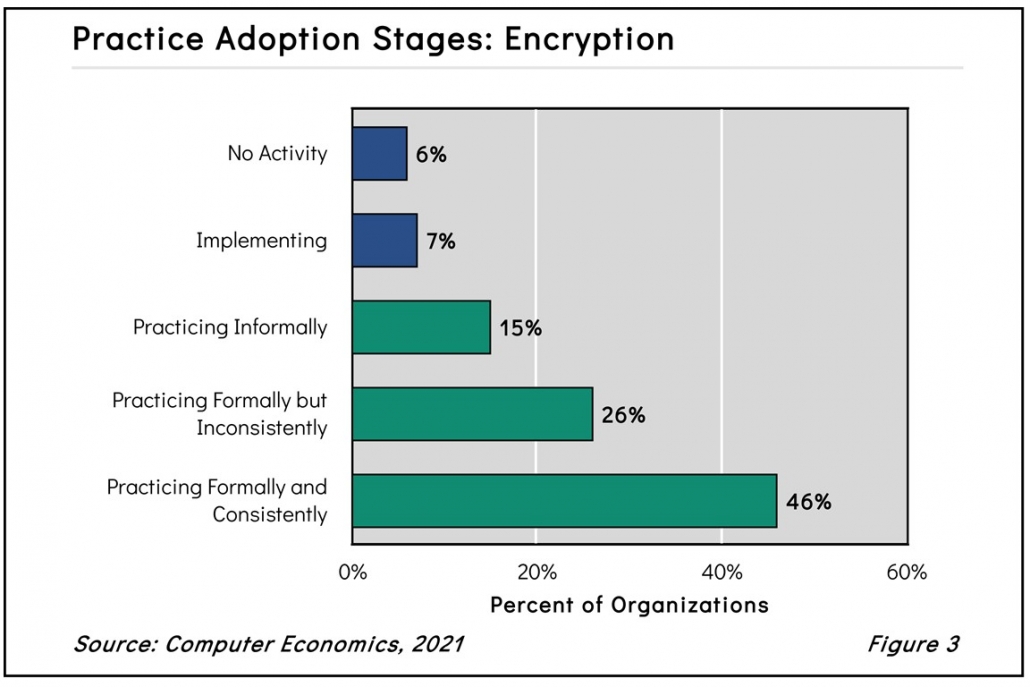
As shown in Figure 3 from our full report, Encryption Adoption and Best Practices, 15% of our survey respondents encrypt data informally, while 26% do so formally but inconsistently. This may mean that they only encrypt data in certain applications, for certain personnel, or in specific locations but not others. Whatever the reason for inconsistency, this is an area of concern for executives determined to close the door to cybercriminals. The fact that only 46% practice encryption formally and consistently is surprising.
“Encryption is not something where you can just set it and forget it,” said Tom Dunlap, director of research for Computer Economics, a service of Avasant Research, based in Los Angeles. “An organization’s systems are constantly changing, and it’s very easy for new systems to go into production with unencrypted datasets. So you have to periodically audit for compliance.”
Data theft is very much on the rise. Each year, hundreds of millions of sensitive personal records are exposed by hackers and cybercriminals. Encryption is regarded as an essential security control and part of a company’s security policies and procedures. It is an advisable practice for every organization, especially those processing personal information or other highly confidential data.
Take the case of the Equifax breach in 2017, which serves as an example of encryption inconsistency. The device inspecting encrypted traffic was misconfigured, because the digital certificate had expired almost a year previously. This was one of the vulnerabilities that enabled hackers to compromise the personal information of 155 million people, leading to massive consequences not only for those whose information was compromised, but also for Equifax and its senior leadership, many of whom were terminated.
Another area of inconsistency relates to where encryption is performed. Data is at risk when it is at rest in a database or storage repository and also when it is in transit over a network. Consistent encryption requires the protection of data in both states. Yet some companies only encrypt data in one of these states, potentially exposing their data to attack.
The full report begins with a definition of encryption. We next study the adoption and practice levels and examine those by organization size and sector. We conclude with best-practice recommendations.
This Research Byte is a brief overview of our report, Encryption Adoption and Best Practices. The full report is available at no charge for Avasant Research subscribers or may be purchased directly from our website (click for pricing).


