Supply chain vulnerabilities are a new front in the cybersecurity battlefield brought about by the interconnection of people, technology, and business processes. The interconnectedness presents a double-edged sword for enterprises: efficiency vs exploitable vulnerabilities. A single cyberattack can trigger a cascade of disruptions, leaving businesses scrambling and consumers facing empty shelves. Business leaders need to dig deep and understand cybercriminals’ strategies to target supply chains and implement solutions to mitigate risks.
The Evolving Threat Landscape
The digital world is an interconnected space constantly on the defence to brace the daily cyber threats. While the number of reported cyber incidents remains a critical metric, it may be significantly underestimating the true threat landscape. A widening gap between reported complaints and actual losses exposes a disturbing trend: cyberattacks are becoming more sophisticated and destructive.
In 2023, the FBI Internet Crime Report (IC3) recorded that the total financial losses from cybercrime over the past five years have surpassed $35 billion. Conversely, the report reflects less than 4 million official complaints filed during the same period. While this data is based on complaints filed with the IC3, it likely represents a fraction of total global losses. This significant discrepancy underscores a concerning reality that organizations are under-reporting cyberattacks or falling victim to a new breed of attacks that are more difficult to detect and contain.
Attackers are increasingly recognizing the strategic advantage of exploiting vulnerabilities within supply chains. Therefore, there are several factors contributing to the evolving threat landscape:
Increased Attack Surface
New technologies like AI and IoT can produce vast attack surfaces. But the supply chain, by its nature, self-imposes an increasing attack surface. Every vendor in the supply chain is a crossroad, linking to other routes and providing a plethora of opportunities for malicious actors to enter the system. The supply chain’s attack surface thus grows exponentially. As additional manufacturers and partners join the network, its complexity rises. As a result, it becomes more challenging to monitor and secure each intersection. By taking advantage of a small vendor, one may have access to the larger network.
Lack of Visibility and Control
Identification and remediation of vulnerabilities are challenging because organizations sometimes lack comprehensive insight into the security procedures of their providers. Vulnerabilities may go undiscovered and lead to exploitable holes in the supply chain if there is a lack of clarity on the security controls, patch management procedures, and incident response methods of suppliers. Shadow IT within vendor networks, obsolete software, and unmonitored devices are all concealed tripwires in the maze, ready to stymie security attempts. Furthermore, monitoring sensitive data via complicated supply chain operations becomes a guessing game, raising the risk of exposure and possible breaches.
Cascading Impact
A break in one part of the supply chain can have repercussions for the whole ecosystem, upsetting business processes and resulting in serious financial and reputational harm. If there is a vulnerability anywhere in the supply chain, an attacker can access vital infrastructure, data, or systems. Once inside, through compromised access points, intruders spread laterally and deeply penetrate linked networks and systems. Production lines stop, critical data is encrypted or leaked, and operational systems come to a complete stop, severely impairing the operations of several businesses. Products being out of stock, delivery delays, money losses, and declining consumer confidence are all examples of how the domino effect may affect any link in the chain.
What are some best practices to mitigate the risks of this evolving landscape?
Mitigating Risks/Best Practices
Organizations must adopt a proactive approach to supply chain cybersecurity to navigate this complex landscape. Therefore, we recommend the following framework of best practices for evaluating and mitigating risks:
Invest in Security
Effective cybersecurity frameworks go beyond simply outlining policies and procedures. A core tenet is prioritizing investment in security measures to fortify an organization’s security posture. This prioritization is driven by the escalating threat landscape. Organizations across various sectors recognize the importance of allocating resources toward security when making new IT spending decisions.
As illustrated in Figure 2 from Avasant’s IT Security, Cybersecurity, and Compliance Spending and Benchmarks report, security spending is categorized into six key areas. Notably, information security/privacy stands out as the top priority, with 87% of organizations increasing their spending in this area. This trend is likely driven by the escalating prevalence of security threats in recent years. High-profile incidents involving information theft, ransomware attacks, and business disruptions caused by targeted attacks have demonstrably heightened security awareness.
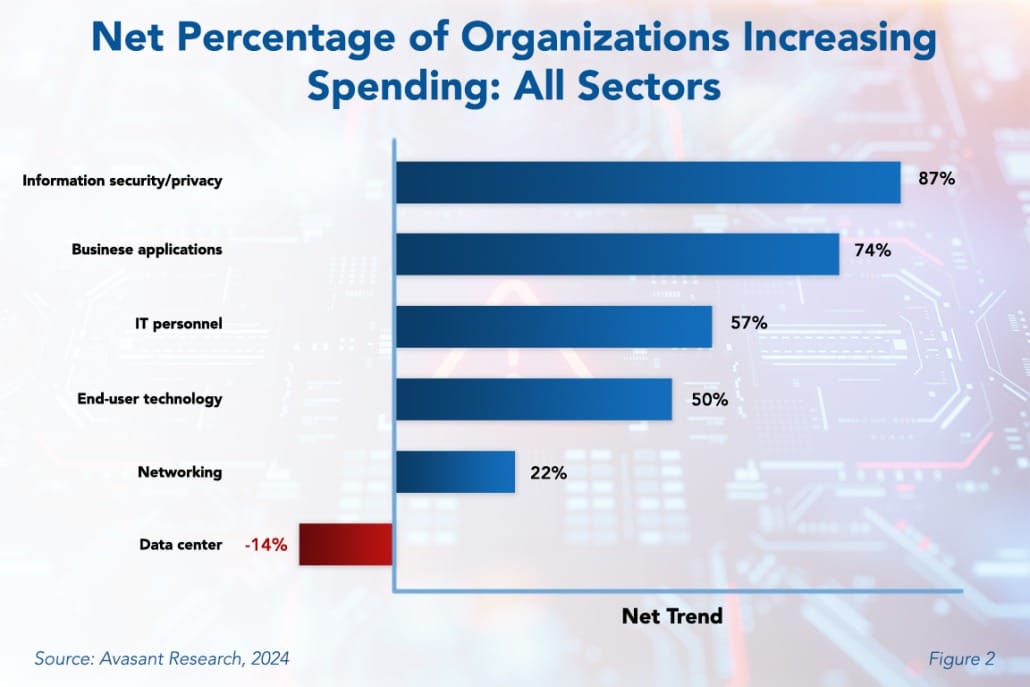
Strategic security investment will enhance an organization’s threat detection and response, improve staff training and awareness, regularize security assessments and penetration testing, maintain a robust security infrastructure, and stay current with evolving threats. By allocating resources for security, organizations can significantly augment their ability to defend against cyber threats and protect their critical assets.
Risk Assessment
-
- Vendor and Partner Evaluation: Conduct thorough risk assessments of every vendor’s and partner’s security posture. This should include evaluating their:
- Security controls and infrastructure
- Data governance policies and procedures
- Incident response capabilities and communication protocols
- Patch management practices
- Penetration testing and vulnerability management programs
Particular focus should be placed on the security controls implemented by third-party logistics providers and cloud service providers that handle sensitive data.
-
- Threat Modelling: Develop a comprehensive threat model that considers critical assets, potential attack vectors and attackers, vulnerability points within your supply chain ecosystem, and the potential impact of different attack scenarios.
Following the acquisition of Starwood Hotels in 2014, unauthorized actors accessed guest reservation information. This intrusion remained undetected for approximately four years until a security researcher identified the breach. In response to the incident, Marriott implemented a security framework to enhance its overall security posture. This framework focused on conducting more comprehensive security assessments during acquisitions, aiming to prevent similar occurrences in the future.
Contractual Provisions
-
- Robust Cybersecurity Clauses: Do not rely on boilerplate language. Integrate clear and enforceable cybersecurity clauses into all vendor and partner contracts. These clauses should address:
- Data security protocols, including data encryption and access controls
- Incident reporting requirements, outlining timelines and communication protocols in case of a breach
- Vulnerability disclosure protocols, ensuring prompt notification of any discovered vulnerabilities within their systems
- Right to Audit: Ensure contracts grant your organization the right to conduct periodic security audits of vendors and partners to verify compliance.
It’s important to note that even the most robust clauses can’t guarantee complete protection. However, by incorporating stronger cybersecurity measures and audit rights into agreements, companies can significantly improve their overall security posture and hold vendors accountable for data protection.
Continuous Monitoring
-
- Proactive Threat Detection: Reactive measures are insufficient. Implement solutions to continuously detect and monitor potential vulnerabilities and security threats across the supply chain. This might involve deploying security information and event management systems or leveraging specialized threat intelligence feeds. This will allow for the identification and mitigation of potential vulnerabilities and security incidents across the supply chain before they can be exploited.
- Penetration Testing: Regularly conduct penetration testing of your own systems and, where possible, collaborate with vendors to perform penetration testing of their systems.
Equifax suffered a data breach in 2017, exposing the personal information of nearly 150 million Americans. Attackers exploited a known vulnerability in a web browser component that Equifax failed to patch. The breach went unnoticed for months until a researcher alerted the company. Equifax mitigated this by tightening its vulnerability management practices, prioritizing timely patching, and adopting a more proactive approach to security. Additionally, it revamped its incident response plan to ensure faster detection and containment.
Collaboration and Communication
-
- Open Communication Channels: Adopt open communication channels and collaboration with vendors and partners to exchange threat intelligence, best practices, and incident response protocols.
- Joint Working Groups: Consider establishing joint working groups composed of representatives from your organization and key vendors to collaborate on supply chain security initiatives and threat mitigation strategies. Collaborative exercises like tabletop simulations can further strengthen preparedness for potential cyberattacks.
Capability Building
-
- Security Awareness Training: To foster a culture of security awareness, invest in upskilling your staff on supply chain cybersecurity threats and best practices to identify and mitigate social engineering attempts, phishing attacks, and other threats targeting the human element of the supply chain. This can involve conducting security awareness training programs, sponsoring cybersecurity certifications, and establishing internal knowledge-sharing initiatives.
- Supply Chain Security Expertise: Consider building in-house expertise in supply chain cybersecurity or partnering with external consultants who can provide specialized guidance and support.
In 2020, hackers infiltrated SolarWinds’ systems and injected malicious code into a software update. This update was downloaded by thousands of customers and provided a backdoor to attackers into their systems. A security patch to remove the backdoor was only issued when security researchers noticed unusual activity. To mitigate this, SolarWinds implemented stricter security measures for their software development process, including multifactor authentication and code signing. They also increased transparency and communication with their customers about security vulnerabilities. Also, SolarWinds started working more closely with their vendors to ensure strong security practices throughout the supply chain.
It’s not only an IT problem; supply chain security is essential for business. Organizations must safeguard their valuable assets and resources, uphold consumer confidence, and guarantee sustainable digital growth by investing in cybersecurity solutions and cultivating a security-aware culture. In the digital age, supply chain cybersecurity concerns pose a serious business problem. However, companies can develop safe and resilient ecosystems that can endure the changing threat landscape by taking a proactive approach, assessing and reducing risks, and implementing best practices. In today’s interconnected world, supply chain cybersecurity is a top priority for organizations to ensure the integrity and continuity of their core operations.
By Tracell Frederick, Managing Consultant


