In assessing risks to their organizations’ information and systems, information technology security professionals face an evolving array of threats. Last year’s defenses may not be adequate to counter the threats of this year’s attacks. Therefore, it is important for executives to have an awareness of the seriousness of each type of IT security risk and how threat levels are changing.
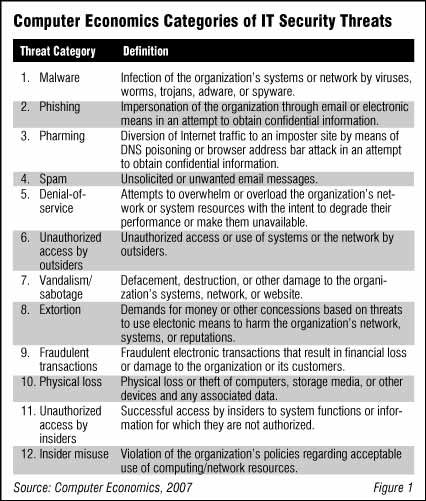
This article is an executive summary of our full report, Trends in IT Security Threats: 2007, which analyzes the 12 categories of computer security threats as shown in Figure 1.
For each category, the full report analyzes the perceived seriousness of each category of computer crime and how threat levels have changed in the last 12 months. In addition, we provide high level statistics on the number of incidents reported for each category.
This information technology risk assessment is based on a survey of over 100 IT security and risk management professionals, conducted by Computer Economics in the fourth quarter of 2006.
Summary of Major Findings
Analysis of these survey results provides insights into how IT professionals perceive the seriousness of 12 categories of information security threats and how these threat levels are changing. Some of these results are encouraging, but some may indicate a gap between perception and reality.
- Insider threats are the highest-ranking IT security concern. Insider misuse and unauthorized access by insiders are considered the top two IT security threats by our survey respondents. Inasmuch as the greatest risk to the organization resides with those inside the security perimeter, this perception is warranted.
- Spam follows closely behind insider threats as a category of concern. This may be attributed to the prevalence of spam, the fact that spam is highly visible to everyone in the organization, including executives, and that spam serves as a vector for many other types of attacks. The majority believe that the spam threat is increasing, not decreasing.
- In spite of advances in technology to fight malware–computer viruses, worms, trojans, adware, and spyware–malware still ranks highly in the list of concerns. There is significant variation between organizations in terms of the frequency of malicious code attacks, most likely due to variation in how well organizations defend against such security events.
- Unauthorized access by outsiders is ranked only slightly behind malware in terms of seriousness. It is quite possible, however, that in some organizations, hackers have obtained unauthorized access without the awareness of the organization. Hence, the number of hacking incidents is likely underreported in the statistics.
- Although IT security professionals take the threat of physical loss or theft of computer hardware and storage somewhat seriously, a significant number think it is only a minor threat. This is somewhat surprising in light of the number of respondents who report such incidents in the past year.
- Although many organizations are experienced in fighting electronic fraud, survey respondents rank fraud in the middle of the list of security concerns. These results most likely reflect the fact that many high-risk organizations, such as banks and financial institutions, believe that their countermeasures are adequate to keep the level of fraud within acceptable levels.
- We find that IT security professionals are not sufficiently worried about the threat of pharming attacks. Similarly, we do not find very high levels of awareness of the threat of phishing, at least among respondents outside of the financial services sector.
- Most IT security professionals and managers do not view electronic vandalism/sabotage as a serious threat. Such computer crimes in the past were motivated by a desire to gain bragging rights among hackers, while today such acts are more likely to be motivated by a desire to get revenge, to make a political statement, to conduct cyber-terrorism, or to wage electronic warfare. The degree of concern about threats is largely dependent on whether the organization has experienced such an attack in the past.
- IT professionals vary considerably in their perception of the seriousness of denial of service (DoS) attacks. This disparity is most likely due to the variation in the “attractiveness” of the organizations in our sample as targets. However, it appears that many organizations are complacent concerning this threat.
- Extortion by electronic means ranks last in the list of IT security concerns. This is most likely because of the infrequency of such attempts. Therefore, it is not surprising that most IT security professionals do not consider extortion a serious threat. However, because most organizations shun this type of publicity, it is likely that respondents are underreporting the number of extortion attempts by cyber-criminals.
The full report describes these trends and information security statistics in more detail, including the relationships between various types of computer security threats. For each category, we analyze current perceptions of the threat level and how the threat level has changed in the past 12 months. We also analyze the connection between reported number of IT security events and the perceptions of threat levels. Differences in responses based on industry are noted where significant.
Demographics
Although responses to this survey were received from organizations on every continent, the majority of participants (67%) are based in the U.S. and Canada. Asia and Australia account for 12% of the responses, followed by Europe at 10%. Africa and Central/South America together account for 11% of the responses.
In terms of industry sectors, banking and finance organizations have the largest representation in our sample at 14%. Government and high tech organizations are also well represented, at 11% and 10% respectively. The rest of the participants are from a wide variety of industry types. Job responsibilities of respondents include information security (infosec) management positions such as Chief Security Officer (CSO) and Chief Information Security Officer (CISO); infosec technical professionals; IT management positions, such as CIO; risk management positions, and other executive positions with direct knowledge of their organizations’ IT security experiences.
In selecting the sample for this survey, we paid special attention to the size of the organization, so that the respondents would be dominated by companies with over 100 employees. The largest group comprises organizations with 100 to 1,000 employees (38%). Nearly 30% of the respondents come from organizations with 1,000 to 5,000 employees. Another 20% of the respondents come from companies with over 5,000 employees. Organizations with less than 100 employees only comprise 13% of the sample.
Table of Contents
- Executive Summary
- Overview of IT Security Threats
IT Security Threat Categories
The Relative Seriousness of IT Security Threats
Changes in Threat Levels in Past 12 Months
-
Security Threat Trends by Category
Malware Attacks
Phishing Attacks
Pharming Attacks
Spam
Denial-of-Service Attacks
Unauthorized Access by Outsiders
Vandalism and Sabotage
Extortion
Fraudulent Transactions
Physical Loss of Computing Devices or Storage Media
Unauthorized Access by Insiders
Insider Misuse
- Demographics
List of Figures
Figure 1: Computer Economics Categories of IT Security Threats
Figure 2: IT Security Threats Ranked by Seriousness
Figure 3: Change in Threat Levels Over Past 12 Months
Figure 4: Seriousness of Malware Attacks
Figure 5: Malware: Change in Threat Level in Past Year
Figure 6: Seriousness of Phishing Attacks
Figure 7: Phishing: Change in Threat Level in Past Year
Figure 8: Seriousness of Pharming Attacks
Figure 9: Pharming: Change in Threat Level in Past Year
Figure 10: Seriousness of Spam Attacks
Figure 11: Spam: Change in Threat Level in Past Year
Figure 12: Seriousness of Denial of Service Attacks
Figure 13: Denial of Service: Change in Threat Level in Past Year
Figure 14: Seriousness of Unauthorized Access by Outsiders
Figure 15: Unauthorized Access by Outsiders: Change in Threat Level in Past Year
Figure 16: Seriousness of Vandalism/Sabotage
Figure 17: Vandalism/Sabotage: Change in Threat Level in Past Year
Figure 18: Seriousness of Extortion Attempts
Figure 19: Extortion Attempts: Change in Threat Level in Past Year
Figure 20: Seriousness of Fraudulent Transactions
Figure 21: Fraudulent Transactions: Change in Threat Level in Past Year
Figure 22: Seriousness of Physical Loss of Computing Devices and Storage
Figure 23: Physical Loss: Change in Threat Level in Past Year
Figure 24: Seriousness of Unauthorized Access by Insiders
Figure 25: Unauthorized Access by Insiders: Change in Threat Level in Past Year
Figure 26: Seriousness of Insider Misuse
Figure 27: Insider Misuse: Change in Threat Level in Past Year
Figure 28: Respondents by Location
Figure 29: Respondents by Industry
Figure 30: Respondents by Number of Employees
April 2007
This Research Byte is a brief overview of our report on this subject, Trends in IT Security Threats: 2007, which provides useful input to an organization’s overall information security risk management program. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website at https://avasant.com/report/trends-in-it-security-threats-2007/ (click for pricing).


