Reports
Showing 1681–1696 of 4763 results
-
![Two-Factor Authentication Among Least Mature Best Practices Top 10 Best Practices - Two-Factor Authentication Among Least Mature Best Practices]()
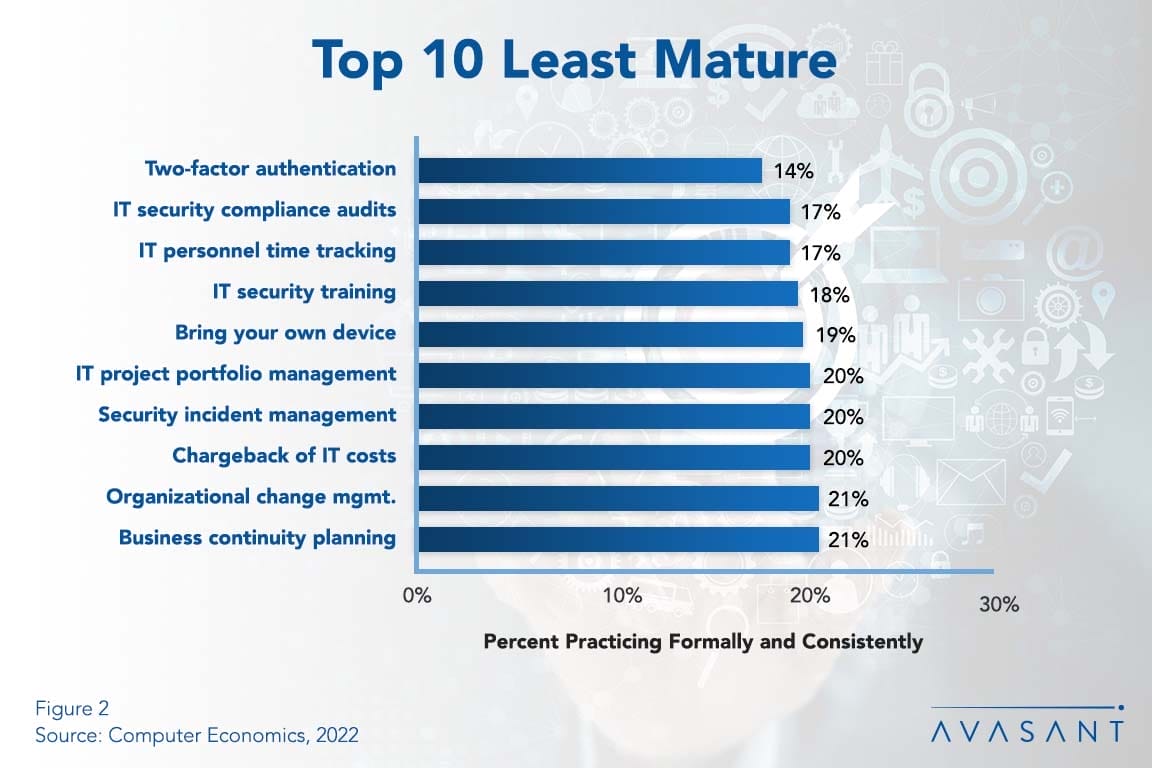
Two-Factor Authentication Among Least Mature Best Practices
Computer Economics has released its major annual study on 33 IT management best practices, with two-factor authentication topping our list of least mature practices. This Research Byte highlights some of our findings on the least mature practices, along with an overview of the contents of the full study. The full study analyzes the growth and maturity of all 33 best practices, which are grouped into five major categories: IT governance, IT financial management, IT operational management, IT security and risk management, and application development.
March, 2022
-
![IT Management Best Practices 2022 Sample Pages Product Cover Page Example - IT Management Best Practices 2022 Sample Pages]()
IT Management Best Practices 2022 Sample Pages
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 33 IT management practices, which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices. (196 pp., 178 figs.)
March, 2022
-
![IT Management Best Practices 2023 Sample Pages Product Cover Page Example 2023 - IT Management Best Practices 2023 Sample Pages]()
IT Management Best Practices 2023 Sample Pages
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 35 IT management practices, which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices.
March, 2023
-
![IT Management Best Practices 2022 Top 10 Best Practices - IT Management Best Practices 2022]()
IT Management Best Practices 2022
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 33 IT management practices, which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices. (196 pp., 178 figs.)
March, 2022
-
![IT Management Best Practices 2023 Digital Workplace RB IT best - IT Management Best Practices 2023]()
IT Management Best Practices 2023
The best-run IT organizations not only focus their process improvement efforts on those of other departments, they also seek to optimize their own IT management processes internally. In this study, we examine the growth and maturity of 35 IT management practices, which we have grouped into five major categories: IT governance practices, IT financial management practices, IT operational management practices, IT security and risk management practices, and application development practices.
March, 2023
-
![Google’s Latest Move in Building Out its Security Platform Offering Google Research byte - Google’s Latest Move in Building Out its Security Platform Offering]()
Google’s Latest Move in Building Out its Security Platform Offering
The rising threat landscape has led cloud service providers to expand the scope of their cybersecurity offerings to multiple data sources and automate the triage process and incident response. This includes the use of artificial intelligence/machine learning to model the behavior of attackers and identify threats in advance. By acquiring Mandiant and Siemplify, Google is taking a big step in its vision of “invisible security” with automated threat hunting, detecting, and response. This will allow CISOs to capitalize on the SIEM-to-SOAR maturity trend for streamlining their threat response procedures.
March, 2022
-
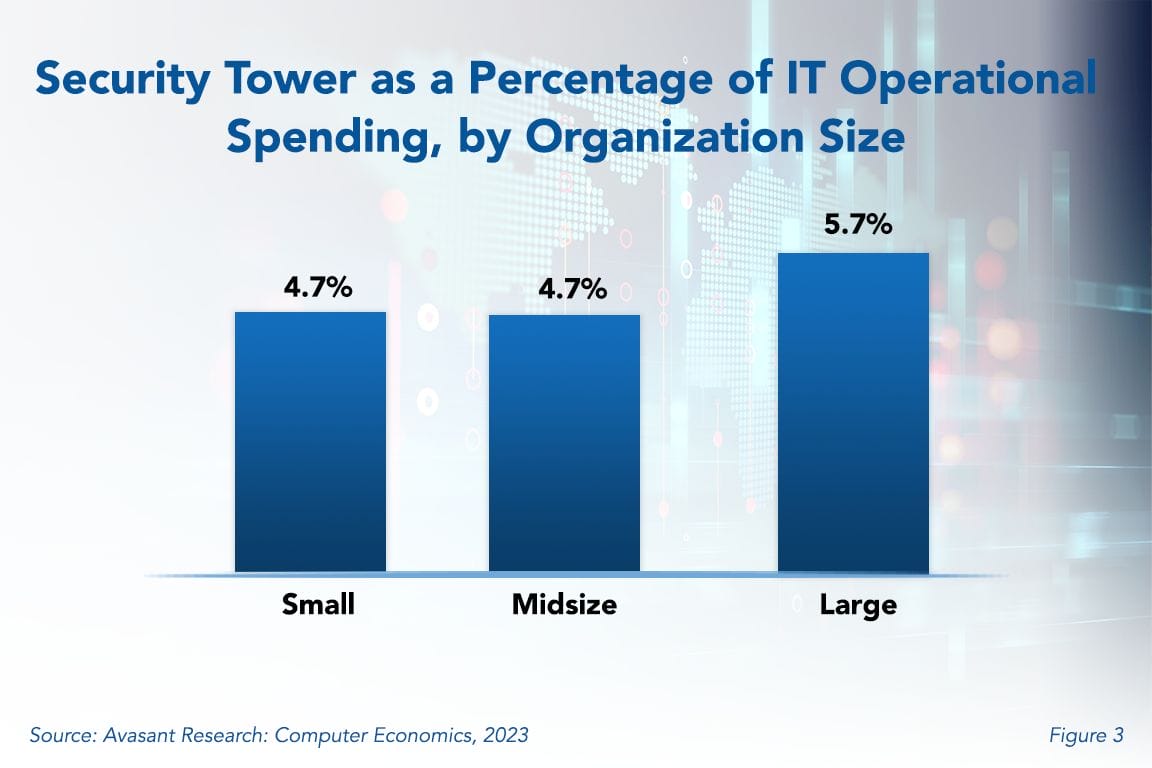
![IT Security and Cybersecurity Spending Benchmarks—Download Free Sample Pages Security Tower as a Percentage - IT Security and Cybersecurity Spending Benchmarks—Download Free Sample Pages]()
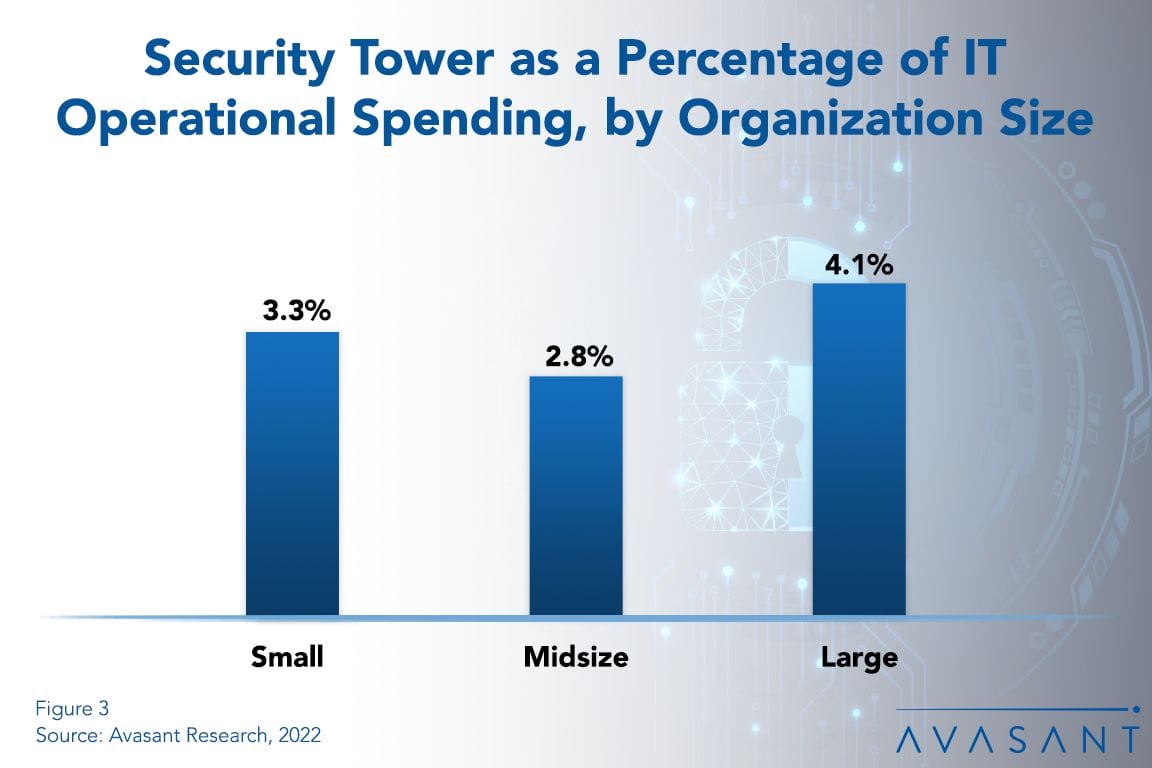
IT Security and Cybersecurity Spending Benchmarks—Download Free Sample Pages
Security and cybersecurity incidents are costly, with losses increasing every year. No wonder, then, that our research shows IT security and cybersecurity are the top priority for new IT investments year after year. But how much is enough?
June, 2024
-
![Navigating IT Outsourcing Challenges amid Russia-Ukraine Conflict PrimaryImage RussiaUkraine - Navigating IT Outsourcing Challenges amid Russia-Ukraine Conflict]()
Navigating IT Outsourcing Challenges amid Russia-Ukraine Conflict
Ukraine has looked at IT outsourcing as an important source of revenue. The current conflict will have massive repercussions on its IT industry. From the perspective of enterprise customers, unfortunately, this conflict will force them to go back to the drawing board and lay out contingency plans. They will need to find a way forward with their Ukranian service providers that is empathetic but at the same time protects customers against disruption.
March, 2022
-
![IT Quality Assurance Staffing Ratios 2022 Graph Template Quality Assurance - IT Quality Assurance Staffing Ratios 2022]()
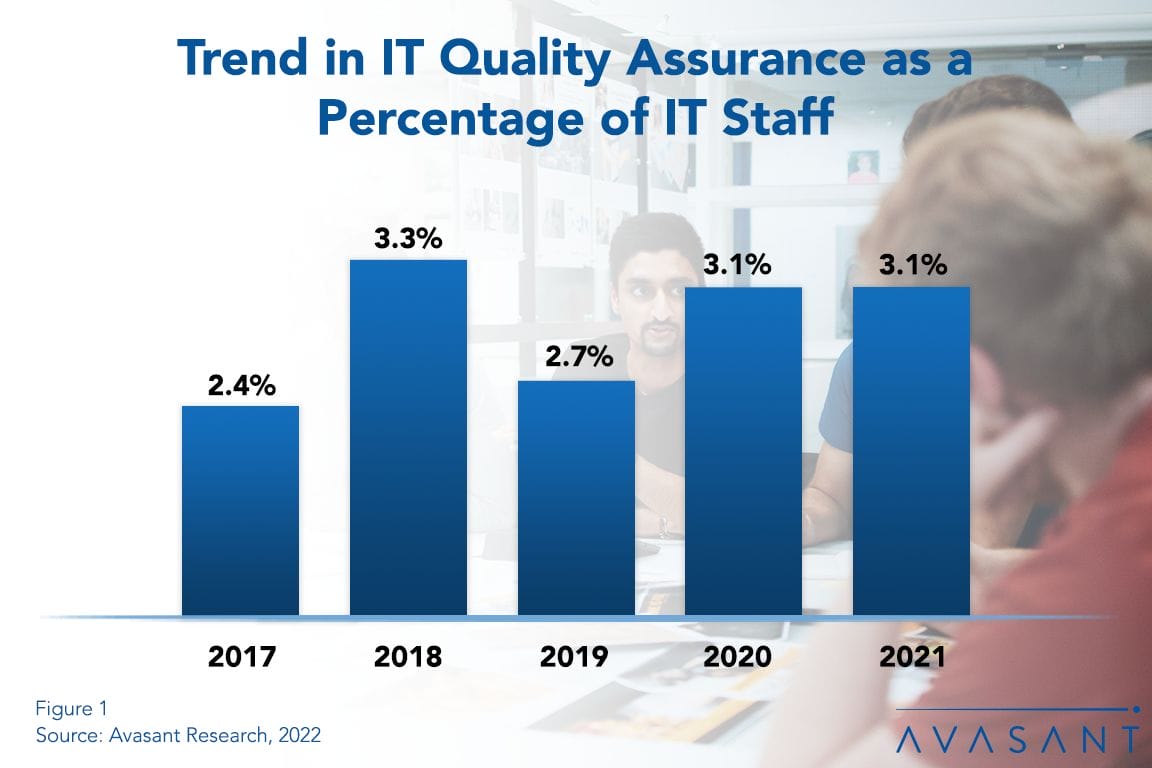
IT Quality Assurance Staffing Ratios 2022
Staffing levels for IT quality assurance personnel have been relatively steady over the past five years for several reasons, including the new ways in which software is being developed and the varying needs of industry sectors. In this report, we first evaluate recent changes in IT QA staffing levels. We then provide three benchmarks by organization size and by sector: QA staff as a percentage of the IT staff, QA staff as a percentage of the Application Group, and applications per QA staff member. We conclude with recommendations for improving the effectiveness of the QA function within the IT organization.
February, 2022
-
![New Software Development Methods Keeping QA Staff Growth in Check Graph Template Quality Assurance - New Software Development Methods Keeping QA Staff Growth in Check]()
New Software Development Methods Keeping QA Staff Growth in Check
The traditional IT position dedicated exclusively to quality assurance is most likely a dying breed. With waterfall development being replaced by iterative approaches such as agile, QA is getting rolled into other job positions. This Research Byte examines the reasons for the trend and provides a summary of our full report on IT Quality Assurance Staffing Ratios.
February, 2022
-
![Avasant Releases New Benchmarks for IT Security and Cybersecurity Spending Security Tower 2 - Avasant Releases New Benchmarks for IT Security and Cybersecurity Spending]()
Avasant Releases New Benchmarks for IT Security and Cybersecurity Spending
Security and cybersecurity incidents are costly, with losses increasing every year. In light of these growing threats, it is no wonder that organizations in all industries continually rank security as a top priority for new spending. But how much are they spending? To answer this question, we have now released our new report, IT Security, Cybersecurity, and Compliance Spending and Staffing Benchmarks.
February, 2022
-
![IT Security, Cybersecurity, and Compliance Spending Benchmarks 2022 Security Tower 2 - IT Security, Cybersecurity, and Compliance Spending Benchmarks 2022]()
IT Security, Cybersecurity, and Compliance Spending Benchmarks 2022
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
February, 2022
-
![IT Security, Cybersecurity, and Compliance Spending Benchmarks 2023 IT Security Cybersecurity and Compliance Spending Benchmarks - IT Security, Cybersecurity, and Compliance Spending Benchmarks 2023]()
IT Security, Cybersecurity, and Compliance Spending Benchmarks 2023
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
May, 2023
-
![Four Technology Trends for 2022—Putting People Back in the Picture Featured Image Toms Rb - Four Technology Trends for 2022—Putting People Back in the Picture]()
Four Technology Trends for 2022—Putting People Back in the Picture
IT organizations everywhere have been tasked with leading the digital transformation. But that transformation seems pretty bleak—artificial intelligence (AI), machine learning, robotic process automation, and blockchain. Where are the people in your digital transformation? When you look back on what you accomplished in 2022, will you be able to say you made things better for your customers? How about your users?
February, 2022
-
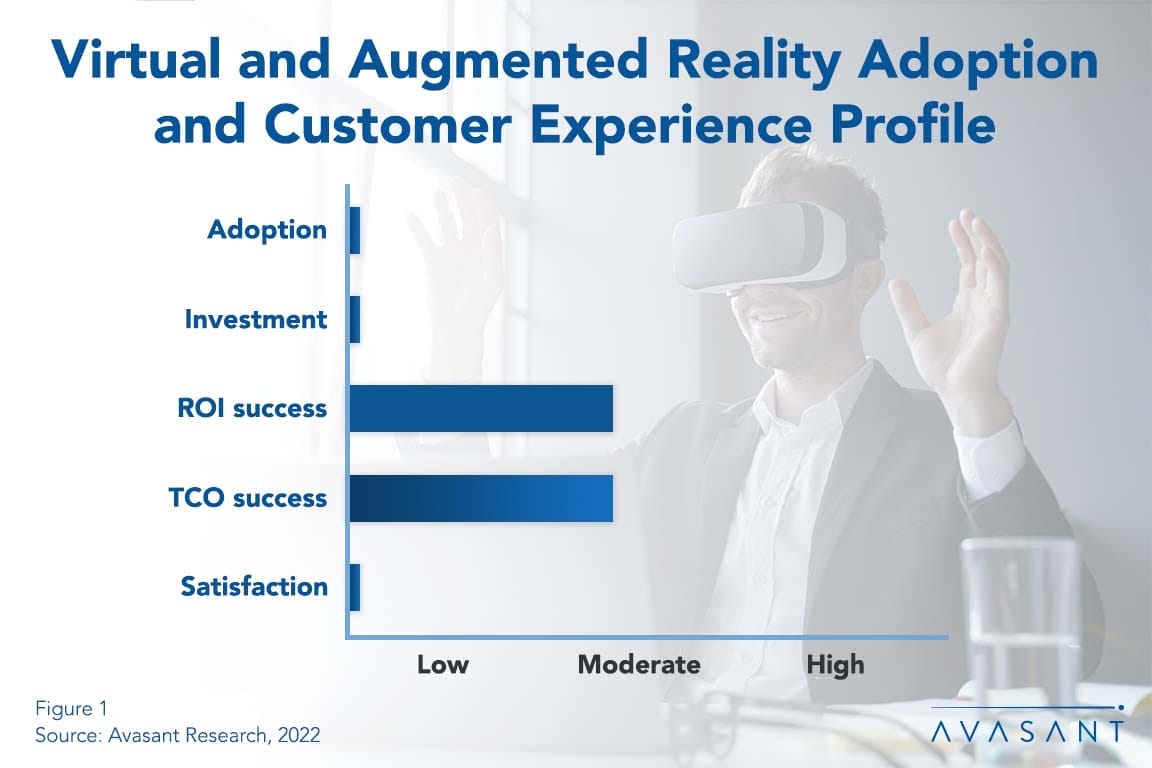
![Virtual and Augmented Reality Show Great Promise Despite Slow Mainstream Adoption VR AR - Virtual and Augmented Reality Show Great Promise Despite Slow Mainstream Adoption]()
Virtual and Augmented Reality Show Great Promise Despite Slow Mainstream Adoption
Virtual reality (VR) and augmented reality (AR) are emerging technologies that will change the nature of work in many industries. By allowing workers to map out solutions before implementing them in the real world, they minimize human errors and increase worker efficiency. They also support a hybrid work environment, as more use cases emerge for training and collaboration. This Research Byte summarizes our full report, Virtual and Augmented Reality Adoption Trends and Customer Experience.
February, 2022