In our major study of 35 IT management best practices, it is no surprise that security dominates the list of the most-mature practices. But what continues to surprise us is the low percentage of IT organizations that have adopted these crucial security practices formally and consistently. Only about half or fewer of our respondents can say they do, which means the majority of organizations need improvement in their security and risk management practices.
Figure 3 from our full study, IT Management Best Practices 2018-2019, shows that security policies tops our list of the most-mature practices, with 57% saying their security policies are formal and consistent. The fact that most organizations have IT security policies is not surprising, since such policies are often mandated by corporate policies or industry regulations. But it is disappointing that only 57% of them establish them formally and consistently. Perhaps this is one reason that we continue to see little progress against high-profile cyberattacks.
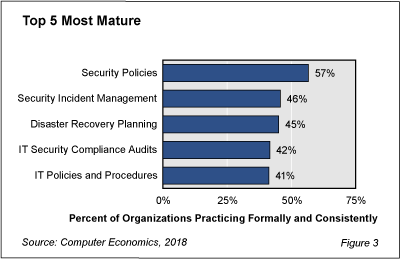
Security incident management, at 46%, is second on this most-mature list. Security incident management is a process to record, track, and resolve security breaches. When a security incident occurs, an organization will have a response team in place and clearly defined procedures for managing the incident. Security incident management is especially important for companies such as banks and retailers that hold sensitive customer information. But again, fewer than half of IT organizations formally and consistently respond to and manage security incidents.
“Maybe all the reports of security breaches are making consumers a little bit jaded,” said Tom Dunlap, director of research for Computer Economics, an Irvine, Calif.-based research firm. “Target, for example, suffered an enormous loss of consumer data in 2013. Yet, Target for the most part recovered consumer trust and financial losses within two years. Although the CEO was pushed out, it doesn’t seem like Target itself suffered any real, long-term harm. Perhaps this is why some organizations think they can get by with a lukewarm attitude toward security best practices.”
In the full study, we examine the growth and maturity of 35 IT management practices. Some of these are well-established disciplines and are widely accepted. Others are gaining traction among leading-edge organizations. Still other practices are being widely promoted by tool vendors and consultants but only rarely adopted, and it remains uncertain whether they will endure. Our goal in this study is to provide IT executives with real-world data on how widely each practice is implemented, a basis for comparing their organizations with their peers, and a means of identifying emerging best practices.
This study is now in its 14th year. Each year, we ask IT organizations in our annual survey to what extent they have adopted a selected list of IT management best practices. Survey participants have five response choices:
-
No Activity: We are not practicing this discipline in any way.
-
Implementing: We are in process of implementing this best practice.
-
Practicing Informally: We do not have formal policies or procedures for this discipline, but we do practice it in an informal or ad-hoc manner.
-
Practicing Formally but Inconsistently: We have formal policies and procedures for this discipline, but we do not follow them consistently or to the extent that we should.
- Practicing Formally and Consistently: We have formal policies and procedures for this discipline and we follow them consistently.
The best practices in the study are as follows:
-
IT governance practices: IT strategic planning, executive IT steering committee, IT project portfolio management, project management office, IT change control board, and organizational change management.
-
IT financial management practices: IT personnel time tracking, service-based cost accounting, chargeback of IT costs, showback of IT costs, IT service catalog, and benchmarking IT spending.
-
IT operational management practices: IT policies and procedures, enterprise architecture, IT Infrastructure Library (ITIL), IT asset management system, bring your own device, user-satisfaction surveying, and IT performance metrics.
-
IT security and risk management practices: security policies, data classification and retention, IT security compliance audits, security incident management, disaster recovery planning, disaster recovery testing, and business continuity planning.
-
Application development practices: system development life cycle, agile development, software change management process, DevOps, and post-implementation audits.
- Innovation practices; IT participation in business strategy, IT leadership for digital transformation, IT R&D budget, innovation/ideation portal.
This study is designed to increase the awareness of IT leaders concerning what are the best practices in IT management, provide benchmarks against which an IT organization can compare its own adoption and practice level, and justify investments to improve an organization’s IT management practices.
This Research Byte is a brief overview of our report on this subject, IT Management Best Practices 2018-2019. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

