The great majority of employees may harbor no malicious intent, but it only takes one or two to wreak havoc on an unsuspecting organization. Insiders already have physical access to the organization’s facilities, and they also have access to systems behind the organization’s firewall—a disastrous recipe. Because people within an organization pose a severe threat, implementing routine insider security risk assessments is critically important and should form an important part of the organization’s overall security program.
An insider security risk assessment is a process for understanding an organization’s level of protection and readiness to mitigate insider threats. Most IT organizations have insider security risk assessments to some extent, but too often, they are not formally established, comprehensive in their scope, or followed consistently.
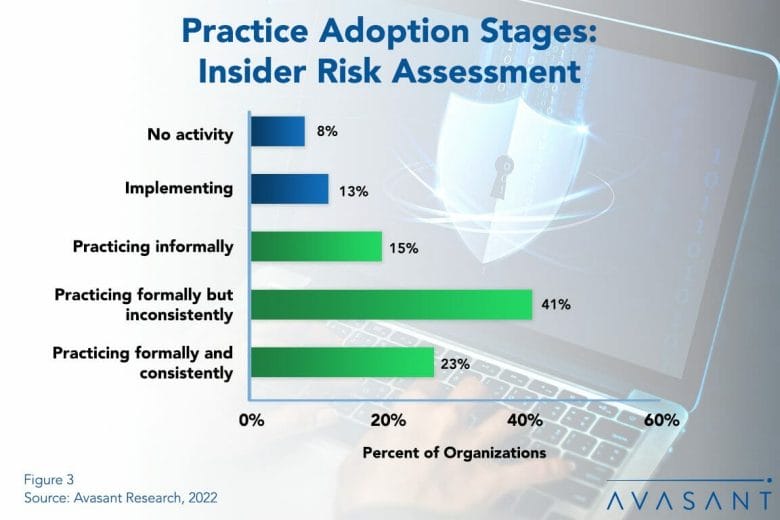
Figure 3 from our full report, Insider Security Risk Assessment Best Practices, shows where organizations are at each level of adoption. The three green bars make up the practice rate: 15% assess insider risk informally, 41% do so formally but inconsistently, and only 23% do so formally and consistently (the maturity level).
Because of this, insider threats remain prevalent and continue to increase annually. Organizations are thereby at risk for financial losses, data breaches, regulatory fines, and exposure of their trade secrets. However, the problem, for the most part, is not a technology problem but a management problem in not formally practicing or ensuring that insider risk assessments are conducted on a regular basis.
Without insider risk assessments, an organization does not have a solid foundation to mitigate risk or take corrective action. The organization is also blind to the actual state of its security program. There will be an inability to detect potential threats from current and former employees. And most importantly, the organization will lack the foresight to enhance measures to protect against insider threats.
“With all the focus on cybersecurity to protect against external attacks, it is easy to overlook the fact that people inside the firewall often represent the greater threat,” said Avasant fellow Fred Pond. “Countering the threat requires a sustained management commitment to conduct insider risk assessments as a formal part of the security program.”
In our annual IT Management Best Practices report, insider risk assessment is one of ten disciplines in the IT security and risk management category. The other nine are IT security training, data classification and retention, two-factor authentication, IT security compliance audits, security incident management, penetration testing, disaster recovery planning, disaster recovery plan testing, and business continuity planning. These practices reduce risk, either from security incidents or losses due to business disruptions and disasters.
Our full report looks at adoption trends and maturity of insider security risk assessment by organization size and sector. We conclude with practical recommendations for organizations to improve their insider risk assessments.
This Research Byte is a brief overview of our Insider Security Risk Assessment Best Practice report. The full report is available at no charge for subscribers, or it may be purchased by non-clients directly from our website (click for pricing).





