Bring your own device (BYOD) policies are a sensible approach for many organizations to leverage the convenience and familiarity of personal devices for their employees. These policies proved to be effective when employees worked from home during the pandemic. But BYOD adoption appears to have reached its peak, plateauing over the past five years.
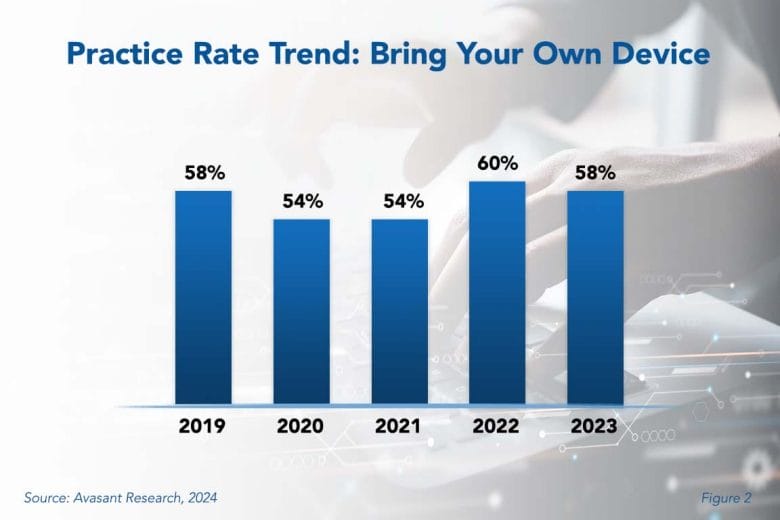
As shown in Figure 2 from the full report, BYOD Best Practices, 58% of organizations currently allow employees to bring their own devices, which is down from 60% in 2022 but up from 54% in 2021. However, our annual IT Management Best Practices survey found that just under one-third of respondents chose not to allow employees to use their personal devices for work purposes. Relative to other best practices in this study, the percentage of organizations that have policies permitting employees to use personal devices for work-related activities is low. The practice is not widely embraced. Despite this, BYOD is a maturing best practice that clearly has room to grow.
Users want to conduct business from any location using devices that get the job done. This complicates IT’s responsibility to ensure security and reliability. Any unmanaged device in an enterprise IT environment is potentially an unsecured device that jeopardizes company assets and data. IT departments must be able to safely onboard new hires and keep an eye on every company device and personal device that they use for work.
“The demand for personal gadgets will increase, fueled by consumer devices,” said Asif Cassim, principal analyst for Avasant Research, based in Los Angeles. “Organizations will need a robust BYOD policy balancing productivity and data protection.”
Allowing employees to use their personal devices for work must begin with a written policy that considers all aspects and impacts of BYOD. In the event of a security breach, loss of confidential information, or misuse, having a written policy provides some degree of legal protection that the organization might not have if BYOD is implemented in an informal manner. The policy should be signed by every employee who is permitted to use personal devices for work. This includes top executives, who have access to the most confidential information within the organization. Employers also should conduct periodic training and reinforcement of the policy on a regular basis or whenever the policy changes.
In this report, we first take a look at adoption trends for BYOD by organization size and sector. We also discuss the elements that every BYOD policy should contain, steps IT organizations should take before enabling users to access corporate networks with their personal devices, and solutions available to help manage the security of mobile devices and applications.
This Research Byte is a brief overview of our report on this subject, BYOD Best Practices. The full report is available at no charge for Computer Economics clients, or it may be purchased by non-clients directly from our website (click for pricing).

