This RadarView is designed to inform enterprises about cybersecurity best practices and provide a relatively granular understanding of key service providers. It begins with a summary of key trends that are shaping the cybersecurity space. We continue with a detailed assessment of 29 providers offering cybersecurity services. Each profile provides an overview of the service provider, its key IP assets, and a list of clients and partnerships, along with brief client case studies. Each profile concludes with analyst insights on the provider’s practice maturity, partner ecosystem, and investments and innovations.
Why read this RadarView?
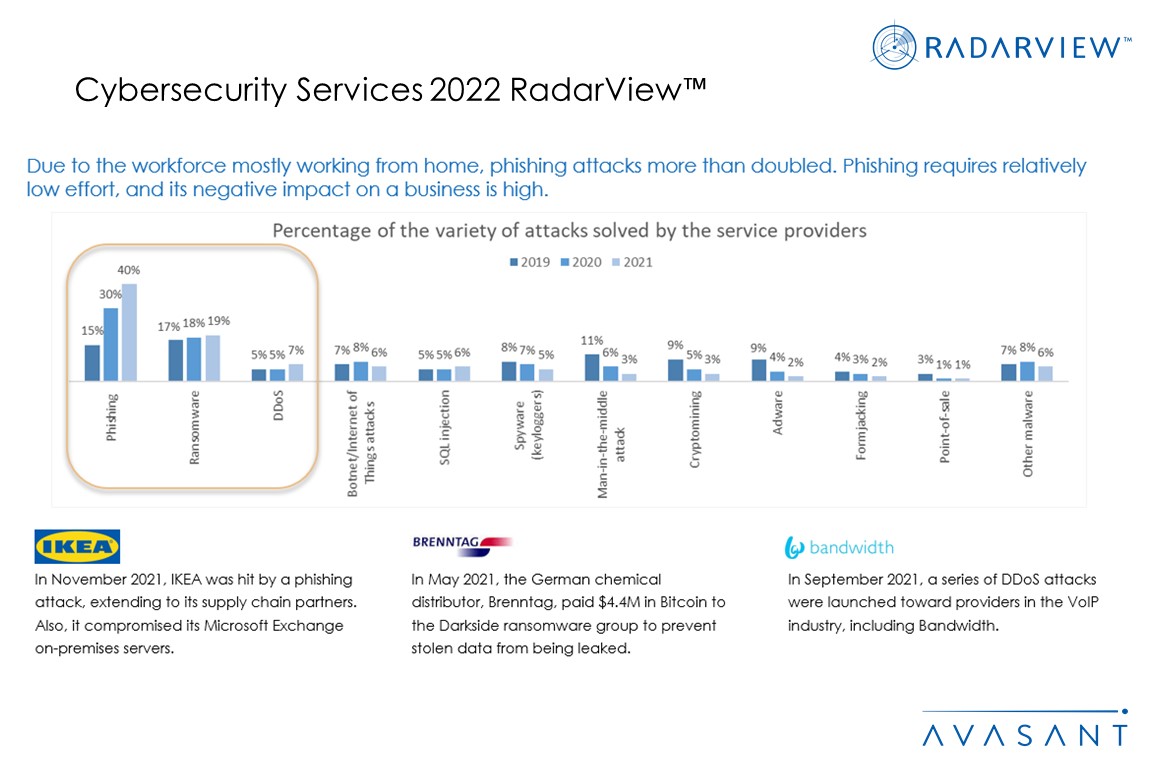
The Russia-Ukraine conflict has further escalated cyber risks in an already precarious cyber threat environment. Organizations continue to contain email cyberattacks involving phishing that are extending to their supply chain partners.
The Cybersecurity Services 2022 RadarView™ highlights key cybersecurity market trends and Avasant’s viewpoint. It aids companies in identifying top service providers to assist them in adopting cybersecurity solutions. It also offers an analysis of each service provider’s capabilities in technology and delivery support, enabling organizations to identify the right strategic partners for cybersecurity.
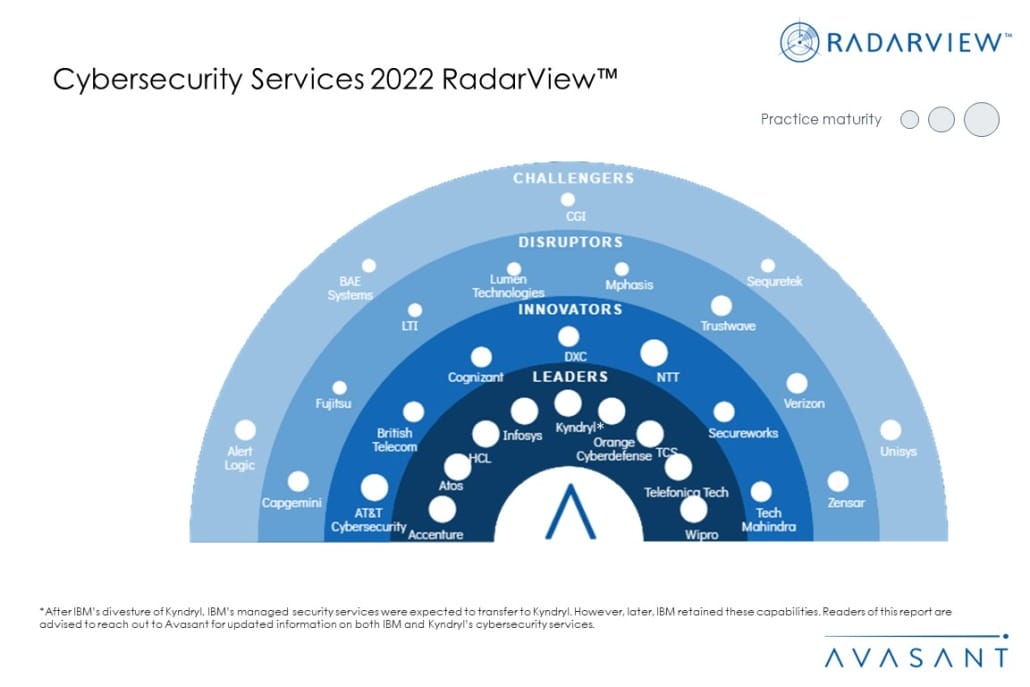
Featured providers
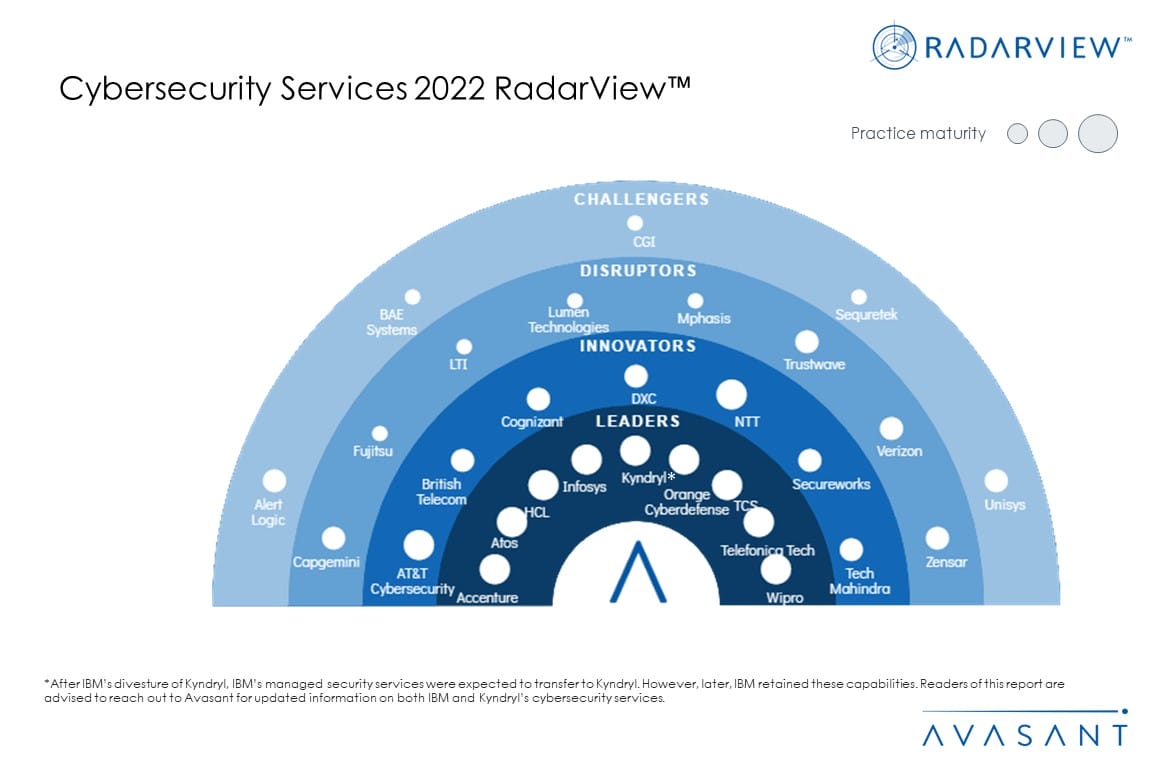
This RadarView includes a detailed analysis of the following cybersecurity services providers: Accenture, Alert Logic, AT&T Cybersecurity, Atos, BAE Systems, British Telecom, Capgemini, CGI, Cognizant, DXC Technologies, Fujitsu, HCL, Infosys, Kyndryl, LTI, Lumen Technologies, Mphasis, NTT, Orange Cyberdefense, Secureworks, Sequretek, TCS, Tech Mahindra, Telefónica Tech, Trustwave, Unisys, Verizon, Wipro, and Zensar.
Methodology
The industry insights and recommendations presented are based on our ongoing interactions with enterprise CXOs and other key executives; targeted discussions with service providers, subject matter experts, and Avasant Fellows, along with lessons learned from consulting engagements.
Our evaluation is based on primary input from the service providers, focused briefings, public disclosures, validation from their clients, and Avasant’s ongoing market interactions. The assessment is across the three dimensions of practice maturity, partner ecosystem, and investments and innovation, leading to our recognition of those service providers that brought the most value to the market over the last 12 months.
Table of contents
About the report (Page 3)
Executive summary (Pages 4–8)
-
- Defining cybersecurity
- Key enterprise cybersecurity trends shaping the market
- The road ahead for enterprises
- Avasant recognizes 29 top-tier providers supporting enterprise adoption of cybersecurity services
Lay of the land (pages 9–17)
-
- Attack vectors become more varied and sophisticated
- Phishing attacks continue to account for the largest percentage of cyberattacks followed by ransomware
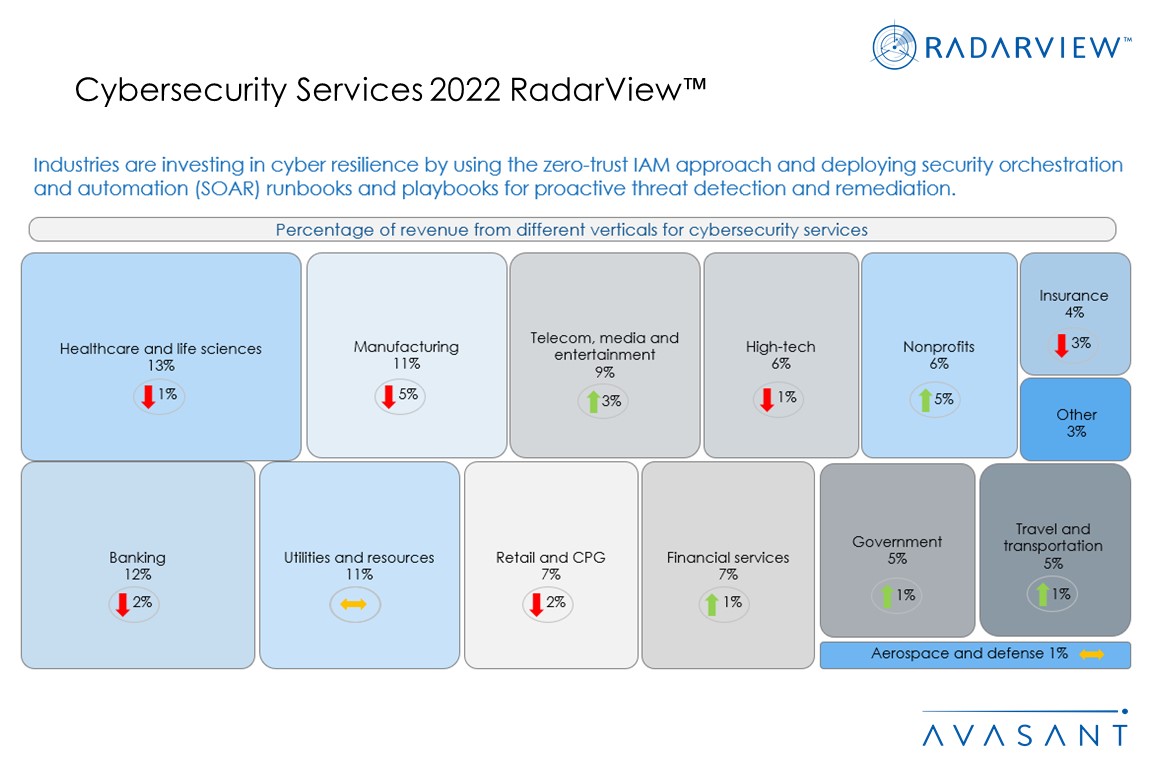
- Essential services, including healthcare and banking, continue to lead the cybersecurity adoption trend
- Organizations modernize their IT infrastructure, as there is increased interest in the zero-trust security model
- Companies deploy or refresh necessary security controls for the evolving landscape
- Engage with providers that offer advisory services along with implementation and managed services
- Companies move from a reactive to a proactive SOC and automate the triage process and incident response
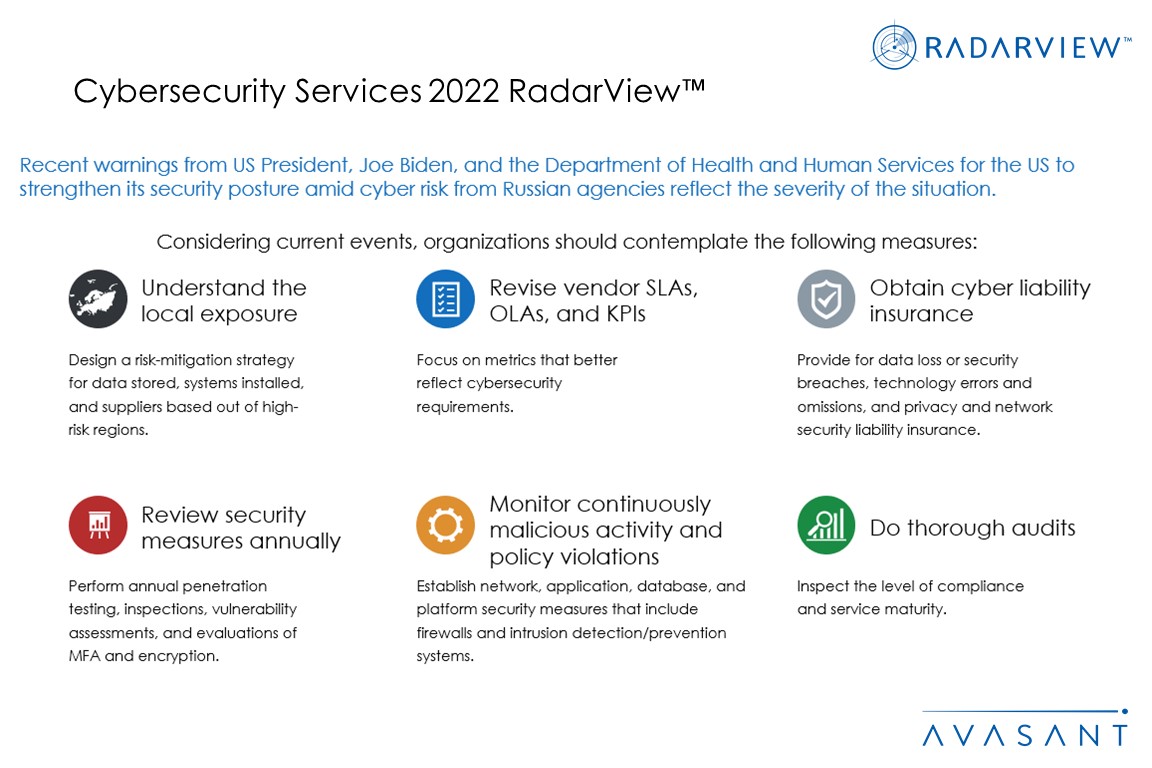
- Organizations should prepare for cyber risks posed by the Russia-Ukraine war
RadarView overview (Pages 18–23)
-
- Research methodology and coverage
- Interpretation of classification
- RadarView assessment
Service provider profiles (Pages 24–82)
-
- Detailed profiles providing a 360-degree view of the following service providers: Accenture, Alert Logic, AT&T Cybersecurity, Atos, BAE Systems, British Telecom, Capgemini, CGI, Cognizant, DXC Technologies, Fujitsu, HCL, Infosys, Kyndryl, LTI, Lumen Technologies, Mphasis, NTT, Orange Cyberdefense, Secureworks, Sequretek, TCS, Tech Mahindra, Telefónica Tech, Trustwave, Unisys, Verizon, Wipro, and Zensar.
Key contacts (Page 83)
Read the Research Byte based on this report.