The Russia-Ukraine war has further escalated cyber risks in an already precarious cyber threat environment. Organizations continue to endure email cyberattacks involving phishing that are extending to their supply chain partners. As businesses modernize their IT infrastructure, there is increased interest in the zero-trust security model and deploying or refreshing security controls. These measures help companies move from a reactive to a proactive security operations center (SOC) by automating the triage process and incident response.
These emerging trends are covered in Avasant’s Cybersecurity Services 2022 RadarView™. The report is a comprehensive study of the industry-wide adoption of cybersecurity services. It includes the current landscape and provides enterprise recommendations. It takes a close look at the leaders, innovators, disruptors, and challengers in this market.
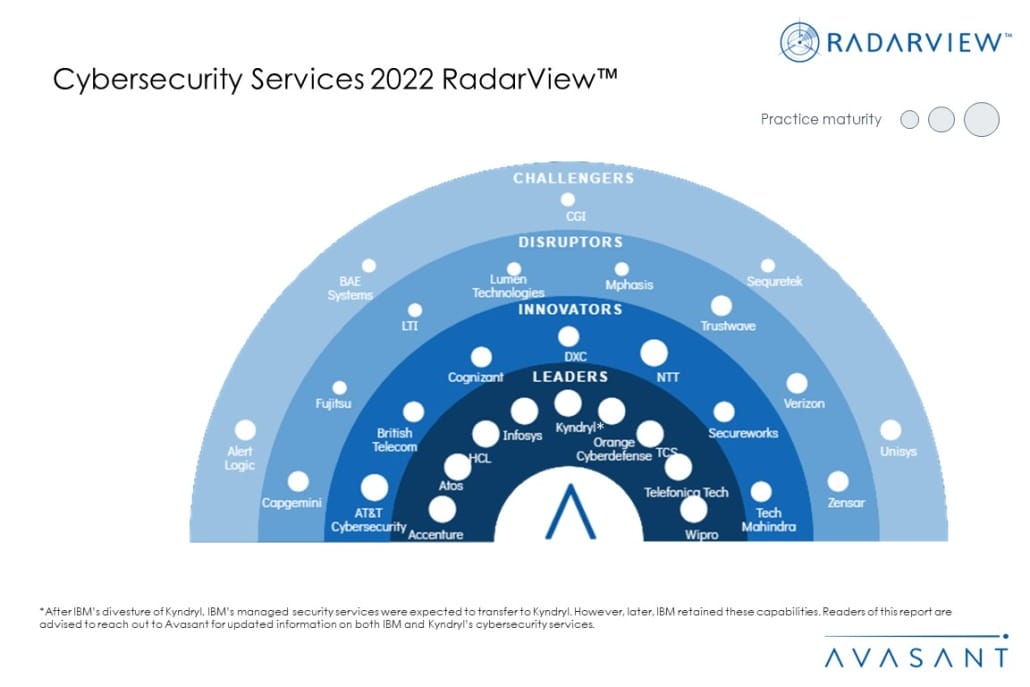
Avasant evaluated 35 providers using three dimensions: practice maturity, partner ecosystem, and investments and innovation. Of the 35 providers, we recognized 29 as having brought the most value to the market during the past 12 months.
The report recognizes service providers in four categories:
-
- Leaders: Accenture, Atos, Kyndryl, HCL, Infosys, Orange Cyberdefense, TCS, Telefónica Tech, and Wipro
- Innovators: AT&T Cybersecurity, British Telecom, Cognizant, DXC, NTT, Secureworks, and Tech Mahindra
- Disruptors: Capgemini, Fujitsu, LTI, Lumen Technologies, Mphasis, Trustwave, Verizon, and Zensar
- Challengers: Alert Logic, BAE Systems, CGI, Sequretek, and Unisys
Figure 1 from the full report illustrates these categories:
“As attack vectors become more varied and sophisticated, organizations need to tighten up their network, application, database, and platform security measures,” said Gaurav Dewan, Avasant associate research director. “This is best supported by a dedicated, internal team or third-party service provider who can respond in real-time.”
The full report provides a number of findings and recommendations, including the following:
1. Move from a reactive to a proactive SOC.
-
- Use machine learning and data science to model attacker behavior, for example, indicators of compromise, and proactively identify threats and automate the triage process and incident response.
2. Consider a zero-trust security model.
-
- Replace legacy VPNs and traditional internet gateways with a zero-trust solution and deploy cloud-based solutions to neutralize cyberattacks on connected operational technology devices.
3. Refresh necessary security controls for this evolving landscape.
-
- Enterprise customers need to secure their hybrid environment by refreshing, enabling, and standardizing security controls deployment to address trends emerging around cloudification, Industry 4.0, and the convergence of 5G and software-defined networking.
4. Layout a comprehensive audit program.
-
- Considering the Russia-Ukraine war, organizations should reassess risk, analyze performance metrics, check the supply chain, and layout a comprehensive audit program.
“With a more distributed compute environment and workforce, we are seeing a move toward a more proactive security posture,” said Avasant director Mark Gaffney. “This should include regular red and blue teaming activities to identify vulnerabilities and remediate them before the bad guys find them.”
The full report also features detailed profiles of 29 service providers, along with their solutions, offerings, and experience in assisting enterprises in their cybersecurity transformation journeys.
This Research Byte is a brief overview of the Cybersecurity Services 2022 RadarView™ (click for pricing).


