Computer Economics, a division of Avasant Research, has released its major annual study on 34 IT management best practices, and one important category—IT security and risk management—is showing mixed results. This is a bad sign in 2020, considering the changing threat landscape and the ramifications of the pandemic. Many companies virtualized their IT organizations and shifted to work-from-home (WFH) environments early in 2020. When this happened, they dramatically extended the boundaries of their enterprise into insecure territory.
“Cyberattacks have surged at least 85% since March,” said Tom Dunlap, director of Avasant Research based in Los Angeles. “Data theft and ransomware are on the rise, aimed increasingly at the work-from-home crowd. Because of this new reality, it is shocking what our best practices survey revealed this year: Many security best practices are not applied consistently.”
Figure 3 from our full study, IT Management Best Practices 2020-2021, shows that five IT security and risk management practices range in maturity from 41% to 46%. What do we mean by practice maturity? It means the percentage of respondents that apply a practice formally and consistently. Take encryption, for example, which has a 46% maturity rating. Forty-six percent of companies encrypt data consistently and with a formal plan. This means a whopping 54% of survey respondents do NOT encrypt data formally and consistently, which is alarming. This might mean they do not encrypt all of their data or perhaps they encrypt data at rest but not while it is moving. Or, there is no formal plan in place to be sure all critical data is encrypted. This is a security breach waiting to happen.
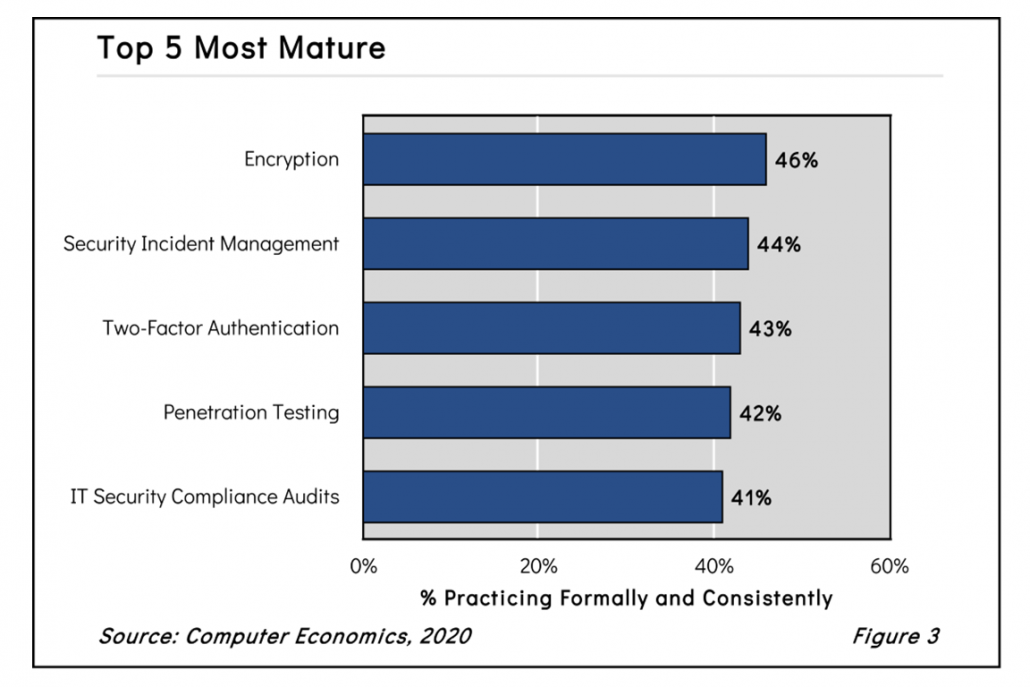
Or take security incident management—number two on our most mature list—with 44% saying they apply this best practice formally and consistently. But that means 56% of companies do not consistently and formally record, track, and resolve security incidents. The fact that 44% of organizations have a security incident management practice is expected, given corporate standards and WFH realities. But it is disappointing that 56% do not manage security incidents formally and consistently. Even more disappointing is that the maturity percentage (44%) is down from last year (51%). Perhaps this is one reason that we continue to see little progress against high-profile cyberattacks.
Third on the list is two-factor authentication (2FA), at 43%. Two-factor authentication is a security measure that provides an extra layer of protection to an account log-in. It was at 34% last year, so at least it is moving in the right direction. Still, the fact that 57% do not use 2FA formally and consistently is worrisome.
Penetration testing is fourth at 42%. A penetration test, often called a pen test, is a best practice that identifies security weaknesses. It was at 44% last year, so it is down a bit in 2020. Not to beat a dead horse, but the fact that 58% do not consistently and formally conduct pen tests is disappointing.
Rounding out the most-mature list is IT security compliance audits, at 41%. Periodically auditing users and IT staff to ensure that security and privacy policies are followed is one of the most important security measures an organization can take. What good is having security policies in place if no one is following them? It is disappointing that this maturity number is only 41%. It was practically the same last year, 42%.
Some of the 34 best practices are well-established disciplines and are widely accepted. Others are gaining traction among leading-edge organizations. Still other practices are being widely promoted by tools vendors and consultants but are only rarely adopted, and it remains uncertain whether they will endure. Our goal in this study is to provide IT executives with real-world data on how widely each practice is implemented, a basis for comparing their organizations with their peers, and a means of identifying emerging best practices.
This study is now in its 13th year. Each year, we ask IT organizations in our annual survey to what extent they have adopted a selected list of IT management best practices. Survey participants have five response choices:
-
- No Activity: We are not practicing this discipline in any way.
- Implementing: We are in the process of implementing this best practice.
- Practicing Informally: We do not have formal policies or procedures for this discipline, but we do practice it in an informal or ad-hoc manner.
- Practicing Formally but Inconsistently: We have formal policies and procedures for this discipline, but we do not follow them consistently or to the extent that we should.
- Practicing Formally and Consistently: We have formal policies and procedures for this discipline, and we follow them consistently. This is the maturity level.
The best practices in the study are as follows:
-
- IT governance practices: IT strategic planning, IT steering committee, IT project portfolio management, project management office, IT change control board, organizational change management, and enterprise architecture.
- IT financial management practices: IT personnel time tracking, service-based cost accounting, chargeback of IT costs, showback of IT costs, IT service catalog, and benchmarking IT spending levels.
- IT operational management practices: Monitoring software licenses, IT Infrastructure Library (ITIL), IT asset management system, bring your own device, user-satisfaction surveying, and IT performance metrics.
- IT security and risk management practices: IT security training, data classification and retention, two-factor authentication, IT security compliance audits, penetration testing, security incident management, encryption, disaster recovery planning, disaster recovery testing, and business continuity planning.
- Application development practices: System development life cycle, agile development, software change management process, DevOps, website accessibility, and post-implementation audits.
The full study is designed to increase the awareness of IT leaders concerning what are the best practices in IT management, provide benchmarks against which an IT organization can compare its own adoption and practice level, and justify investments to improve an organization’s IT management practices.
This Research Byte is a brief overview of our report on this subject, IT Management Best Practices 2020-2021. The full report is available at no charge for Avasant Research subscribers, or it may be purchased by non-subscribers directly from our website (click for pricing).


