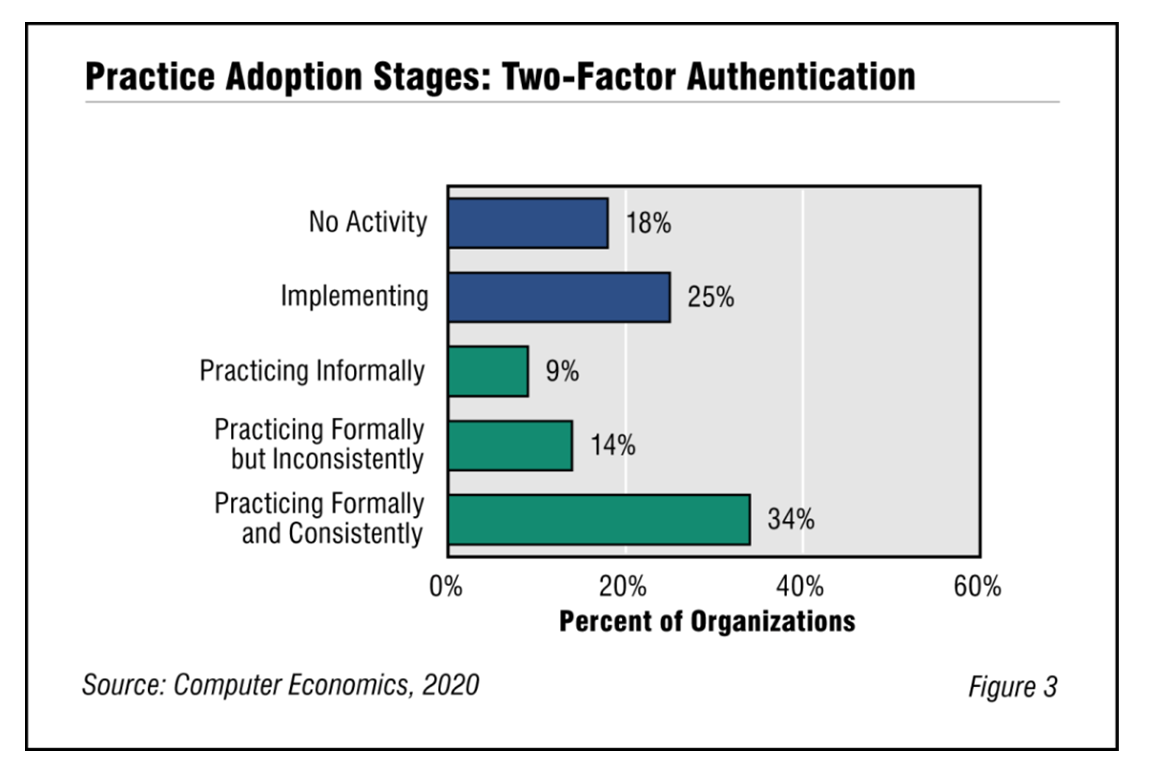
Two-factor authentication is an IT security best practice that provides an extra layer of protection for system access. It is a highly advisable security measure, but our annual survey of IT management best practices shows that not enough companies use it formally and consistently. This report begins with a brief explanation of two-factor authentication. We next study two-factor authentication adoption and practice levels, examining those by organization size and sector. We conclude with best-practice recommendations. (16 pp., 6 fig.)
DISCLAIMER:
Avasant's research and other publications are based on information from the best available sources and Avasant's independent assessment and analysis at the time of publication. Avasant takes no responsibility and assumes no liability for any error/omission or the accuracy of information contained in its research publications. Avasant does not endorse any provider, product or service described in its RadarView™ publications or any other research publications that it makes available to its users, and does not advise users to select only those providers recognized in these publications. Avasant disclaims all warranties, expressed or implied, including any warranties of merchantability or fitness for a particular purpose. None of the graphics, descriptions, research, excerpts, samples or any other content provided in the report(s) or any of its research publications may be reprinted, reproduced, redistributed or used for any external commercial purpose without prior permission from Avasant, LLC. All rights are reserved by Avasant, LLC.