-

IT Security Outsourcing Trends and Customer Experience 2023
IT security is a major focus for IT leaders that continues to grow in importance. The threat landscape is evolving with increased reliance on the cloud, greater diversity in the IT service portfolio, more employees working from home, and a more burdensome regulatory environment.
November, 2023
-
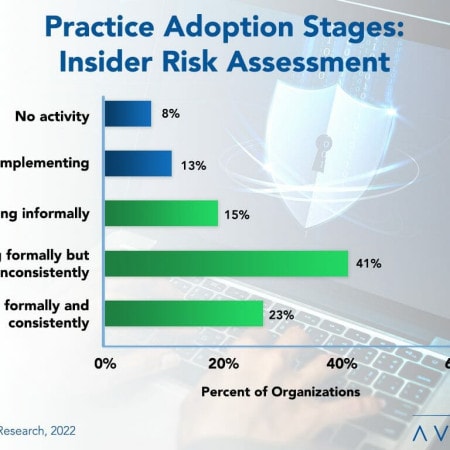
Insider Risk Assessment: Which of Your Employees May Be the Bad Apple?
Most IT organizations have insider security risk assessments to some extent, but, too often, they are not formally established, comprehensive in their scope, or followed consistently. Because of this, insider threats remain prevalent and continue to increase annually. This Research Byte summarizes our full report on Insider Security Risk Assessment Best Practices.
September, 2022
-
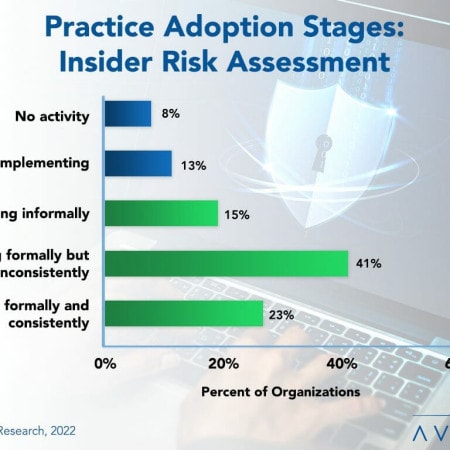
Insider Security Risk Assessment Best Practices 2022
Most organizations are aware of the IT security threats posed by outsiders. Countermeasures such as firewalls, antivirus software, and intrusion detection systems are all aimed at these threats. Yet these measures do little to counter insider threats within the organization.
September, 2022
-
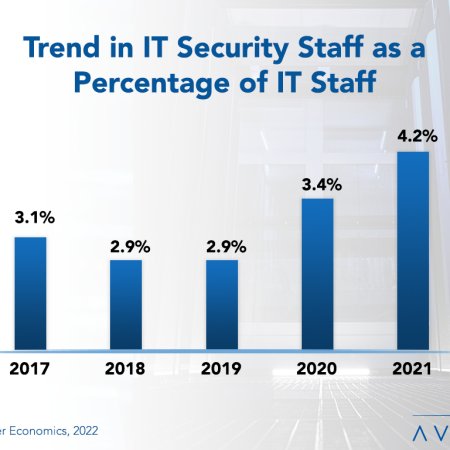
IT Security Staffing Ratios 2022
High-profile security attacks and the impact of remote work continue to put pressure on IT security personnel. This report presents the five-year trend in IT security staffing and provides benchmarks for understanding the IT security staff head count. We analyze IT security staffing in terms of the number of applications, users, and network devices. Our analysis also includes the influence of organization size and sector on staffing requirements. We conclude with recommendations for optimizing IT security staffing. (21 pp., 9 fig.)
April, 2022
-
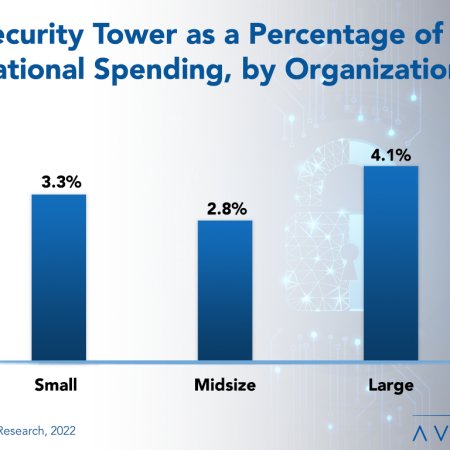
Avasant Releases New Benchmarks for IT Security and Cybersecurity Spending
Security and cybersecurity incidents are costly, with losses increasing every year. In light of these growing threats, it is no wonder that organizations in all industries continually rank security as a top priority for new spending. But how much are they spending? To answer this question, we have now released our new report, IT Security, Cybersecurity, and Compliance Spending and Staffing Benchmarks.
February, 2022
-

IT Security, Cybersecurity, and Compliance Spending Benchmarks 2022
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
February, 2022
-
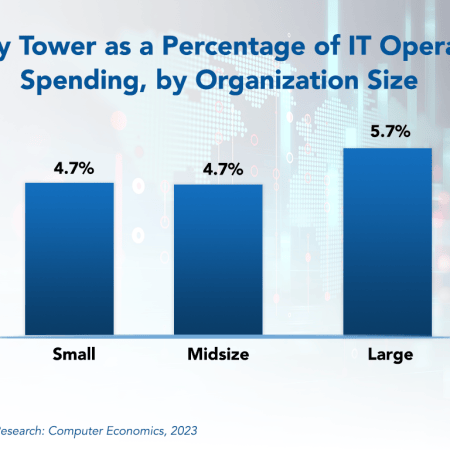
IT Security, Cybersecurity, and Compliance Spending Benchmarks 2023
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
May, 2023
-

IT Security a Never-Ending Arms Race
With increased threats from within and without, IT organizations would love to have a silver bullet for security. Although there is no silver bullet, there is a growing array of security technology available. No wonder then that IT security technology investment and adoption are both high, and businesses can reap the benefits of protection that the technologies provide. This Research Byte summarizes the full report, IT Security Technology Adoption and Customer Experience.
November, 2021
-

IT Security Technology Adoption and Customer Experience 2021
Organizations in all industries and of all sizes need IT security technology, and with threats on the rise the investment rate is the highest of any category of technology that we track. However, return on investment is not as rosy, with security technology earning a moderate rating for ROI. This report examines adoption trends for IT security technology of all types, from basic capabilities such as firewalls and spam filtering to more advanced tools such as incident detection. We analyze the adoption rate, investment rate, and economic experience for security technology overall. We conclude with recommendations for ensuring the success of IT security technology investments.
November, 2021
-
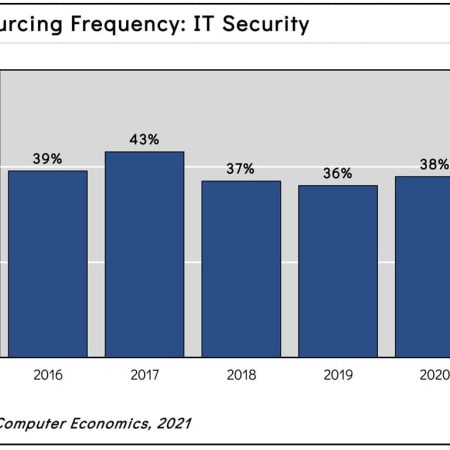
Third-Party Security Providers Evolve to Handle Diverse Threats
Security has become a major focus for IT leaders in 2021, and companies are now increasing their spending to secure the enterprise, including greater use of third-party security providers. This is because the threat landscape is evolving, as seen most recently in the Colonial Pipeline ransomware attack. This Research Byte summarizes our full report on IT security outsourcing trends.
May, 2021
-
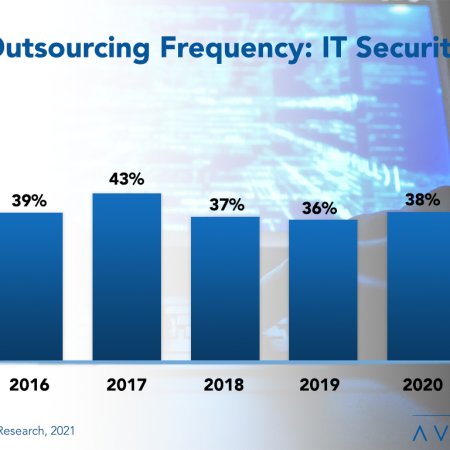
IT Security Outsourcing Trends and Customer Experience 2021
IT security has become a major focus for IT leaders in 2021. This is because the threat landscape is evolving with increased reliance on the cloud, a greater diversity in the IT service portfolio, more employees working from home, and a more burdensome regulatory environment. This report helps IT executives compare their outsourcing activity and experience with other IT organizations. We use three metrics to measure IT security outsourcing activity: how many organizations outsource IT security (frequency), how much of the workload is typically outsourced (level), and the change in the amount of work outsourced (trend). We also measure the cost and service experience of organizations that outsource this function and determine how outsourcing activity and experience vary by organization size and sector. We conclude with recommendations.
May, 2021
-
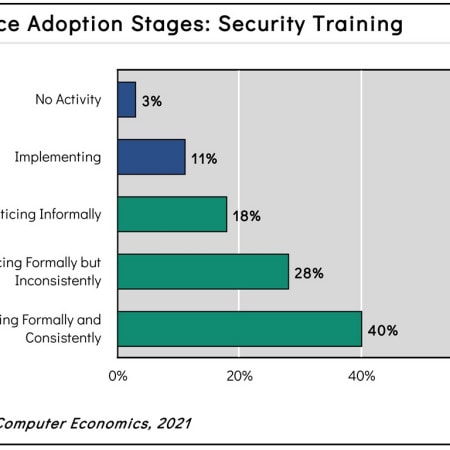
Call Security: Our People Lack Awareness
Security training is a business best practice that involves the training of all IT and user personnel in a company’s security policies and procedures to increase awareness and ensure compliance. It is a highly advisable practice for every company. However, our report shows that too many adopters are only conducting security training in an informal manner, which can have dire consequences. This Research Byte provides a summary of our full report on security training best practices.
April, 2021
-

Security Training Adoption and Best Practices 2021
Security training is a business best practice that involves the training of all IT and user personnel in a company’s security policies, procedures, and best practices to increase awareness and ensure compliance. It is a highly advisable practice for every organization. Many companies report the existence of security training, yet there is ample room for improvement. This report begins by defining security training and summarizing the main types of training available. We next study the adoption and practice levels and examine those by organization size and sector. We conclude with best-practice recommendations.
April, 2021
-

IT Security Spending Benchmarks
Although IT security spending as a percentage of the IT budget is flat year over year, the trend has been upward over the past four years. This study establishes benchmarks that enable organizations to assess their spending on IT security software, hardware, and services. The benchmarks include IT security spending as a percentage of the IT budget and IT security spending per user. We examine the four-year trend in these benchmarks as well as variances by organization size and sector. We conclude with recommendations for optimizing IT security costs and ensuring the budget is spent effectively. (19 pp., 10 fig.) [Research Byte]
September, 2016

 Grid View
Grid View List View
List View