-
Avasant Releases New Benchmarks for IT Security and Cybersecurity Spending
Security and cybersecurity incidents are costly, with losses increasing every year. In light of these growing threats, it is no wonder that organizations in all industries continually rank security as a top priority for new spending. But how much are they spending? To answer this question, we have now released our new report, IT Security, Cybersecurity, and Compliance Spending and Staffing Benchmarks.
February, 2022
-

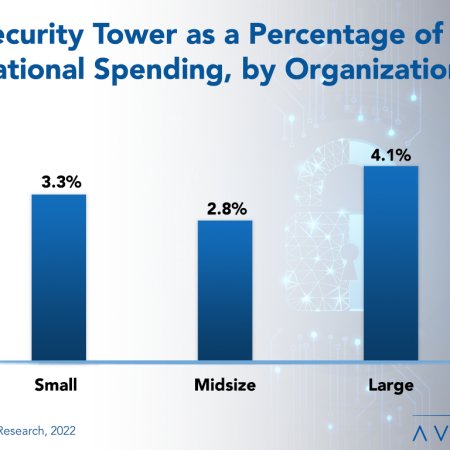
IT Security, Cybersecurity, and Compliance Spending Benchmarks 2022
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
February, 2022
-
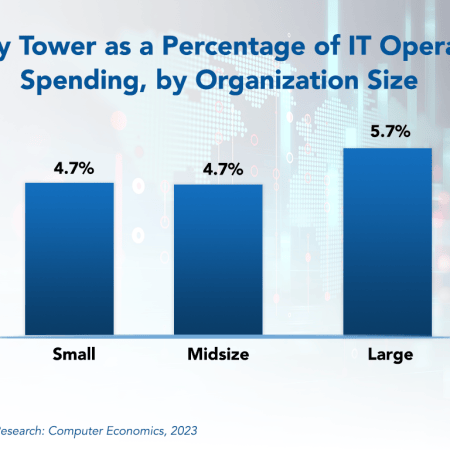
IT Security, Cybersecurity, and Compliance Spending Benchmarks 2023
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
May, 2023
-

Crossroads of the Utilities Sector Business Model
With an eye on the future, digital transformation offers Utilities the opportunity to be more efficient, responsive and innovative in delivering services. Digital transformation also provides improved customer engagement on mobile, social and web interfaces. This enables better two-way communications that lead to customized rate plans, products, and services based on customer usage, resulting in improved data management and analytics leading to higher operational efficiencies in the generation, transmission, and distribution. The industry is likely to witness a significant transformation which will eventually serve the best interest of both the consumer and the Utilities industry.
August, 2019
-

Moving Security Beyond Regulatory Compliance
Organizations today must comply with a greater number of regulations than ever before, many of which deal with information and system security. While the intent of these regulations is good, their proliferation is burdensome. Even more troubling, it is possible to be compliant but not secure. Based on our survey of 100 security, IT, and compliance professionals, this article proposes four principles for establishing a security program that goes beyond regulatory compliance. (5 pp., 6 figs.) [Executive Summary]
October, 2007

 Grid View
Grid View List View
List View