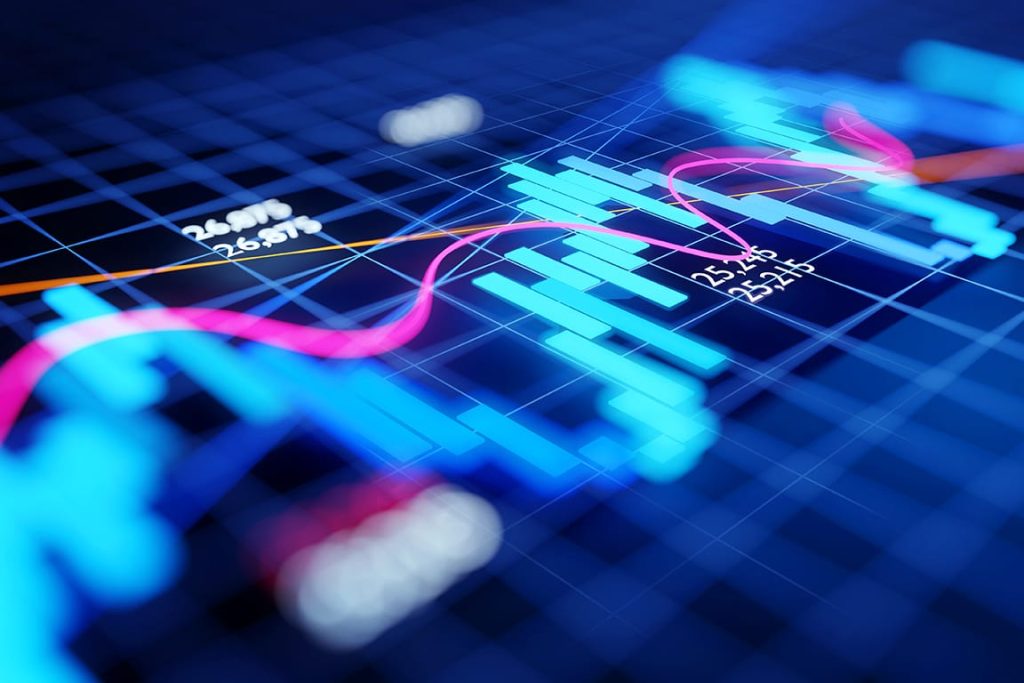
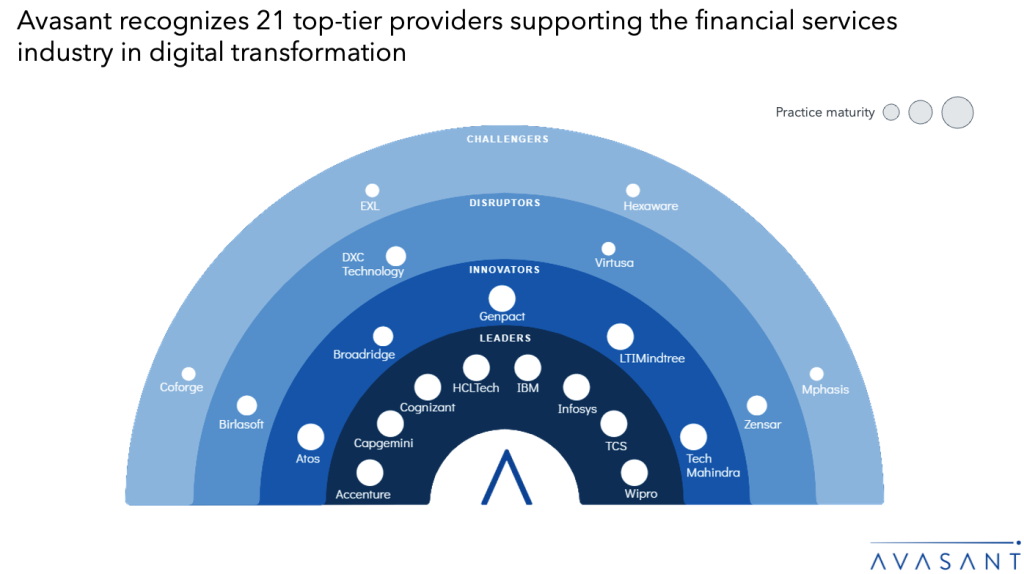
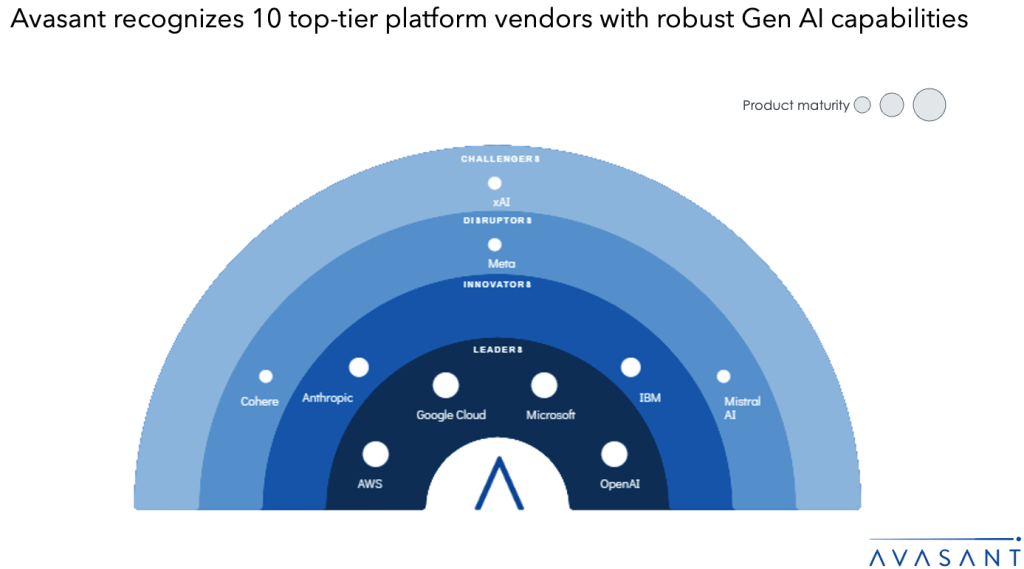
As enterprises move from pilots to scaled generative AI (Gen AI) deployments, platforms are evolving to support production readiness, regulatory alignment, and performance optimization. Vendors are integrating capabilities such as multimodal processing, edge inferencing, and governance toolkits to meet operational demands. To accelerate adoption across industries, they are building comprehensive partner ecosystems that include hyperscalers, infrastructure providers, service firms, and OEMs. These partners bring industry-specific expertise, enable edge deployment of LLMs, support Gen AI-native application and data integration, and provide access to scalable, production-ready infrastructure. The supply-side trends are covered in Avasant’s Generative AI Platforms 2025 RadarView™.