-
Generative AI-based Security Tools are, in Effect, Fighting Fire with Fire
Following the cultural and technological explosion brought forth by the launch of OpenAI’s ChatGPT last fall, the security industry has seen enormous investment in technologies for large language models (LLMs), such as generative AI. While players like Google and Microsoft have launched new generative AI security products, IBM, CrowdStrike, and Tenable have integrated features into their existing products. Though each product has its own capabilities, the focal point is to automate threat hunting and prioritize breach alerts. However, the rise of generative AI also includes the opportunity for threat actors. It has potentially lowered the barrier of entry for cybercriminals to develop sophisticated business email compromise phishing campaigns, find and exploit zero-day vulnerabilities, probe for critical infrastructure, create and distribute malware, and much more.
November, 2023
-

Cybersecurity in Connected Aircraft: Risk Mitigation for Airlines, Passengers, Airports, and Service Providers
The aviation industry is embracing a connected environment by digitizing its operations. This involves leveraging IoT devices, 5G networks, applied AI, advanced analytics, and SaaS-based applications to streamline maintenance, repair, and overhaul. A connected aircraft generates three types of information: aircraft control and navigation data, cabin-based in-flight entertainment data, and operations-based flight movement data. However, interconnected systems have greatly widened the risk perimeter. These demands call for applying security measures, including zero-trust security and secure by design principles, and collaborating with a technology partner who offers services such as threat detection, incident response, governance, risk and compliance, red teaming, 24x7 monitoring, and threat intelligence.
January, 2023
-

Digital Masters 2022 RadarView™
The Digital Masters 2022 RadarView™ addresses the need for enterprises to understand the current landscape for adopting digital technologies. The report helps them identify implementation services providers best suited for executing transformation initiatives by supplying granular insights for each provider.The 88-page report also provides our point of view on how enterprises have changed the way they look at technology, outsourcing, and reprioritizing their digital investments.
August, 2022
-

Cybersecurity Services 2022 RadarView™
The Cybersecurity Services 2022 RadarView™ is designed to inform enterprises about best practices in this space and provide a relatively granular understanding of key service providers. It provides a 360-degree view of key cybersecurity services providers across practice maturity, partner ecosystem, and investments and innovation, thereby supporting enterprises in identifying the right cybersecurity services partner. The 85-page report also highlights top market trends in the cybersecurity space and Avasant’s viewpoint.
April, 2022
-
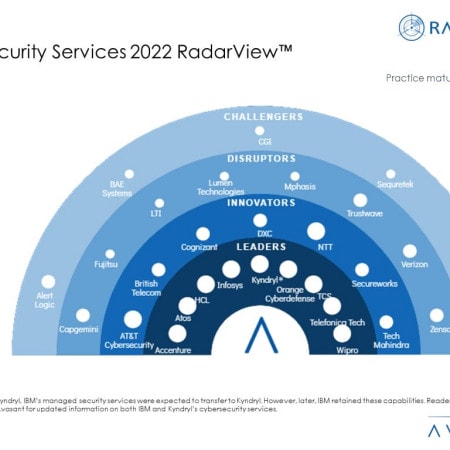
Cybersecurity Services: Moving to a Proactive Security Posture
The Russia-Ukraine war has further escalated cyber risks in an already precarious threat environment. Organizations continue to endure email cyberattacks involving phishing that are extending to their supply chain partners. As businesses modernize their IT infrastructure, there is increased interest in the zero-trust security model and deploying or refreshing security controls. These measures help companies move from a reactive to a proactive security operations center (SOC) by automating the triage process and incident response. These emerging trends are covered in Avasant’s Cybersecurity Services 2022 RadarView™.
April, 2022
-
Avasant Releases New Benchmarks for IT Security and Cybersecurity Spending
Security and cybersecurity incidents are costly, with losses increasing every year. In light of these growing threats, it is no wonder that organizations in all industries continually rank security as a top priority for new spending. But how much are they spending? To answer this question, we have now released our new report, IT Security, Cybersecurity, and Compliance Spending and Staffing Benchmarks.
February, 2022
-
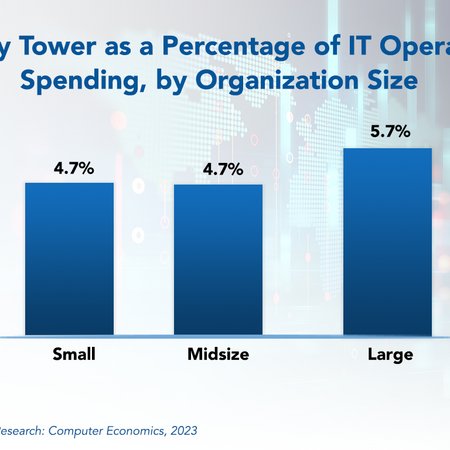
IT Security, Cybersecurity, and Compliance Spending Benchmarks 2023
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
May, 2023
-

IT Security, Cybersecurity, and Compliance Spending Benchmarks 2022
Security and cybersecurity incidents are costly, with losses increasing every year. It is no wonder, then, that organizations continually rank security as a top priority for new spending. But how much are they spending? This report provides spending and staffing benchmarks by industry and organization size for IT security, cybersecurity, and related compliance. Benchmarks are calculated by number of users, organization revenue, and percentage of IT spending, as well as by number of network devices, locations, and endpoints. Security staffing is calculated as a percentage of the IT staff and also per user. Industry benchmarks are provided for business services, financial services, critical infrastructure, public sector, healthcare, manufacturing/distribution, and retail. There is also a breakdown for identity/access management, security policy/awareness, cybersecurity/incident response, threat and vulnerability management, data privacy/security, and governance, risk, and compliance.
February, 2022
-

Wipro’s Edgile Acquisition: Another Step in the Right Direction for Wipro’s Cybersecurity Aspirations
IT service providers are looking to own the end-to-end cybersecurity adoption cycle and be part of the executive decision-making. This implies going beyond regular implementation and managed security services and offering consultancy and advisory services. Through Edgile, Wipro aims to achieve the following two goals: move up the value chain by playing an influential role in the initial stages of deals, which involve decision-making at the board or CXO leveland position itself as an end-to-end service provider by augmenting its cybersecurity consulting capabilities and covering the entire value chain.
February, 2022
-
Avasant Digital Forum: Building Healthcare’s Digital Future
In recent years, advocates of telemedicine promised increased access to healthcare, better patient outcomes, and reduced costs. COVID-19 became an unexpected large-scale trial for telehealth. Remote patient monitoring, chronic disease management, virtual appointments, and other aspects of digital medicine showed earlier success in those trials. As vaccines and therapeutics reduce the load on healthcare providers, they should not look to return to their previous standards of care. Instead, they should look to continue with digital healthcare in their post-COVID plans.
April, 2021
-

Avasant Digital Forum: The Age of Cyber Crime: Mitigating the Impact of Data Breaches
The recent Solarwinds breach has shown that cybercrime is a rapidly increasing threat to businesses and has become an inevitability. The business impact can range from loss of data to damaged consumer confidence and significant financial liabilities. While investing in cyber security is critical, there’s a fiduciary responsibility to have a mitigation plan against damage to business reputation and trust from a data breach. It’s important for every company to be prepared to handle the breach lifecycle – from Incident management to Impact assessment, Communication, Breach resolution and Recovery.
March, 2021
-

Avasant Digital Forum: Securing The Enterprise In The Post Covid World: Next Generation Cyber Defense
As enterprises rapidly shift to Cloud, Agile and Edge computing, their cyber security strategy has to adapt. The pandemic has further escalated the cyber-risks as organizations shifted to Work from Home and virtualized their operations. The Post-COVID enterprise security strategies must include a Cloud-centric model that spans across the extended work boundaries and a hybrid/multi-cloud environment. Securing your data against cyber threats and ransomware in this Extended Enterprise is now one of the most critical priorities.
December, 2020
-

Enterprise Security Orchestration Platforms 2020 RadarView™
The Enterprise Security Orchestrion Platforms 2020 RadarView™ report is designed to help enterprises make strategic decisions to identify the best security orchestration platform to build their SOC. It assesses the platform providers based on automation capabilities, the number of predefined playbooks, built-in integrations, flexibility in the pricing model, efforts to reduce TCO, and the maturity and scale of the operation.
October, 2020

 Grid View
Grid View List View
List View