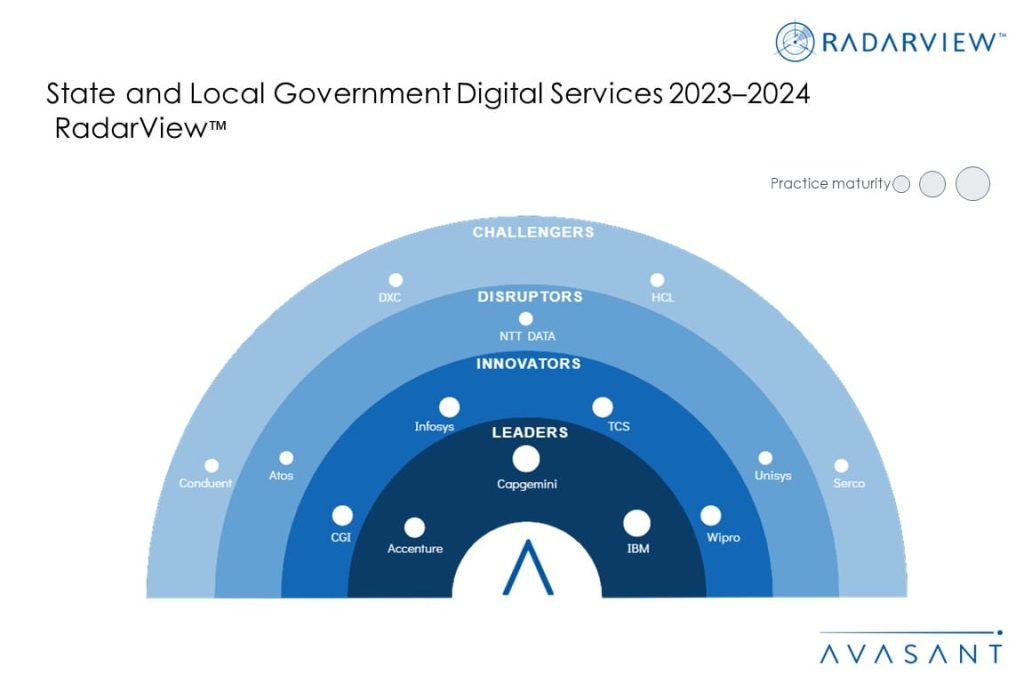
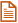While the demand for new infrastructure and real estate projects is rising, engineering and construction firms are facing skilled worker shortages, project overruns, supply chain disruptions, and increasing regulations. To address these challenges, businesses are accelerating their digital transformation journeys by leveraging connected construction platforms, project management solutions, automated tools for modular construction, and remote project inspections. Additionally, engineering and construction companies are using digital technologies for improved productivity, process efficiency, and increasing profitability, investing heavily in virtual reality and product life cycle management tools. These emerging trends are covered in Avasant’s Engineering and Construction Digital Services 2022–2023 RadarView™.