Latest Reports
-
![Application Developer Staffing Ratio Takes Another Dip Fig1AppDevStaffingRatio - Application Developer Staffing Ratio Takes Another Dip]()
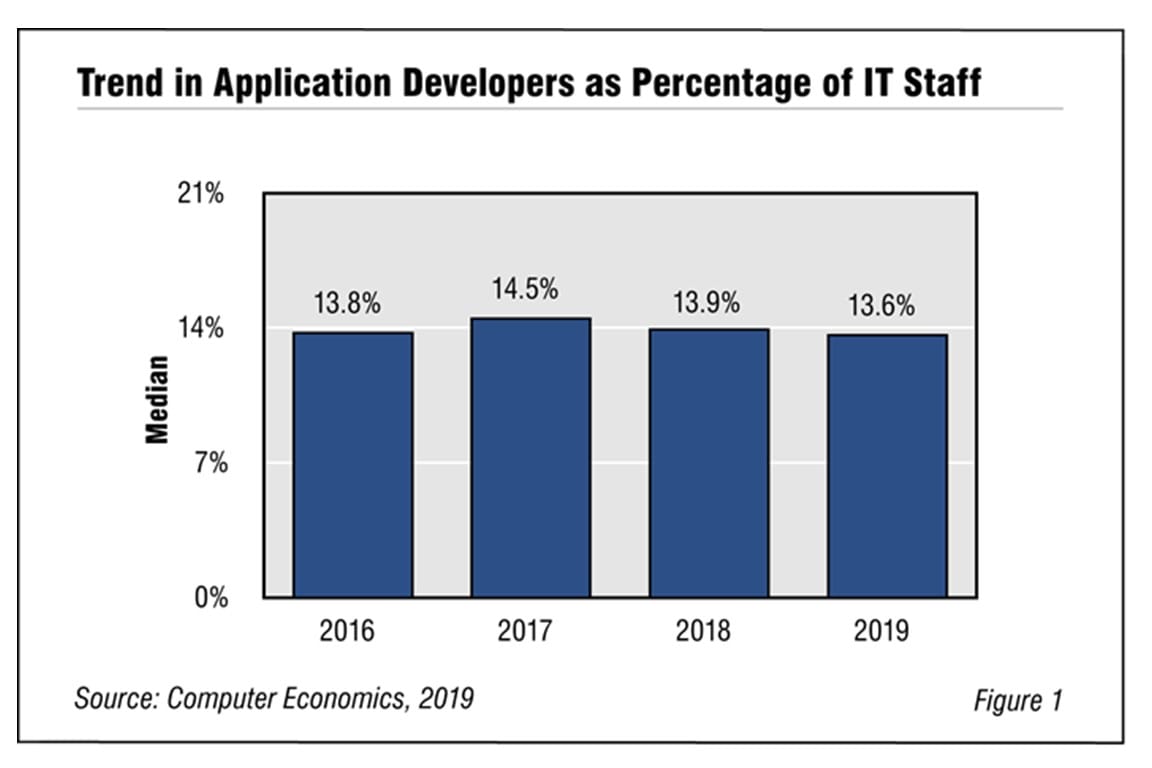
Application Developer Staffing Ratio Takes Another Dip
The ratio of application developers to the entire IT staff is a critical metric for IT managers. Why? Because developers tend to make up the largest part of most IT organizations, and they also tend to be among the higher-paid IT employees. Thus, it is vital for IT leaders to keep abreast of trends in application developer staffing ratios. This research byte summarizes our findings in the full report, Application Developer Staffing Ratios.
November, 2019
-
![What’s Behind the Decline in Business Analysts? Fig1BusinessAnalystStaffingRatios2020 - What’s Behind the Decline in Business Analysts?]()
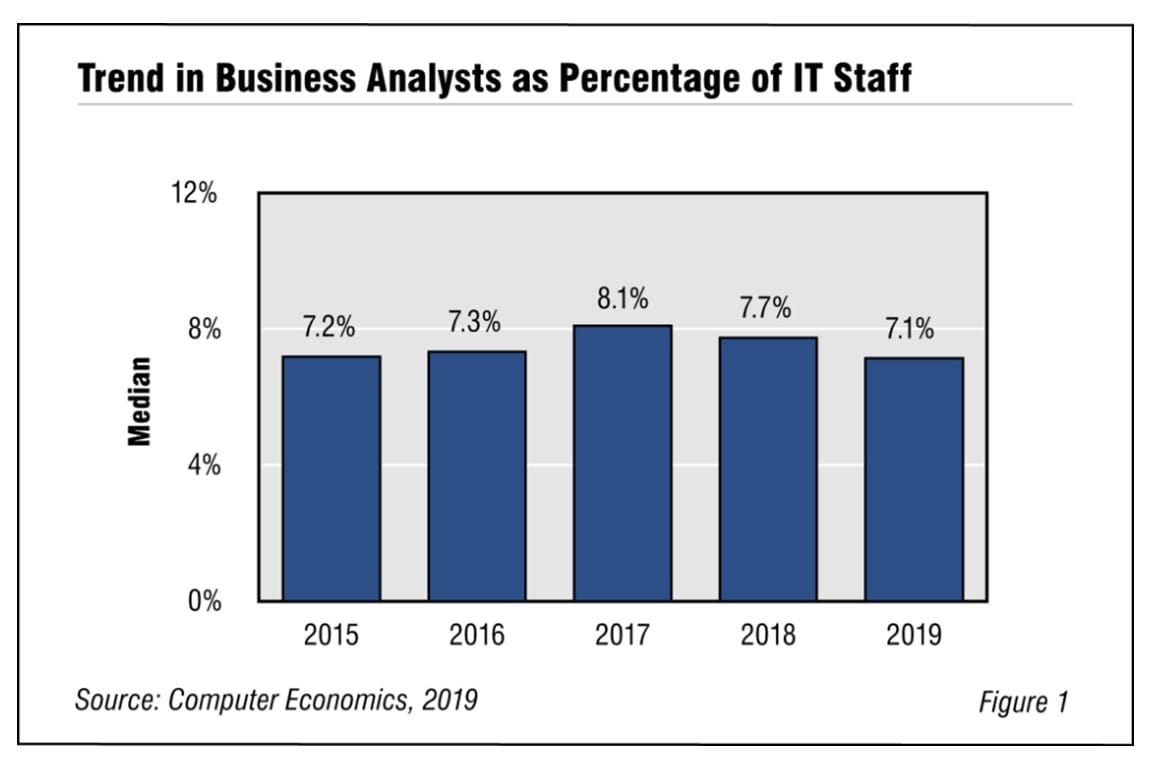
What’s Behind the Decline in Business Analysts?
With digital transformation taking center stage in recent years, we have predicted that the business analyst role would continue to rise in prominence within IT organizations. However, the number of business analysts as a percentage of the total IT staff has dropped for the second straight year. Were we wrong, or are there other factors behind the decline?
January, 2020
-
![Desktop Support Staffing Declines to Three-Year Low Fig1DesktopSupport2020 - Desktop Support Staffing Declines to Three-Year Low]()
Desktop Support Staffing Declines to Three-Year Low
Today’s desktop and laptop computers are not the hot commodity they were 30 years ago, but they still require a great deal of support. However, when viewed as a percentage of the total IT staff, the percentage of desktop support personnel has now reached a three-year low. This Research Byte explores some reasons behind the decline.
February, 2020
-
![Network Support Staffing Plateaus, Despite Increasing Pressure Fig1NetworkSupport2020 - Network Support Staffing Plateaus, Despite Increasing Pressure]()
Network Support Staffing Plateaus, Despite Increasing Pressure
The importance of computer networks cannot be overstated in this digital age. However, the level of network support staffing has plateaued in recent years and shows no signs of increasing. In other words, the increasing need for more bandwidth, better security, analytics, and reliability has not driven up the ratio of network support staff to total IT staff in the typical organization. This Research Byte summarizes the five-year trend in network support staffing ratios.
May, 2020
-
![Enterprise Security Orchestration Platforms – Gravitating Towards AI-Enabled Tools and Contextual Indicators Slide1 1 - Enterprise Security Orchestration Platforms – Gravitating Towards AI-Enabled Tools and Contextual Indicators]()
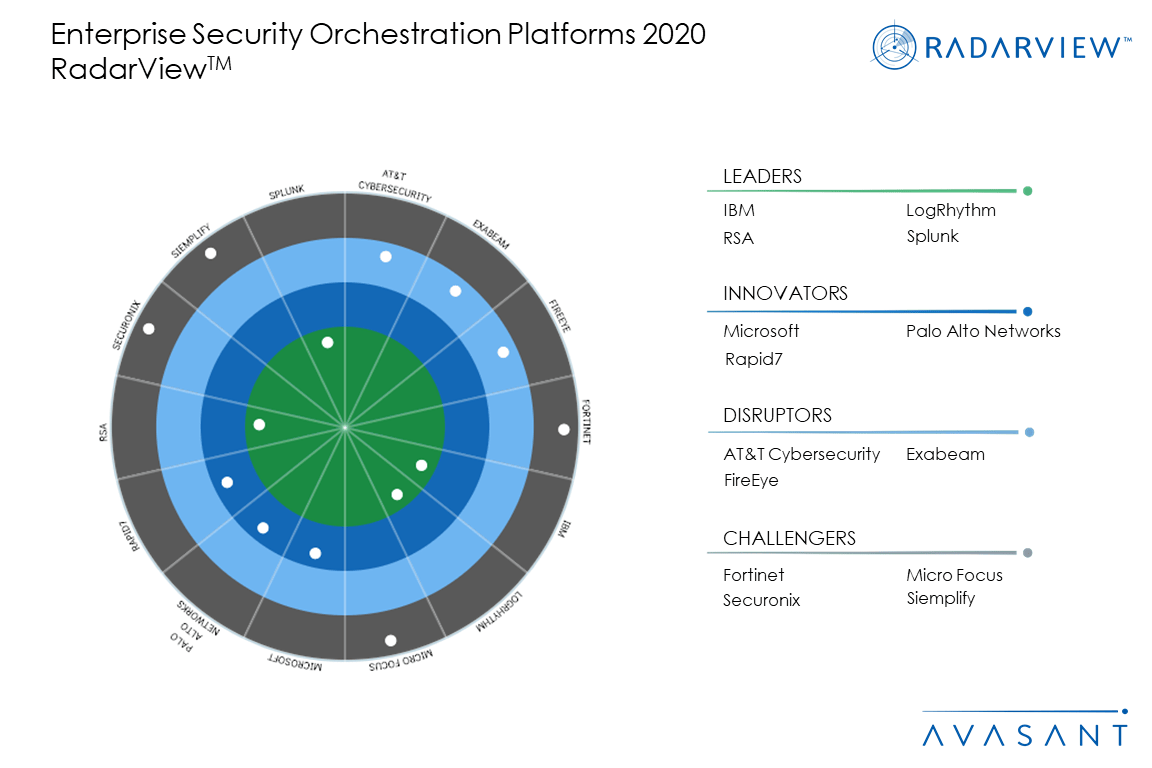
Enterprise Security Orchestration Platforms – Gravitating Towards AI-Enabled Tools and Contextual Indicators
The traditional enterprise security platform is evolving.They now incorporate more capabilities into a single enterprise SOAR (security orchestration, automation, and response) platform. The SOAR value proposition has become more evident during the COVID-19 pandemic, because organizations require multi-functional capabilities to secure themselves against new threats.These tools help solve security challenges resulting from a distributed workforce, more BYOD devices, and cloud solutions. This Research Byte summarizes our full RadarView report on the subject.
October, 2020
-
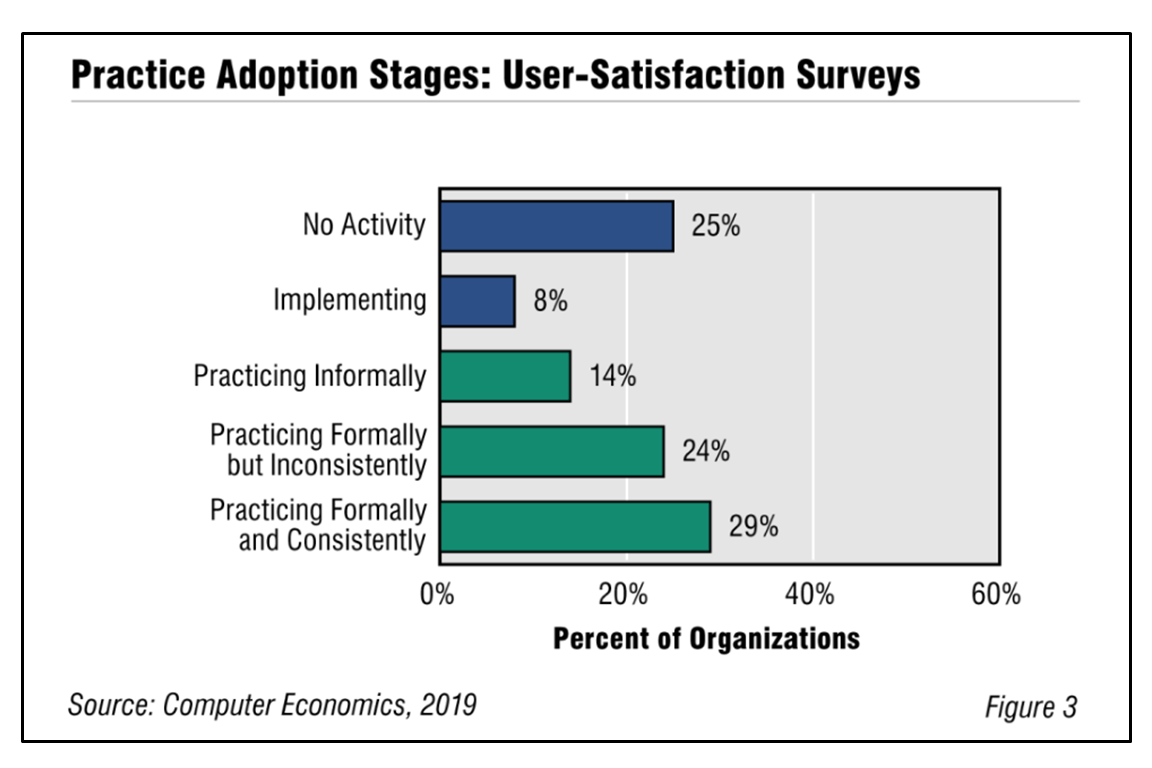
![How Are We Doing? Surveying Users and Reporting IT Performance Metrics Fig3UserSatisfactionPerformance2019 - How Are We Doing? Surveying Users and Reporting IT Performance Metrics]()
How Are We Doing? Surveying Users and Reporting IT Performance Metrics
Two distinct but related IT management best practices-user-satisfaction surveys and IT performance metrics-are either growing slightly or remaining at a consistent level. But in both cases, many companies could use some help in practicing these two disciplines formally and consistently. This Research Byte provides a summary of our full report on user-satisfaction surveys and IT performance metrics adoption and best practices.
July, 2019
-
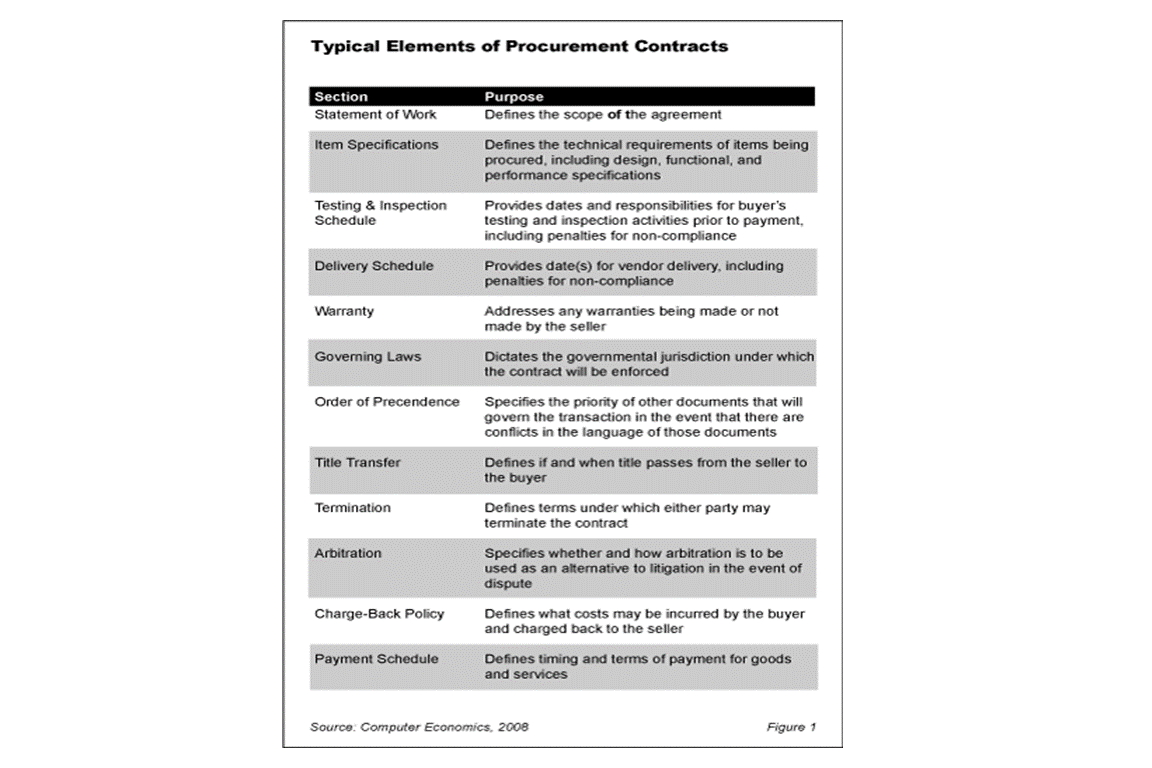
![Understanding IT Procurement Contracts Fig1Procurement - Understanding IT Procurement Contracts]()
Understanding IT Procurement Contracts
Nearly all IT projects require some sort of procurement, whether it is for hardware, software, or services. Therefore, IT project managers need to understand the major element of IT procurement contracts, as outlined in this post.
November, 2008
-
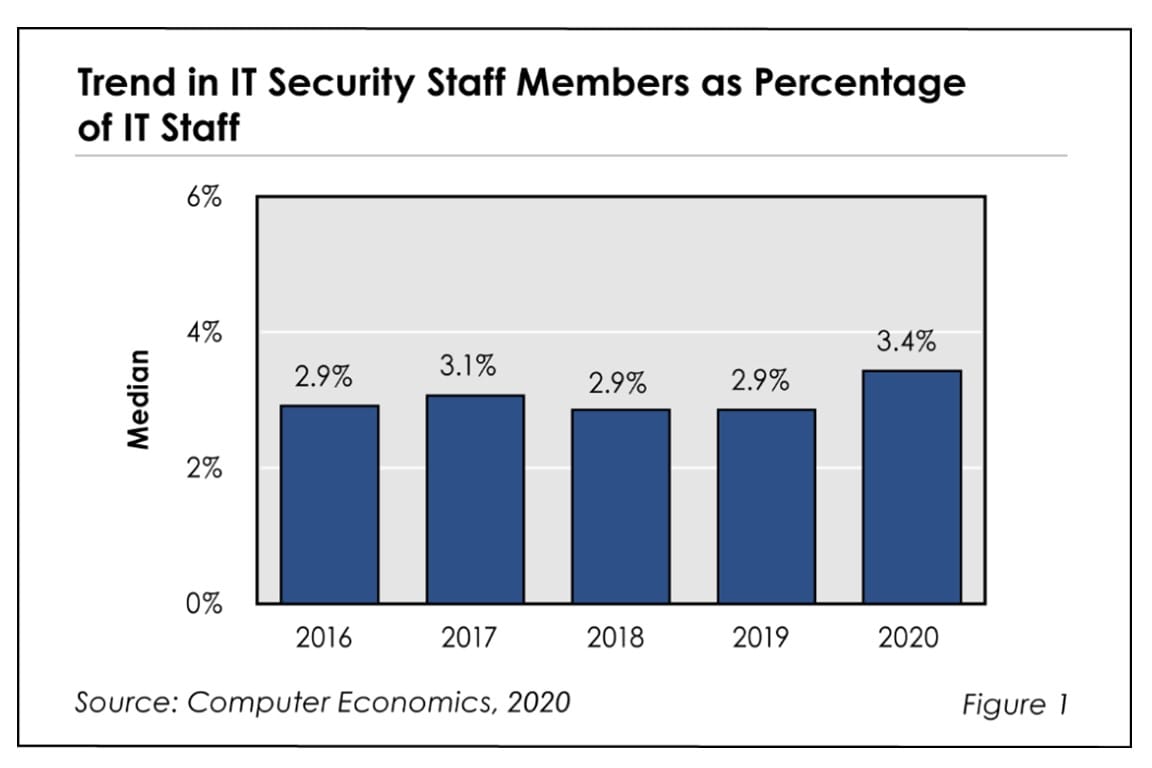
![IT Security Staffing Catching Up with Existential Threats Fig1RBsecuritystaffingratios - IT Security Staffing Catching Up with Existential Threats]()
IT Security Staffing Catching Up with Existential Threats
After years of remaining flat in the face of mounting security threats, IT security head count has finally risen as a percentage of the total IT staff. Until 2020, despite a growing array of threats and rising IT security budgets, IT organizations had not been increasing the size of their security teams and instead focused on technology to fight the problem. This Research Byte looks at the factors behind these trends.
November, 2020
-
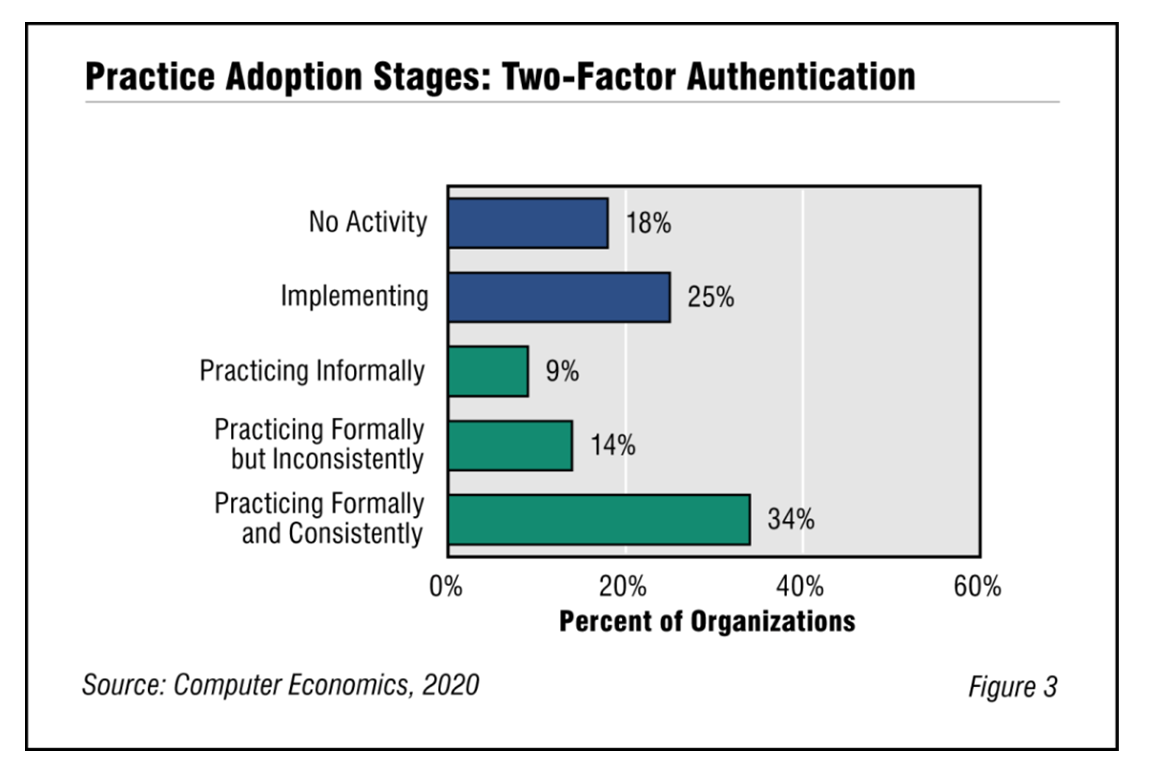
![Nobody Loves Two-Factor Authentication Fig3TwoFactorAdoptionAndBestPractices - Nobody Loves Two-Factor Authentication]()
Nobody Loves Two-Factor Authentication
Two-factor authentication (2FA) is an IT security best practice that provides an extra layer of protection for system access, by asking a user for a second means of identification. It mitigates risk of unauthorized access and yet, despite these benefits, our annual survey of IT management best practices shows that too few companies apply two-factor authentication formally and consistently. This Research Byte explores some reasons for the lukewarm adoption of 2FA.
February, 2020
-
![COVID-19: Enterprise Resilience Is Tested Like Never Before Covid - COVID-19: Enterprise Resilience Is Tested Like Never Before]()
COVID-19: Enterprise Resilience Is Tested Like Never Before
With the ongoing pandemic many stories emerged of resilience, responsiveness, and innovation, as many of us are forced to live in the future. People were asked to act against their nature and shift from a collaborative workplace environment to isolation at home, further blurring the lines between work and life. This led to a need to strengthen the digital muscle hinged around remote-first working, cloud acceleration, smart IT operations, and automated business operations. Infosys seems to have already laid down the digital rail tracks which helped boost revenue and profit, reflecting resilience and adaptability of its business model in this time of crisis.
October, 2020
-
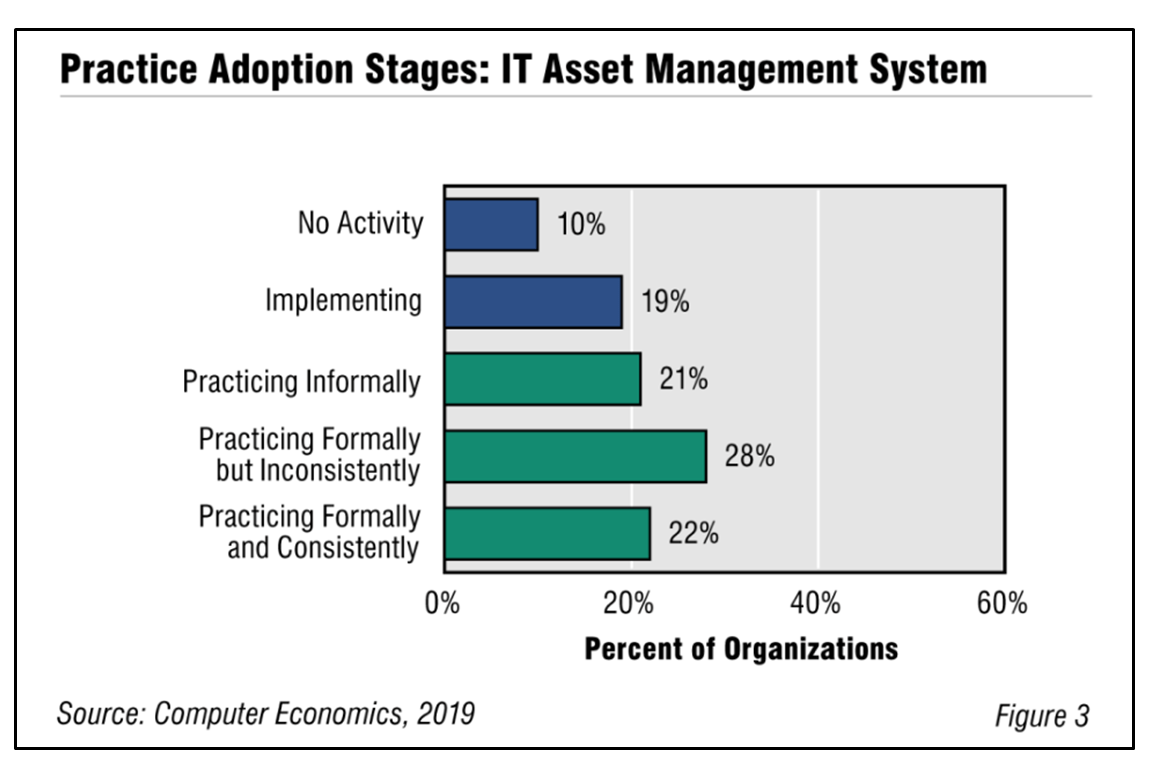
![IT Asset Management Adoption Grows, Despite Complicating Factors Fig3ITAssetManagementBestPractice - IT Asset Management Adoption Grows, Despite Complicating Factors]()
IT Asset Management Adoption Grows, Despite Complicating Factors
For IT organizations, the dream of having all IT assets fully documented and tracked within a formal system remains elusive. While IT organizations have been able to bring certain assets under control, as soon as one area has stabilized, the technology changes. Employee-owned devices and technologies designed to simplify IT asset management such as SaaS keep moving the goal line. This Research Byte provides a summary of our full report on IT asset management adoption and best practices.
August, 2019
-
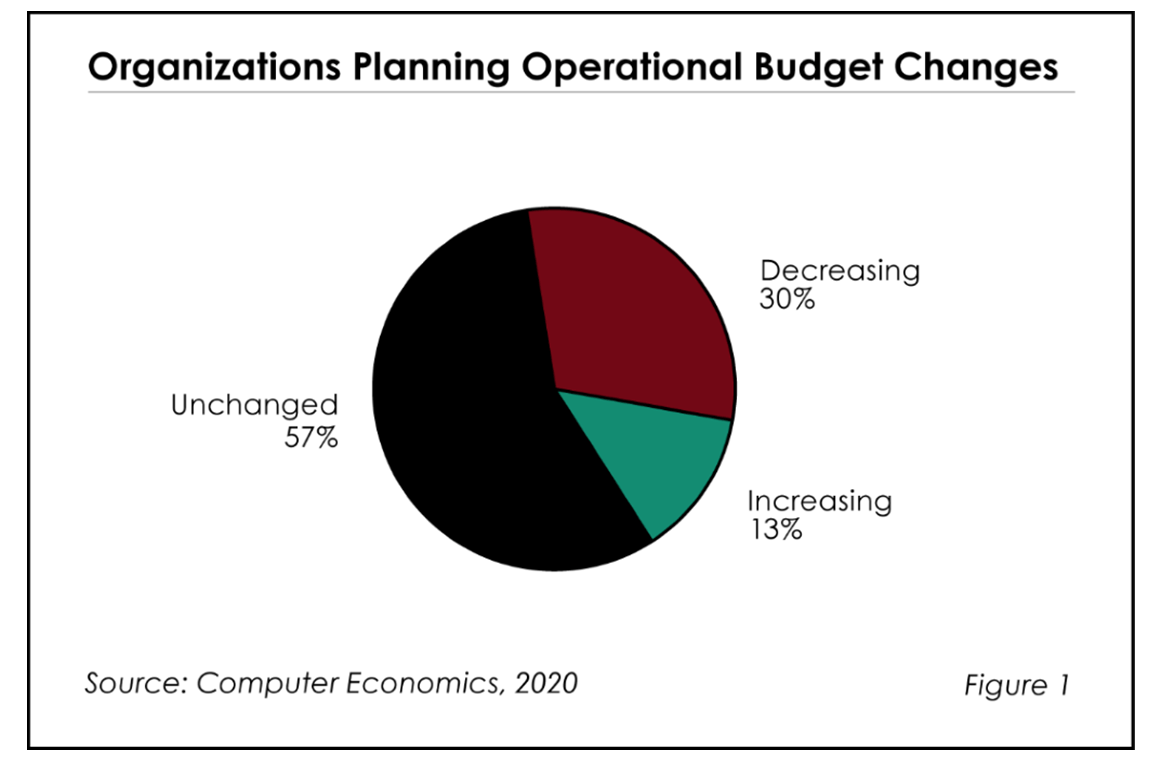
![Coronavirus Impact on IT Budgets Still Coming Fig1ImpactofCOVID19 - Coronavirus Impact on IT Budgets Still Coming]()
Coronavirus Impact on IT Budgets Still Coming
Benchmarking IT spending and staffing is a complicated task in the best of economic conditions. Benchmarking in the middle of a global pandemic and recession is even more difficult, but also more important. As we prepare the launch of the 31st edition of our annual IT Spending and Staffing Benchmarks report, this is the challenge.
July, 2020